AI Moderation Deep Dive: How Spikerz Detects Hate, Spam & Impersonators
AI Moderation: How Spikerz Detects Hate, Spam & Impersonators
Cyberattacks aren't slowing down. According to Check Point, the average number of weekly attacks per organization reached 1,673 last year. That number is honestly alarming, and there’s little indication it will decline anytime soon.
At the same time, businesses are not left without options. Effective protection is available, and advances in technology have made it more accessible than ever.
In this blog post, we'll explore the hidden costs of inadequate social media protection, examine the most dangerous threats targeting businesses online, and show you how AI-powered defense systems like Spikerz detect and neutralize hate, spam, and impersonators before they damage your brand.
An Unprecedented Volume Of Social Media Threats
Businesses today face more social media threats than ever before for three main reasons.
- These attacks are happening more frequently and becoming more advanced.
- Most companies don’t have enough staff to monitor and respond to threats around the clock.
- Small problems can quickly become big disasters. A single fake comment can spread to thousands of people within minutes, or one malicious link can lead to a full account takeover.
The problem has gotten worse as more employees work from home and companies adopt BYOD policies. Hackers now have many more ways to attack your business since your company’s network extends into every employee’s home.
IABs can quickly scan through stolen data to identify potential entry points to your company’s systems. They often bypass security measures like MFA by stealing login cookies found on employees’ personal devices, giving them direct access to your business accounts.
To fight back against these threats, businesses need to expand their security measures to protect all the new ways hackers can get in, including employee access points and home networks. Organizations should also actively search for indications of company-related artifacts being sold on criminal markets to catch potential breaches before they happen.
The Hidden Costs of Inadequate Protection
There has been a massive increase in impersonation attacks due to how easy AI has made it for cybercriminals to create convincing fake personas. Tasks that used to require advanced technical skills and expensive resources can now be accomplished by anyone with access to basic AI tools and a few hours of preparation.
As a result, businesses and individuals face serious consequences that get worse over time and damage their operations in multiple ways.
Account Takeovers
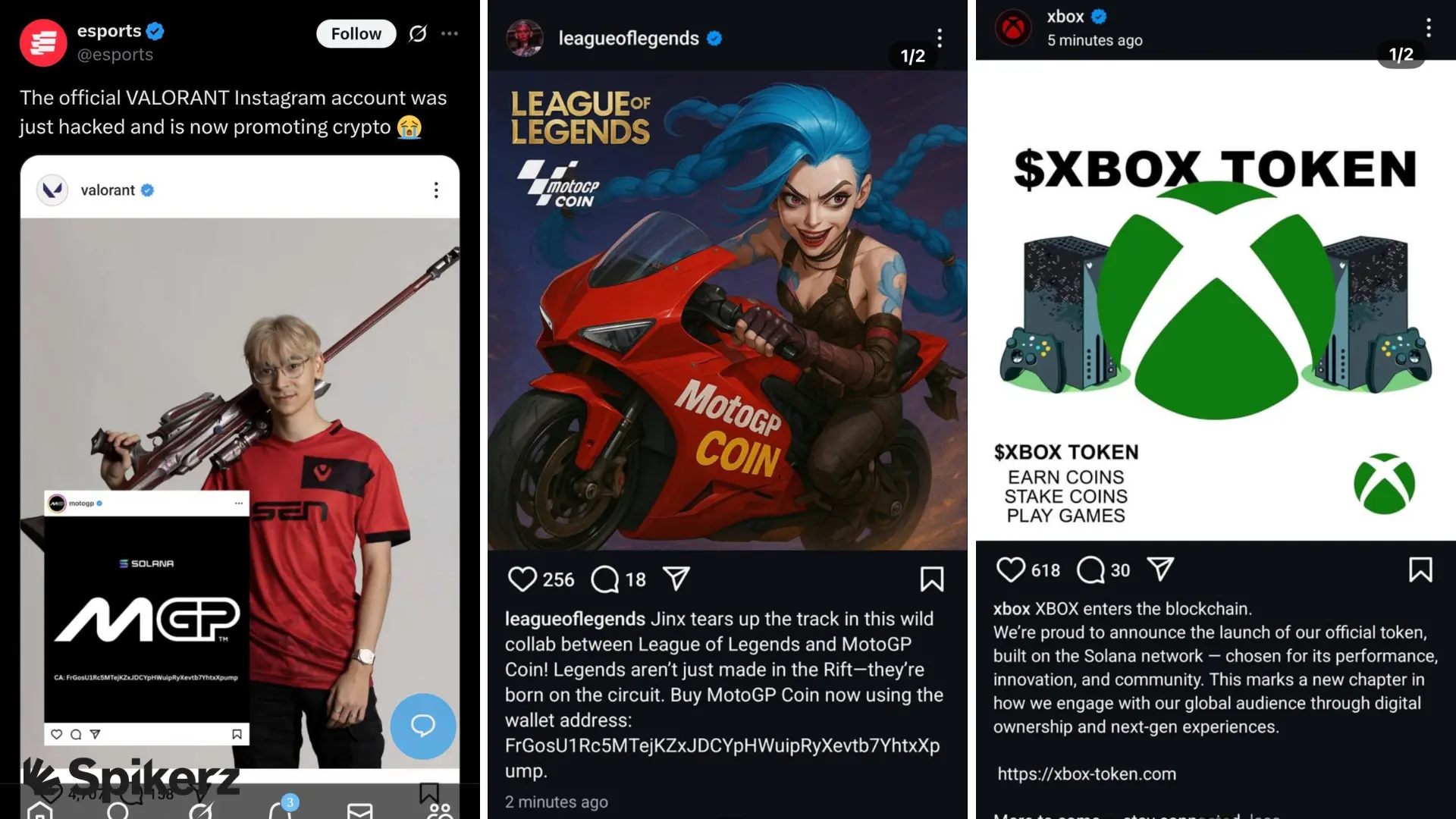
Account takeovers happen when attackers gain unauthorized access into your social media accounts using malware or social engineering tactics like phishing. Once inside, they control your brand's voice and can reach all your followers.
These attacks have become much more dangerous because they’re now easier to pull off and harder to stop.
Once hackers take over an account, the consequences grow quickly. Businesses face financial losses, reputation damage, and disrupted operations. And individual users often become victims of fraud. Since malicious posts can go viral in minutes, and there are now so many ways for hackers to attack, these incidents can cause massive harm quickly.
Recent cases show just how serious this problem really is. The UEFA's Instagram account was hijacked to push a cryptocurrency meme coin scam. And Riot Games had both its League of Legends and VALORANT Instagram accounts taken over to promote similar scams to their fans.
Even major media outlets have been targeted. The New York Post's X account was compromised and used to lure victims into a fake podcast setup that had the potential to turn into a physical crime.
Disinformation Campaigns
Disinformation campaigns are deliberate efforts to spread false or misleading content that looks authentic enough to manipulate public opinion on a large scale. They often target large organizations and public figures, but any business that gains visibility can be a target.
What makes them dangerous is the role of generative AI, which allows attackers to create convincing articles, deepfake videos, and synthetic audio that can mirror your brand's voice and identity with alarming accuracy. When these campaigns succeed, they change public opinion, diminish trust, and trigger financial and reputational fallout that lasts long after the initial wave of disinformation has passed.
What’s worse is that the speed and reach of social media make these attacks more destructive. Content can spread globally within minutes before organizations have any chance to respond or fight back. By then, it’s almost impossible to stop.
A clear example of how dangerous these campaigns are is the European election interference campaign. Russian operatives built fake news outlets filled with AI-generated articles and deepfake videos that were nearly indistinguishable from legitimate reporting. This content successfully reached millions of people across multiple countries, shaping narratives and creating confusion on a massive scale.
In short, disinformation campaigns are so dangerous because once they take hold, they are difficult to contain and their effects persist even after the truth comes out. They undermine credibility, weaken relationships with audiences, and create lasting vulnerabilities that can be exploited again in the future.
Phishing Campaigns
Phishing campaigns are attacks where cybercriminals trick people into clicking links, opening attachments, or sharing sensitive information through emails, messages, or social media posts.
They are the most common attack vector in cybersecurity, and artificial intelligence is making them more difficult to spot. Attackers no longer only rely on poorly written emails. Instead, they use AI to improve their language, mimic brand voices, and personalize messages that look real enough to fool both people and security tools.
According to SlashNext's Phishing Intelligence Report, phishing emails grew by more than 200% in the second half of 2024 alone, showing how these campaigns continue to expand in scale and sophistication.
However, the real danger lies in what happens next. The impact of phishing isn’t limited to a single compromised account or stolen password. Once attackers get in, they can spread through corporate systems, steal sensitive data, and create long-term vulnerabilities that are difficult to detect.
The Sony Pictures breach is a clear example of how disastrous these attacks can be. Attackers disguised themselves as colleagues of senior executives, and their malicious attachments led to the theft of more than 100 terabytes of data and losses exceeding 100 million dollars.
In essence, phishing campaigns are dangerous because they exploit the natural trust people place in familiar communication channels. They bypass technical safeguards, cause financial and reputational harm, and open doors for larger attacks.
Ransomware Attacks
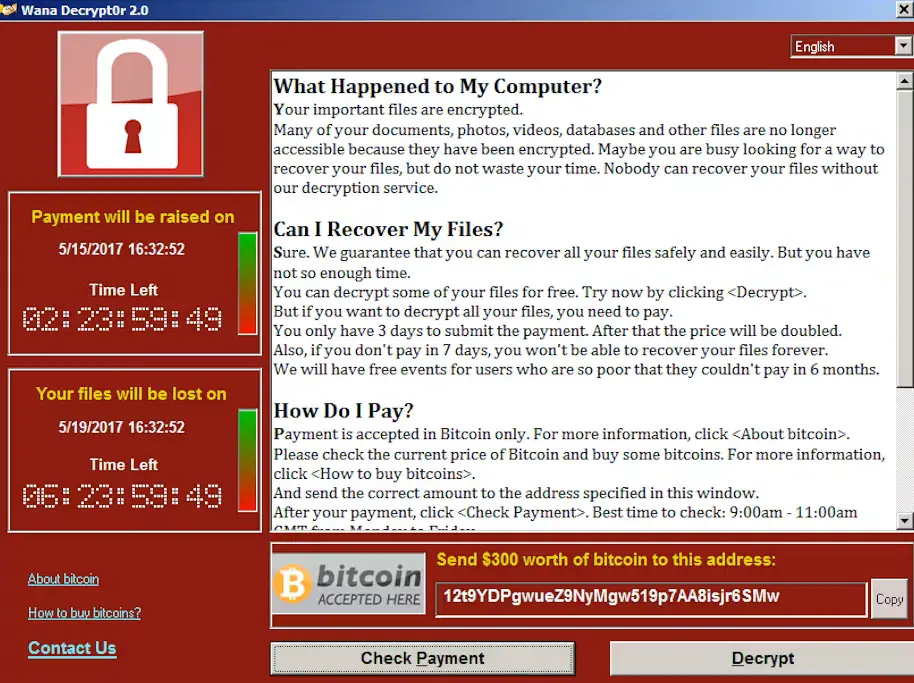
Ransomware attacks happen when criminals take control of your accounts or systems and demand payment to give you back access. Lately, these attacks are using the help of AI-assisted social engineering. Attackers create highly convincing phishing messages on social media or email to trick employees into giving them a foothold in corporate systems.
Once an account is compromised, attackers change the email and password, locking the organization out and demanding ransom (often in the form of cryptocurrency). They often threaten to delete data or damage the company's reputation if their demands aren't met.
Unfortunately, the rate at which these attacks happen is increasing at an alarming rate. The BlackFog State of Ransomware 2025 report recorded 278 disclosed attacks in the first quarter alone, a 45% increase from the previous year.
Ransomware is particularly dangerous because it hits companies in multiple ways at once. It stops business operations immediately, costs a lot of money, and damages the company’s reputation. On the flip side, while recovering from an attack is expensive and doesn’t always work, preventing attacks through employee training and social media monitoring tools costs much less and works much better.
Most Employees Can't Identify Deepfakes
Deepfakes are AI-generated images, audio, or videos designed to look and sound like real people. They are more often than not nearly impossible to distinguish from authentic content.
In the past, creating deepfakes required advanced technical expertise and expensive software. But now they can be done with widely available tools and basic knowledge, lowering the barrier for attackers to create highly convincing fakes.
The biggest problem is that people can’t tell when they’re being fooled. Research from iProov shows that while most people (around 71%) are aware of deepfakes, only 0.1% can consistently identify them. If employees receive a phishing email or social media message featuring a deepfake of a trusted leader or colleague, they're likely to believe it's real. The psychological weight of hearing and seeing someone they recognize makes these attacks hard to resist.
If employees don't recognize deepfakes, the consequences are often big. Criminals can trick staff into transferring funds, exposing sensitive data, or giving up access to business accounts, creating lasting damage, especially financial damage. That’s precisely why training employees to detect and question deepfake content is essential for protecting your organization.
Whaling Attacks
Whaling attacks are a targeted form of phishing that focus on high-level executives or other individuals with authority over sensitive information and large financial transactions.
They're called whaling because hackers go after the biggest "fish" in a company, like CEOs, CFOs, or department heads who can make important decisions without needing additional approval. Unlike broad phishing attempts, they're highly personalized, with attackers investing time to research their targets and craft messages that look legitimate.
What makes them so dangerous is how much work hackers put into them. They mimic the writing style of trusted contacts, reference real business conversations, and sometimes even hijack legitimate email accounts to make their messages look completely authentic. The use of artificial intelligence makes this even more convincing, allowing attackers to replicate tone, phrasing, and even voices or video appearances that executives and employees are used to seeing.
Unfortunately, the consequences of successful attacks can be huge. For example, Snapchat's payroll team once handed over employee data after an email that appeared to come from CEO Evan Spiegel. And Natura & Co lost $14.6 million in 2021 when attackers impersonated an executive and tricked the finance team into transferring funds.
Whaling is extremely effective because it exploits trust at the very top of organizations. When requests come from leaders, employees act quickly, which makes the attacks one of the most damaging threats businesses face today.
How Spikerz's Defense System Detects Hate, Spam And Impersonators
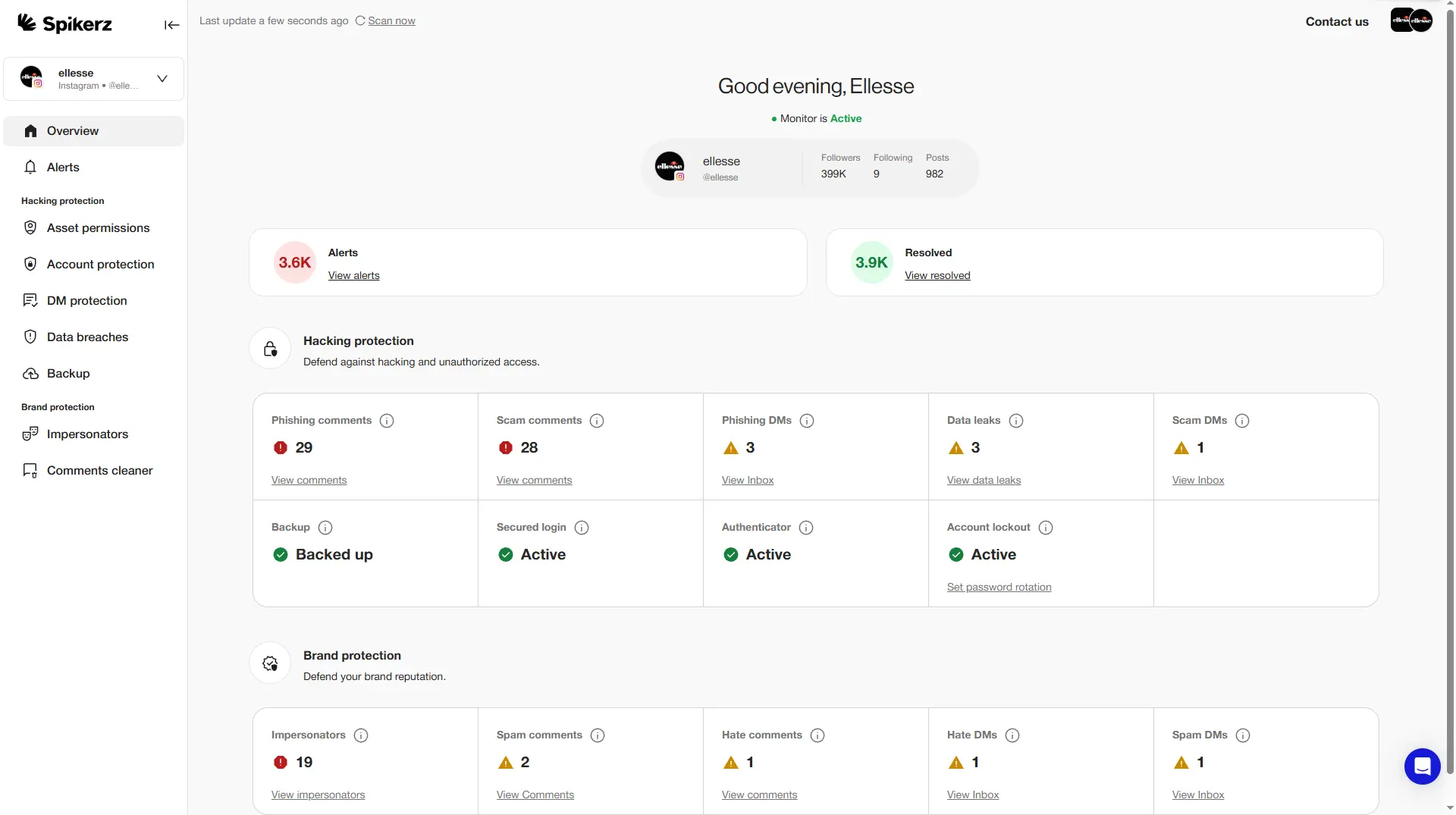
Spikerz is highly effective due to going beyond simple keyword matching to understand intent and cultural context. Our AI analyzes patterns, behaviors, and content in real-time, providing protection that adapts to evolving threats targeting your social media presence.
Phishing Messages
Spikerz actively scans and analyzes your direct messages and comments to spot red flags like phishing attempts, spam links, or suspicious bot activity. It uses AI-powered detection to recognize patterns commonly used in scams and automated attacks.
When Spikerz identifies a threat, it immediately alerts you and either blocks, removes, or flags the harmful content depending on your settings. If you choose to have Spikerz do everything for you, you’ll stay protected without needing to manually filter through everything yourself.
Spam Comments
Spikerz monitors and analyzes comments on your posts to detect spam, including repetitive promotions, links, or bot-generated messages. When it finds something suspicious, it can automatically block, hide, or flag the comment so your feed stays clean and professional.
You can set up custom keywords and filters to fine-tune detection. You decide which words, phrases, or types of comments should be flagged or removed. This way, you'll not just rely on automated detection, you'll shape the protection to fit your brand and audience.
Impersonation Attempts
Spikerz continuously scans social media platforms to detect when brand assets like your logo, name, or content are being misused by impersonators or unauthorized accounts.
When it finds a violation, it alerts you right away and takes action by helping you report the content or account to the platform. This helps protect your brand's reputation, prevent fraud, and ensure that your audience only engages with your official business channels.
Account Takeovers
Spikerz protects your social media accounts from takeovers by monitoring for unusual login attempts, suspicious activity, and signs that someone is trying to break into your profile.
If it detects a threat, it sends you an instant alert and triggers protective actions before any damage is done. Hackers are stopped in their tracks, and you keep full control of your accounts without the risk of losing access or having your brand misused.
If you're tired of worrying about hackers, impersonators, and spam destroying everything you've built online, it's time to take action. Prevention costs a fraction of what recovery does, so create a Spikerz account right now to have the peace of mind that comes from knowing your social media presence is protected by a system that never sleeps. Don't wait until you're the next victim to realize the value of proper protection.
Conclusion
The threats we covered (account takeovers, disinformation campaigns, phishing attacks, ransomware, deepfakes, and whaling) are just the tip of the iceberg. Every day brings new attack methods, more sophisticated AI tools for criminals, and fresh vulnerabilities to exploit.
But here's the thing: you don't have to face these threats alone. Defense systems like Spikerz work around the clock to detect and neutralize dangers before they reach your brand.
The choice is simple. You can continue hoping your current security measures are enough, or you can take decisive action to protect what you've built.
Remember, prevention is always less expensive than recovery. This is true both financially and in terms of your brand's reputation. Start your protection today and transform social media security from a constant worry into a competitive advantage.

.webp)

