Close the security gap in your social media channels
Protect against phishing, scams and account takeovers with a solution that’s easy for security teams to implement and use.
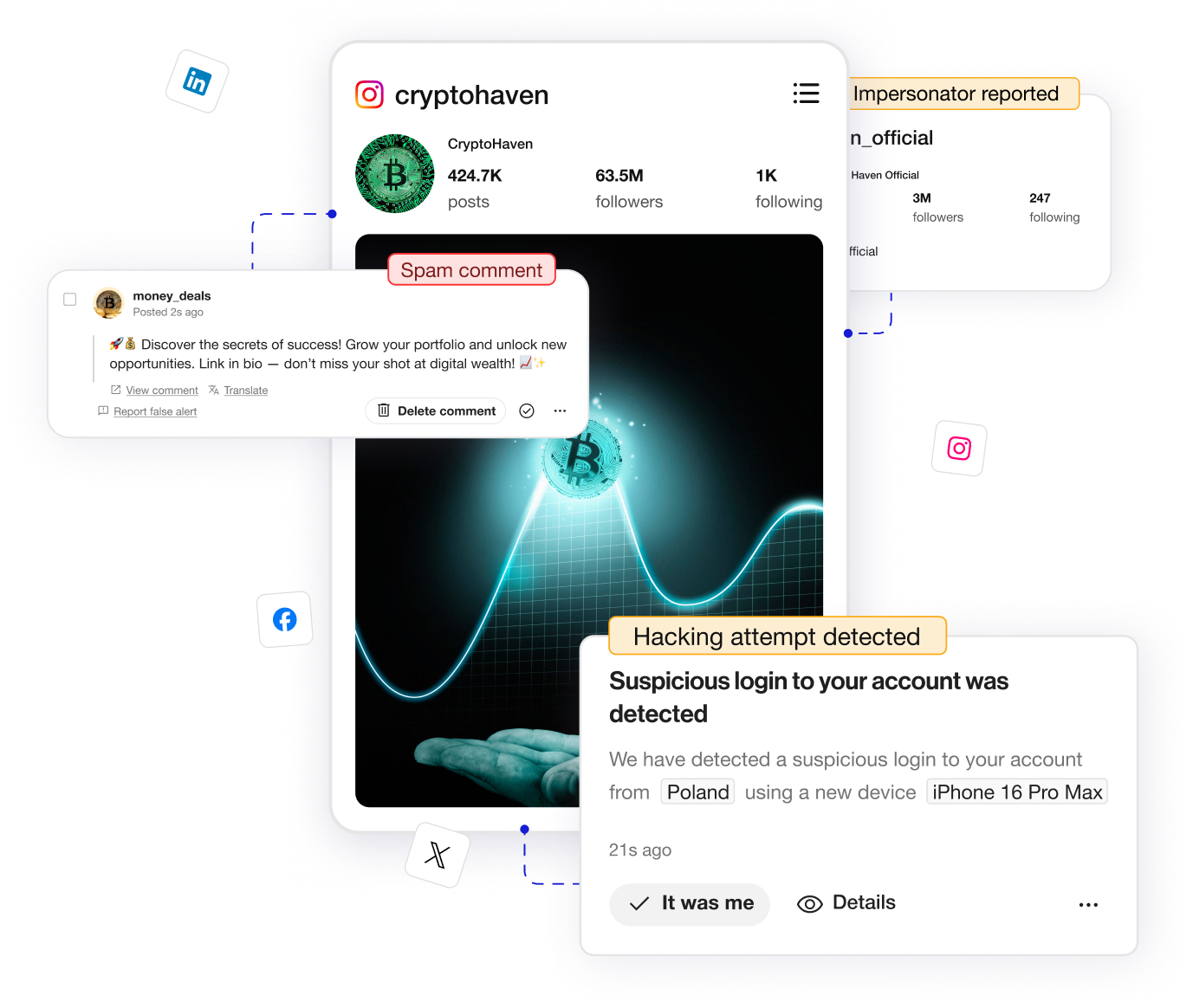















As your brand grows, so do the security risks.
Give your social media accounts enterprise-grade security
Account Takeover Protection
Prevent unauthorized logins with behavioral monitoring, risk-based authentication, and real-time threat blocking.
Immediate Permission Revocation
Prevent unauthorized logins and stop hackers with behavioral monitoring and real-time threat response.
Centralized Access Control
Unify all social media logins into a single secured system to enforce least-privilege access.
Enforce Security Policies
Apply SSO, MFA, and role-based access through IdP integration to align with corporate security standards.
Comprehensive Audit Logging
Record every login, permission change, and access event in immutable logs for compliance and forensics.
Protect your social media accounts
Join over 5,000 brands and enterprises already trusting Spikerz to secure their accounts, moderate comments, and identify impersonators.









Designed for modern social media teams
You don’t need to be an IT expert. Spikerz integrates seamlessly with your social stack and puts full control in the hands of your social team. Just connect your social accounts, set your brand guidelines, and let AI handle the rest.
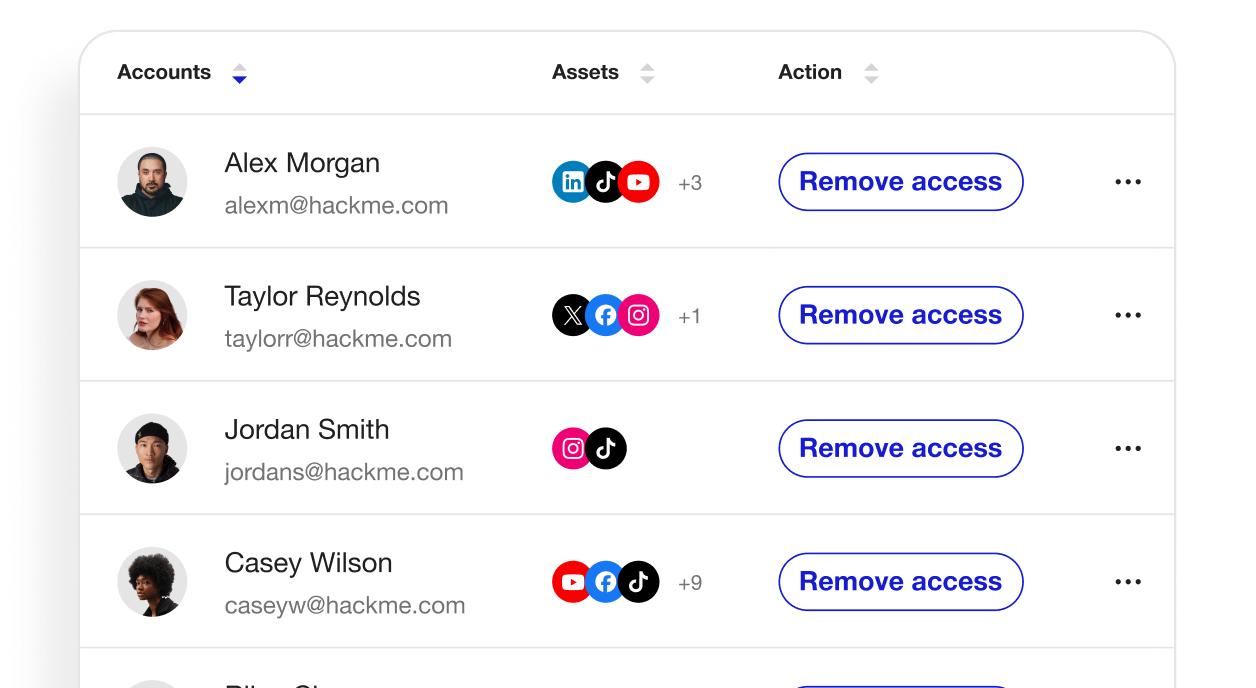
Manage all social account access with full visibility, governance and audit trails
Enhance 2FA with centralized token management, not tied to personal devices
Instantly offboard and revoke access from former employees and vendors across all platforms
Trusted by brands who take security seriously
Spikerz has been tried and tested by digital-native, fast-growing companies who need agility and control.
Ready to protect your brand?
Your marketing team moves fast. Your security team needs full oversight. Spikerz delivers both, protecting paid and organic social channels with enterprise-grade controls that don’t slow business down.
.webp)
Enter your work email address



.webp)

