What Is Account Takeover (ATO)? How Do You Prevent It?
What Is Account Takeover (ATO)? How Do You Prevent It?
Hackers take over accounts for all sorts of reasons: scamming users, distributing ransomware, and spreading political messages. And unfortunately, these attacks are more prevalent than ever. Over the past couple of years, we've watched social media hacks explode. Every single month brings news of another major security breach that damages brand reputations and costs users millions.
The most recent high-profile incidents show no one is safe. From Samsung and Nasdaq to the NBA and NASCAR, even the biggest organizations with massive security budgets fall victim to account takeovers.
In this blog post, we'll cover what account takeovers are, how they happen, who gets targeted, and the practical steps you can take to protect your organization from these attacks.
What is Account Takeover (ATO)?
Account Takeover (ATO) is an attack where cybercriminals take ownership of online accounts using different methods like stolen passwords and usernames, phishing, and malware.
However, another common method they use is to purchase a list of credentials in the dark web that were most likely obtained from social engineering, data breaches, or phishing attacks.
Attackers test these credentials using bots across sites like finance, retail, eCommerce, and social media to find valid logins. Once inside, they can steal information, make fraudulent transactions, hold them for ransom, or use the account for further attacks.
What Types Of Organizations Do ATO Attacks Target?
Financial institutions used to be the main focus for account takeover (ATO) attacks. But today, any organization with online accounts is at risk.
Attackers now go after diverse sectors, depending on what they can get out of it. For example:
- Financial services and eCommerce are still high on the hit list. Hackers hijack accounts to make fraudulent purchases using stored payment details or steal cryptocurrency.
- Public sector, healthcare, and education are frequently targeted for their valuable personally identifiable information (PII), which can be used for identity theft, insurance fraud, or credit fraud.
- Any organization with high value user accounts risks having that data stolen and sold on dark markets, or used as entry points for ransomware.
How Account Takeovers Happen
Understanding how account takeovers work is relatively simple but it can get complicated depending on how it's done. Here are the most common ways hackers use to take over accounts:
1) Theft of Login Credentials via a Data Breach
Stealing login credentials via data breaches typically is done through exploiting vulnerabilities in systems or human behavior to gain unauthorized access to databases where sensitive user information like usernames, email addresses and passwords is stored.
Data breaches are a huge problem. In 2022 alone, roughly 24 billion passwords were exposed in data breaches. And according to Statista, in the third quarter of 2024, 422.61 million data records were leaked in data breaches, impacting millions of individuals worldwide.
Here's how these types of attacks are typically done: Hackers first identify a target like a website, application, or service with user accounts. They then use techniques like:
- Exploiting vulnerabilities in web applications (SQL injection, broken authentication, etc.)
- Compromising servers through unpatched software or misconfigurations
- Social engineering attacks against employees with database access
- Insider threats from malicious employees
- Third-party vendor compromises that affect connected systems
Once inside, the attacker tries to access the database storing user credentials and if the data is unencrypted or poorly encrypted, it's an easy win.
The security of this data depends heavily on how it was stored:
- Plaintext passwords (worst case) are immediately usable.
- Hashed passwords require cracking but are often vulnerable to rainbow table attacks or brute force.
- Properly salted and hashed passwords are much more difficult to crack but not impossible.
After that, the attacker copies the login data and transfers it to a remote server they control. If passwords are hashed, attackers use dictionary attacks, rainbow tables or brute force attacks.
Stolen credentials are then used directly (if the breach is recent and the user hasn't changed their password), tested on other services (credential stuffing), and often sold on the dark web.
2) Brute Force Credential Cracking
.webp)
Brute force credential cracking is a trial-and-error hacking method used to crack passwords, login credentials, and encryption keys. The name "brute force" comes from attackers using excessively forceful attempts to gain access to user accounts.
Despite its simplicity, it remains a significant security threat, accounting for 5% of all data breaches, with 80% of hacking-related breaches involving either brute force attacks or compromised credentials.
The attack process begins when: The attacker gets a list of usernames or emails from a breach or scraped data. They then use a script or bot to systematically attempt passwords for each account.
There are different variations to do it like simple brute force (try all possible character combinations), dictionary attacks (list of common or likely passwords), and credential stuffing (use known username/password pairs from other breaches on different sites).
3) Phishing for Login Information
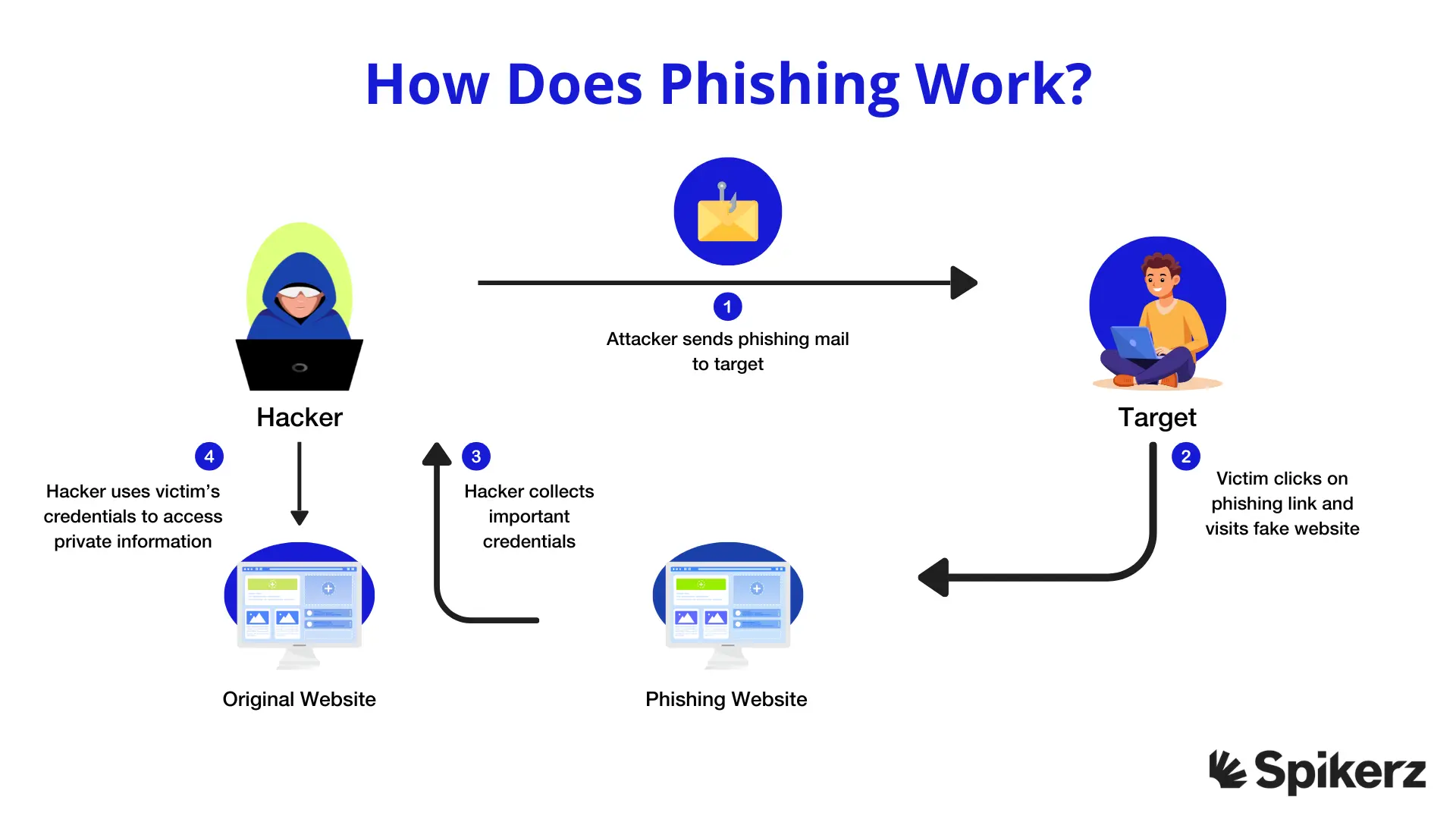
Phishing is the biggest cybersecurity threat there is, with IBM's Cost of a Data Breach report identifying it as the most common breach vector, accounting for 15% of all incidents and costing organizations an average of $4.88 million per breach.
What's worse is that the scale of this threat continues to grow, with nearly 9 million phishing attacks detected worldwide in 2023 and almost one million unique phishing sites appearing in just the first quarter of 2024.
The good news is that attacks typically unfold in a predictable way, so we can easily identify them when we know what to look for:
- First, a hacker pretends to be someone the victim trusts like a colleague, boss or authority figure and sends a fake email or message with a link to a bogus login page.
- The page looks like the real one (Google, Microsoft, Facebook, Instagram, etc.) The victim enters their username and passwords and are sent directly to the attacker.
- The attacker can then use the credentials, sell them, or launch further attacks like business email compromise or account takeover.
4) Data Theft via Viruses and Malware
.webp)
Malware is another prevalent method for stealing login credentials. This method installs malicious software like keyloggers, spyware, Trojans, and remote access tools to secretly steal login credentials and other sensitive data from a user's device.
According to recent data, malware was involved in 40% of data breaches in 2023, representing a 30% increase from the previous year, while CyberArrow reported 5.5 billion malware attacks in 2022 alone.
The infection process typically begins when users unknowingly download or install malicious software. This happens when you inadvertently do something that triggers the malware to be downloaded.
Common actions include clicking on an infected link in an email or visiting a malicious website. In other cases, hackers spread malware through peer-to-peer-file-sharing services and free software download bundles like embedding malicious computer code in a popular torrent or download.
Another technique is to load malware onto the firmware of a USB stick or flash drive. Then, when the USB stick is connected to another device, the malware will likely remain undetected because it's loaded onto the device's internal hardware.
Once the malware has been installed, it operates silently in the background, capturing keystrokes, monitoring user activity, and collecting login credentials and other sensitive information.
This data is then transmitted back to the attackers, who can use it for account takeovers, identity theft, or sell it on the dark web for profit.
5) Man in the Middle (MitM) Attacks
%20Attack.webp)
A Man-in-the-Middle attack happens when a hacker secretly intercepts and possibly alters communication between two parties (e.g., a user and a website), often to steal login credentials, session cookies, or sensitive data.
These attacks have contributed to the growing data breach crisis, with over 35.9 billion known breaches recorded globally as of May 2024, according to Securus Communications.
The attack typically unfolds when users connect to compromised or unsecured networks, such as public Wi-Fi hotspots.
In a common scenario, when you attempt to access your bank's website through a shared network, an attacker on the same network can redirect your traffic through their device instead of sending it directly to the bank's server. This redirection happens through network manipulation techniques that trick your device into routing data through the attacker's system.
Once positioned in this digital 'middle ground,' the attacker gains visibility into all data passing between you and the legitimate service. They can read your login credentials, modify transaction details, or capture session tokens that allow them to impersonate you later.
Research indicates that weak encryption practices were responsible for nearly 70% of successful MitM attacks in the US in 2024, highlighting the importance of strong security protocols and avoiding unsecured networks for sensitive activities.
How Organizations Can Protect Against Account Takeovers
Even though there are many attack vectors we need to cover, there are effective methods of protection we can use to cover all the bases. Here are some of the most effective ways to protect your social media presence.
1) Use Strong, Complex Passwords
Create strong, complex passwords and avoid reusing them to reduce the risk of unauthorized access to accounts and business systems and software. Many cyberattacks (like brute force attacks) rely on weak or reused passwords, having complex passwords make them much harder and less likely to succeed.
2) Enable Multi-Factor Authentication
Multi-Factor Authentication (MFA) is one of the simplest and most effective ways to secure business accounts. It requires users to verify their identity with more than just a password (like a code from an authentication app, a text message, or a biometric scan).
Here's why MFA matters for your business:
- Even if a password is compromised, MFA adds multi-layered defense that prevents intruders from gaining access.
- MFA is perfect for defending against login theft via data breaches, brute force attacks, and malware that steals login credentials.
- Employees don't always follow strong password practices, MFA helps make up for that.
- Many data protection regulations and insurance policies now require MFA to be in place.
- While 2FA (two-factor authentication) is technically a subset of MFA (multi-factor authentication), it provides an effective solution for managing shared team accounts. If you implement team-based 2FA, your organization will be able to control which personnel receive access to login codes for sensitive accounts. There are different platforms that allow you to do just that. For example, Spikerz offers team-based 2FA that allows companies to manage access on a centralized dashboard. This ensures only authorized team members can access sensitive data while preventing unauthorized logins to shared social media accounts.
3) Train Your Employees To Recognize Phishing Attacks
Phishing continues to be the biggest online threat to businesses worldwide. Cybercriminals often bypass technical security via targeting employees directly through deceptive messages.
Here's why employee training is a must:
- Employees who can identify and report phishing attempts help stop threats before they cause any damage.
- Most data breaches begin with a successful phishing email, training employees significantly reduces this risk.
- Training is perfect for helping employees recognize phishing direct messages, SMS messages (smishing), and deceptive comments sent through social media platforms.
- Preventing an attack is far less expensive and disruptive than dealing with the consequences.
- Regular training promotes awareness and helps make security a shared responsibility across the company.
4) Use Account Takeover Protection To Monitor Your Accounts

Account takeover (ATO) attacks are a growing threat to businesses, especially the ones with a strong online presence. For that reason, companies should do everything they can to ensure their accounts are protected.
Here's why using account takeover protection software is essential:
- It helps identify suspicious activity like unexpected logins, location changes, or device swaps.
- If a cyberattack manages to bypass other defenses, ATO protection is your safety net. It's perfect for identifying and stopping account breaches before they cause damage.
- Instead of waiting for human intervention, good ATO tools take immediate action to secure compromised accounts. Take Spikerz as an example. If a hacker successfully breaches one of your social media accounts, Spikerz acts instantly and it kicks the intruder out, changes your passwords, and alerts you. This rapid response stops disasters before they spread, protecting your business from disruptions, brand reputation hits, and loss of customer trust.
- Social media accounts are public-facing and often targeted by attackers. A breach here can damage your reputation quickly, ATO software ensures you stay in control.
5) Use Antivirus Software To Protect Local Devices
Antivirus software is fundamental for any business that relies on computers, laptops, and local networks. It actively defends your devices from numerous threats that can compromise data, disrupt operations, or open the door to bigger attacks.
Here's why antivirus software is a must-have for businesses:
- It's perfect for protecting against all types of malware like viruses, ransomware, spyware, trojans, and more.
- Some antivirus solutions are advanced and help detect and block suspicious network activity, which reduces the risk of MitM attacks (hackers intercept data between your device and the web).
- Every endpoint is a potential entry point for attackers so antivirus software ensures employee devices (whether in-office or remote) are monitored and protected everyday, all day.
- Infected devices affect productivity or can lead to permanent data corruption, antivirus software catches threats early and minimizes disruption.
- Many data protection standards need antivirus software to be installed and actively maintained across all company devices.
Conclusion
Account takeovers are one of the most serious threats facing businesses online. The attacks we've explored, from data breaches and brute force cracking to phishing and malware, show just how many ways hackers can compromise your accounts. With 24 billion passwords exposed in breaches and phishing attacks costing organizations millions, the stakes have never been higher.
But here's what matters: you're not defenseless. If you implement what we share with you today, you’ll create multiple layers of defense that make your accounts significantly harder to breach. The key is taking action before an attack happens, not after.
Your social media accounts and online presence are too valuable to leave unprotected. Start implementing these security measures now! When it comes to account takeovers, prevention isn't just better than cure; it's your only real defense.



