What Is Online Impersonation? And How To Prevent It
What Is Online Impersonation? And How To Prevent It
Each day, hundreds of businesses fall victim to online impersonation—criminals creating fake websites, social media profiles, and mobile apps that mimic legitimate brands to scam unsuspecting customers. These attacks damage your reputation, steal your revenue, and erode trust with your audience.
With impersonation now accounting for 45% of all social media cybersecurity threats, protecting your digital identity isn't optional—it's essential for survival.
In this guide, we'll explore what online impersonation is, examine real-world examples, discuss its legal implications, and share effective prevention strategies to keep your brand safe.
What Is Online Impersonation?
Online impersonation happens when someone uses an identity other than their own for malicious purposes. The primary goal of impersonation is to obtain money, steal personal information, spread misinformation, or manipulate situations. These attacks range from creating fake social media profiles to developing sophisticated clone websites that mirror legitimate businesses.
Impersonators target both individuals and businesses. On an individual level, they might contact friends and family requesting money, open fraudulent crowdfunding accounts, or take out loans in someone else's name. For businesses, impersonators damage reputation by conducting scams under the company's name.

According to Statista, impersonation was the leading cybersecurity threat on social media in Q4 2023, accounting for 45% of reported incidents. These attacks happen across all platforms, including Instagram, X, Facebook, dating websites, online forums, email, and review platforms.
Examples Of Online Impersonation
Online impersonation comes in various forms, each targeting different aspects of your digital presence. Understanding these attack vectors helps you recognize and prevent them before they damage your brand. Here are the most common types you need to watch for:
Website Impersonation
Website impersonation, also known as website spoofing, involves creating lookalike websites that trick customers into purchasing counterfeit products or revealing personal and financial information. These fake sites damage businesses by lowering search visibility, defiling reputation, and directly impacting revenue.
Impersonators use similar domain names, branding elements, and design features to create convincing duplicates of legitimate websites. Common tactics include using domain names with slight misspellings (like "faceboook.com" instead of "facebook.com") or copying entire website structures and hosting them under different domains.

The biggest issue is that this threat continues to grow—in the third quarter of 2024, security researchers detected over 932,000 unique phishing sites worldwide, showing an increase from the previous quarter.
Social Media Impersonation
Social media impersonation involves creating fake profiles or pages that closely resemble genuine accounts. This form of digital identity theft uses the name, image, and identifying elements of a person, company, or organization for fraudulent purposes.
This type of impersonation differs from legitimate fan accounts, parodies, or information pages. It specifically refers to accounts created with intent to deceive, occurring across platforms like X, Instagram, Facebook, and LinkedIn.
Celebrity impersonation has become particularly prevalent, with scammers posing as famous people to trick fans into sharing personal information or sending money. These scams typically involve fake prize claims, charity donation requests, romance scams, or other financial schemes.
The consequences can be devastating. In a recent case, a 67-year-old woman lost her life savings to a scammer impersonating actor Keanu Reeves. The scam began when she connected with someone claiming to be Reeves, who asked for a $500 gift card to "prove" she wasn't interested in his fame and fortune.
Mobile Apps
Mobile app impersonation happens when cybercriminals create counterfeit applications that mimic legitimate apps. Fake apps aim to steal passwords, capture financial information, make unauthorized purchases, or install malware.
What attackers do is replicate the design, logo, and user interface of legitimate apps to make their counterfeits appear authentic.
The biggest issue is that the damage they cause extends beyond individual users—fake apps erode trust in legitimate applications and app stores, harming the entire app economy and damaging the reputation of original app creators.
This threat is growing rapidly. In the second quarter of 2023, smartphone users in North America encountered around 484,500 phishing and malicious attempts, making it the region with the highest number of incidents. Between January 2022 and February 2023, mobile finance app frauds worldwide reached an estimated value of over 2.64 billion U.S. dollars.
Executive Impersonation
Executive impersonation targets high-ranking company officials like CEOs, CFOs, and other corporate leaders. Scammers create fake profiles that mimic the executive's appearance, communication style, and professional background to appear legitimate.
These attacks exploit organizational hierarchy and the tendency to quickly comply with requests from leadership. Impersonators contact employees requesting urgent wire transfers or sensitive information, approach business partners to redirect payments, manipulate stock prices, extract corporate data, or build relationships with industry leaders for network access.
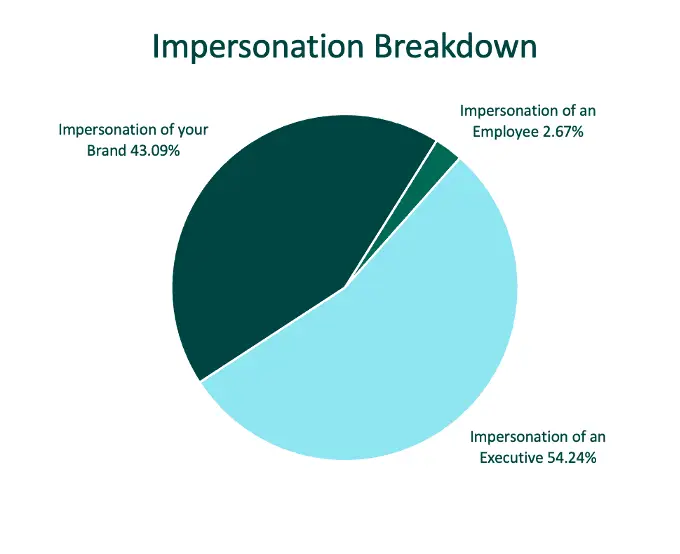
Executive impersonation has grown substantially, with accounts pretending to belong to them climbing to more than 54% of total impersonation volume, surpassing even brand attacks.
Is Online Impersonation Illegal?
Online impersonation exists in a complex legal landscape. While not inherently illegal in all contexts, it often leads to criminal charges or civil lawsuits when used maliciously.
The legality depends on the nature and intent of the actions, varying by country, state, and jurisdiction. Many countries have laws against online fraud, identity theft, and cybercrimes, with varying penalties.
Using an impersonated identity to gain money, property, or other benefits constitutes fraud or identity theft—criminal offenses in most jurisdictions. Similarly, using fake identities to harass, intimidate, or threaten others can lead to cyberstalking charges. If impersonation damages someone's reputation, the victim can sue for defamation or misuse of private information.
Several jurisdictions have enacted specific laws targeting online impersonation. Here are some examples:
- In Denmark, social media impersonation is illegal, potentially resulting in fines or up to six months imprisonment.
- Texas Penal Code §33.07 criminalizes online impersonation, with penalties ranging from a Class A misdemeanor to a third-degree felony.
- California Penal Code Section 528.5 prohibits impersonation through websites or other electronic means.
- Mississippi Code § 97-45-33 makes it a misdemeanor to knowingly impersonate another person online for purposes of harming, intimidating, threatening, or defrauding others.
What To Do If Someone Impersonates Your Business
If your business falls victim to online impersonation, taking quick action is crucial to minimize damage. Here are the most effective steps to protect your brand:
Report It To The Authorities
Reporting online impersonation to proper authorities helps prevent further harm, facilitates investigations, and can lead to the apprehension of criminals involved.
Law enforcement agencies need accurate information to investigate impersonation cases effectively. Your report provides crucial details that help them build cases and identify perpetrators. The information also helps agencies like the Federal Trade Commission (FTC) detect patterns of wrongdoing that can lead to broader investigations and prosecutions.
You can report incidents to the Federal Trade Commission (FTC), the FBI's Internet Crime Complaint Center (IC3), or your local police department.
Report It To The Platform
Reporting impersonation directly to the platforms where it happens is even more important. This action helps platforms identify and remove fake accounts, maintaining platform integrity and creating a safer environment for all users. Also, a lot of the time, police aren't able to take action due to jurisdiction issues, but platforms can take down accounts that violate their terms of service–like in the case of impersonation.

Major platforms have specific processes for reporting impersonation and take these reports seriously. This is because the scale of the problem is massive—in the third quarter of 2024 alone, Facebook took action on 1.1 billion fake accounts, slightly down from 1.2 billion in the previous quarter.
How To Prevent Online Impersonation
While responding to impersonation attacks is important, preventing them in the first place is far more effective. Here are key strategies to protect your business from online impersonators:
Employee Training
Human error is the leading cause of cybersecurity breaches. Employees clicking on phishing links or using weak passwords create vulnerabilities that impersonators exploit.
Regular cybersecurity training ensures your team understands potential threats and adopts secure practices to minimize risks. This training helps employees spot phishing attempts and suspicious activity while establishing cybersecurity as everyone's responsibility rather than just the IT department's.
Effective training also ensures compliance with industry-specific requirements like GDPR, HIPAA, or PCI DSS, protecting intellectual property and sensitive data.
Consumer Education
Educating your customers about potential impersonation attempts forms a crucial layer of defense. When consumers learn to recognize fake emails, messages, or calls claiming to be from your business, they become an extension of your reputation management. When customers fall victim to scammers impersonating your business, it damages trust in your brand.
Remember that scammers constantly update their techniques, using sophisticated technology like AI to mimic voices, create convincing websites, and craft persuasive messages. Teaching consumers to recognize emotional triggers helps them pause before responding to messages creating artificial urgency, fear, or excitement.
Protect Your Company Domain
Domain spoofing leads to phishing attacks, financial losses, and data breaches. Protecting your company domain from these attacks safeguards financial resources, maintains customer trust, and prevents reputational damage.
Domain protection also helps maintain regulatory compliance, especially in industries with strict data protection regulations, preventing potential fines and bigger legal consequences.
Monitor The Web For Impersonation Attacks

Active web monitoring stops impersonators before they can interact with customers or damage your business. Regular monitoring identifies and shuts down impersonation attempts before most consumers encounter them, keeping you ahead of evolving techniques like fake social media accounts, lookalike domains, and fraudulent mobile apps.
Monitoring creates documentation needed for legal action against persistent impersonators while preventing targeted attacks. It also reveals competitors using questionable tactics that mimic your brand.
For social media specifically, regular monitoring allows you to identify and report fake accounts quickly before they defraud your followers.
How Spikerz Can Help Protect Your Business From Online Impersonation

Spikerz is a cybersecurity platform specializing in safeguarding social media accounts for businesses, enterprises, and content creators. Our system continuously scans social media platforms to identify fake accounts mimicking your brand, looking for matching usernames, profile pictures, bios, and other impersonation indicators.
When an impersonator is detected, Spikerz sends instant alerts so your business can take immediate action. We streamline the reporting and removal process by submitting takedown requests to platforms like Instagram and TikTok on your behalf, saving you valuable time and resources.
Our platform also identifies and removes fake followers and bot activity linked to impersonation scams or fraudulent engagement, maintaining the authenticity of your social media presence.
Additional Benefits Businesses See When Using Spikerz
Beyond impersonation protection, Spikerz offers broad safeguards for your social media presence:
- We archive all your social media content—including posts and stories—providing complete backup protection regardless of unforeseen events.
- Our advanced security measures include shared two-factor authentication (2FA), dedicated email and phone numbers, and automated password rotation to block unauthorized access in real-time.
- We help prevent shadowbans that affect your account's visibility and reach, offering recommendations to ensure your activities align with community guidelines.
- Our platform centralizes all your social media permission data in one place, ensuring employees never have more access than necessary for their roles and allowing quick revocation when team members leave your organization.
If you're not actively protecting your brand's online identity, you're gambling with your business's future. The damage from a single successful impersonation attack can take months to repair—if recovery is possible at all. Don't wait until after you've been targeted. Secure your social media presence today before impersonators strike.
Conclusion
Online impersonation represents one of the most significant threats to your brand's digital presence. As we've seen, these attacks come in multiple forms—from website spoofing to social media impersonation, fake mobile apps, and executive targeting. Each approach aims to exploit your hard-earned reputation to defraud customers, damage your brand, or steal sensitive information.
The financial and reputational costs of these attacks make prevention essential. Remember, your online identity directly impacts your bottom line. Protecting it isn't just a good security practice—it's a smart business strategy.



