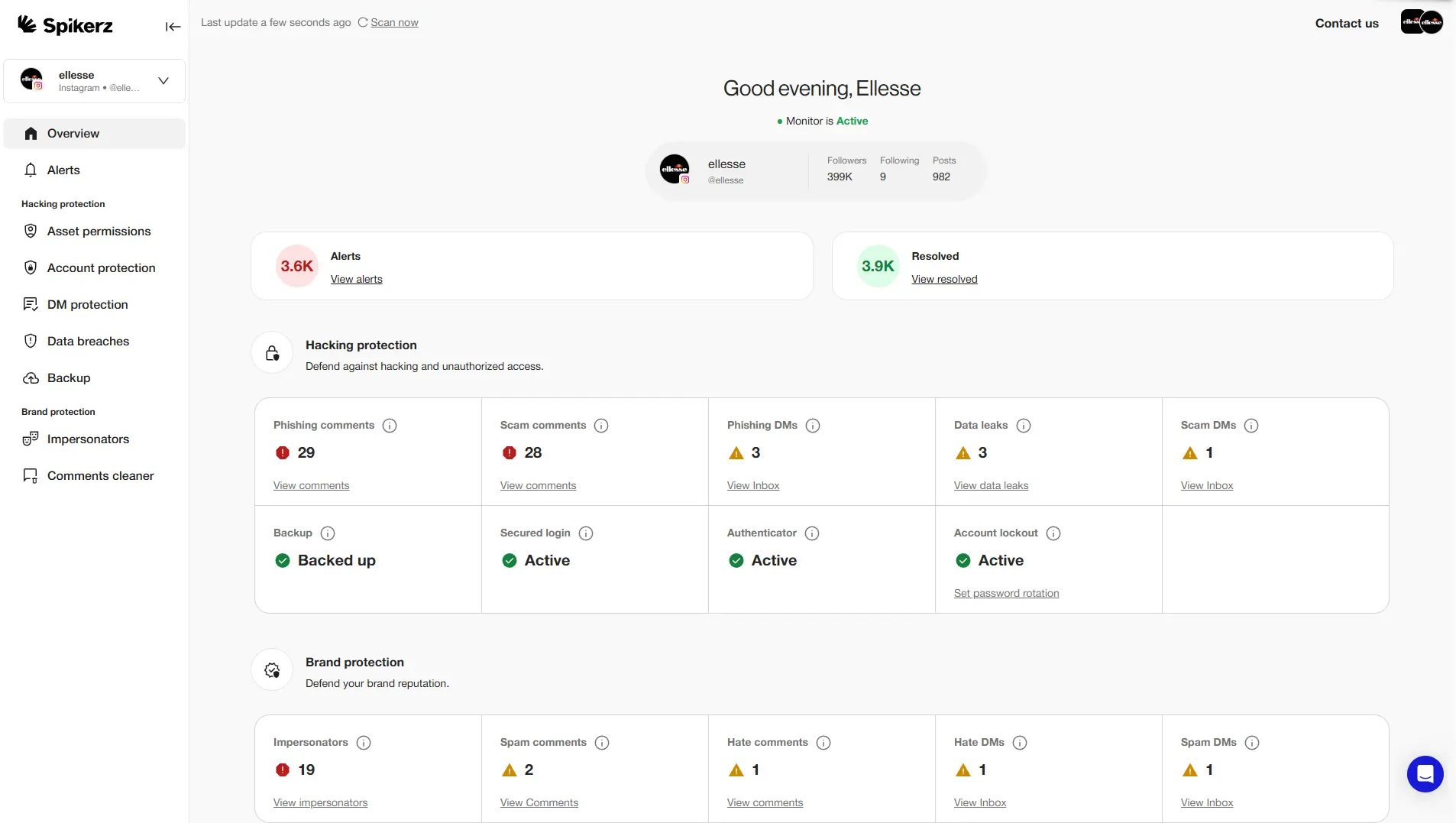
Traditional IAM Tools Are Failing Your Social Media Team
Traditional IAM Tools Are Failing Your Social Media Team
Social media drives business success by connecting brands with customers, building communities, and generating revenue opportunities that didn't exist a decade ago. Your marketing team manages these critical channels every day, posting content, responding to customers, and maintaining your brand's online reputation.
But there's a growing problem that keeps security teams awake at night: controlling who can access and manage these accounts.
When a new hire joins your marketing team, they need the right permissions to manage your social presence effectively. They should have exactly what they need to do their job, following the principle of least privilege that security professionals have preached for years.
In practice, most businesses struggle with this basic security requirement. Ex-employees retain access for weeks or even months after leaving. Team members share passwords through text messages. And marketing agencies have full admin rights when they only need to schedule posts.
Without proper security controls, your social media accounts are vulnerable to intentional takeovers by disgruntled former employees or compromise by hackers who target accounts with excessive permissions.
That’s why in this blog post, we'll explore why traditional IAM tools fail at protecting social media, the real consequences of uncontrolled access, and how specialized solutions like Spikerz address these unique challenges that generic tools simply weren't built to handle.
Your Social Media Access is a Free-for-All
Most IAM tools weren't originally designed with social media in mind, and that's where the problems start. Managing access to platforms like Instagram, Facebook, or LinkedIn is completely different from handling access to corporate resources like email, NAS, or cloud storage. These platforms come with their own authentication methods, rules, and security challenges that traditional IAM can’t easily handle due to evolving threats and user demands.
One of the biggest issues is shared credentials. Instead of neat user accounts tied to a single employee, you often end up with shared credentials that multiple team members rely on. Your social media manager logs in with the same username and password as your content creator, your graphic designer, and sometimes even external agencies.
This creates confusion and risk because when everyone uses the same login, it's nearly impossible to trace activity back to a specific individual. You can't tell who posted what, who changed settings, or who might have accidentally compromised your credentials, leaving your business exposed when something goes wrong.
Things get even messier when someone leaves the company. Traditional IAM tools don't address the problem of manual offboarding for social media accounts. Your IT department might revoke email access within hours, but who remembers to change the Instagram password?
If you forget to change a password or remove access quickly enough, an ex-employee could still log in weeks or months later. That's not just inconvenient; it opens the door to intentional misuse or accidental mistakes that could compromise your accounts and damage your brand's reputation.
Then there's the lack of visibility. Some IAM tools can tell you who has access to internal systems, but they can't show you who is posting, editing, or granting permissions inside a social platform.
Without that insight, managers can't enforce accountability. Marketing directors have no idea if their junior staff member just gave admin rights to an intern and security teams can't detect when someone logs in from an unusual location. Hackers know this and exploit these blind spots, they're aware that social media accounts often have weaker oversight than other business systems.
On top of that, many businesses struggle juggling multiple platforms. A marketing team might manage a dozen different accounts across TikTok, X, YouTube, etc. Each platform has its own login system, its own permission structure, and its own security settings. Traditional IAM tools weren't built to handle this fragmentation, making it nearly impossible to enforce consistent security policies or standards across all your social channels.
What Happens When Your Social Media Access Goes Unchecked?
Social platforms are one of the most visible and influential touchpoints a business has with its audience. When you manage these platforms well, this high visibility is an advantage; it helps you build trust and connect with thousands or millions of prospects. But it can also turn against you if the wrong people have control.
Think about it. What if a disgruntled ex-employee still had access to your company's Facebook page and decided to post something offensive?
In minutes, that post could spread like wildfire. People would screenshot it, share it, and comment on it. Your brand could be trending for all the wrong reasons within an hour.
It's the kind of PR nightmare that damages trust in your business instantly and takes months or even years to repair. What’s worse is that the financial impact goes far beyond just losing customers. You might also face legal action, contract cancellations, and a complete breakdown in stakeholder confidence.
Or imagine this scenario: your Instagram account gets hacked because everyone in your team was still using the same generic password from three years ago. Suddenly, a stranger has full control and they lock you out completely.
They could delete years of content that took thousands of hours to create, or worse, flood your feed with damaging posts, scam links, or inappropriate content. Recovering an account can take days or weeks of back-and-forth with platform support, and the longer it's out of your control, the more damage builds up. Every hour means more lost followers, more damaged relationships, and more revenue disappearing.
Generic IAM vs. Spikerz: How To Choose The Right Tool For the Job
There are several critical factors you should consider when choosing between using a generic IAM tool and a specialized solution like Spikerz for your social media security needs. Both tools have their place, but understanding their fundamental differences helps you make the right choice for protecting your brand's online presence.
Here are the main things you should consider:
Shared Passwords vs. Token-Based Access
Password sharing happens when people give out their login credentials so others can access accounts or apps on their devices. It's common in marketing teams, where the social media manager texts the Instagram password to the new content creator, who saves it in their notes app, and then shares it with the graphic designer over Slack. Before long, that password exists in dozens of places, creating multiple points of vulnerability where hackers can strike.
Shared credentials make it impossible to know who's logging in, who's making changes, and who might still have access long after they shouldn't. When five people use the same password, you can't prove who posted that controversial tweet or who accidentally deleted your video archive.
Even encrypted password sharing through password managers only patches the problem instead of solving it. At the end of the day, you're still depending on the same shared credentials that create accountability nightmares and security vulnerabilities.
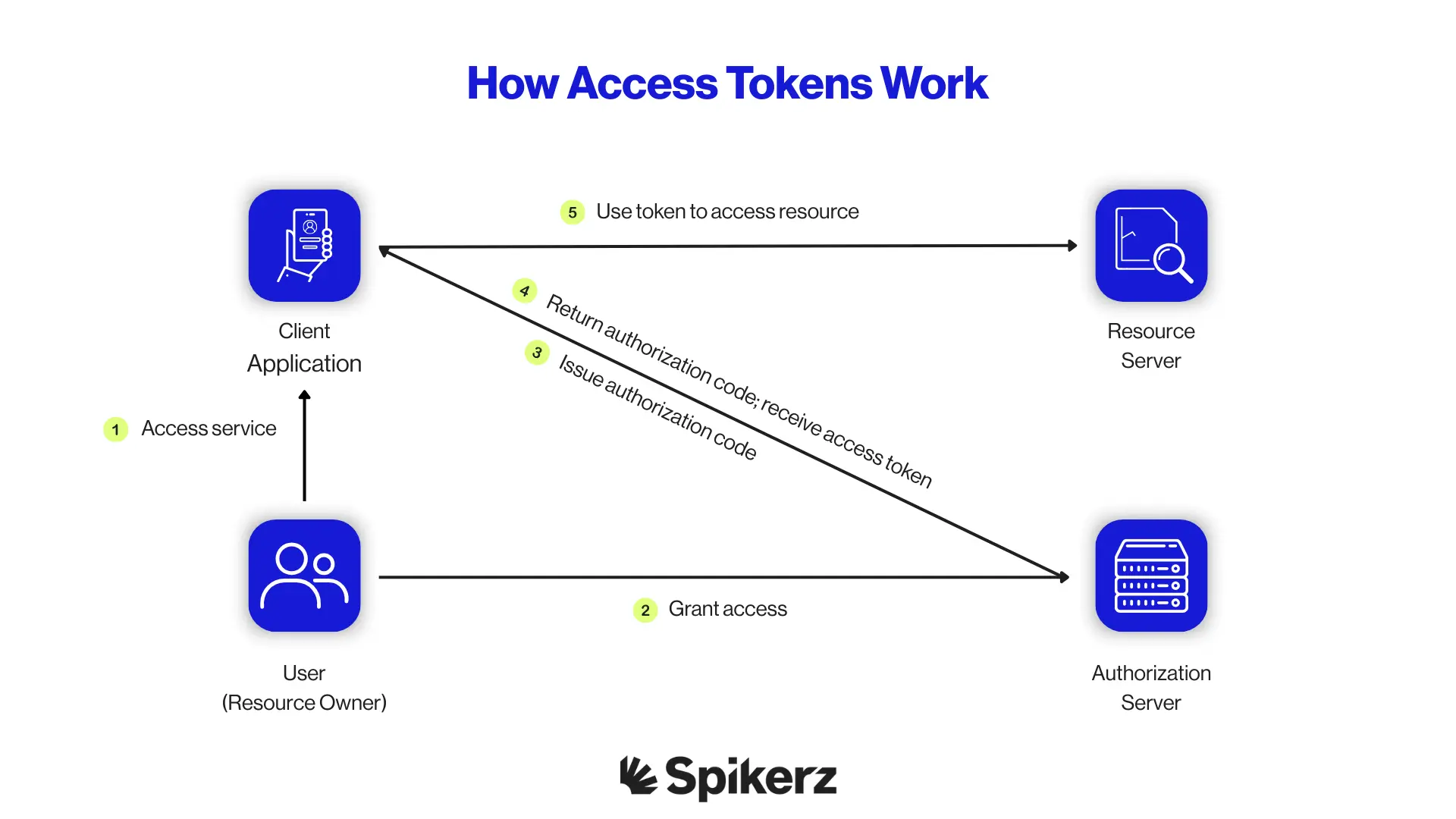
Token-based access takes a completely different approach. Instead of one password being shared between multiple people, each person receives a unique token that proves their identity. Think of it like having individual keycards for a building instead of copying the same physical key for everyone. The token can't be duplicated easily and doesn't need to be memorized or manually entered.
This results in access that's far more secure, granular, and user-friendly. You control exactly who gets in, when, and from where, without exposing your actual login details to anyone on your team.
This is where Spikerz sets itself apart from traditional approaches. Traditional IAM tools often still rely on password-based systems that leave gaps in security, especially on social media accounts where platform limitations make standard IAM controls ineffective.
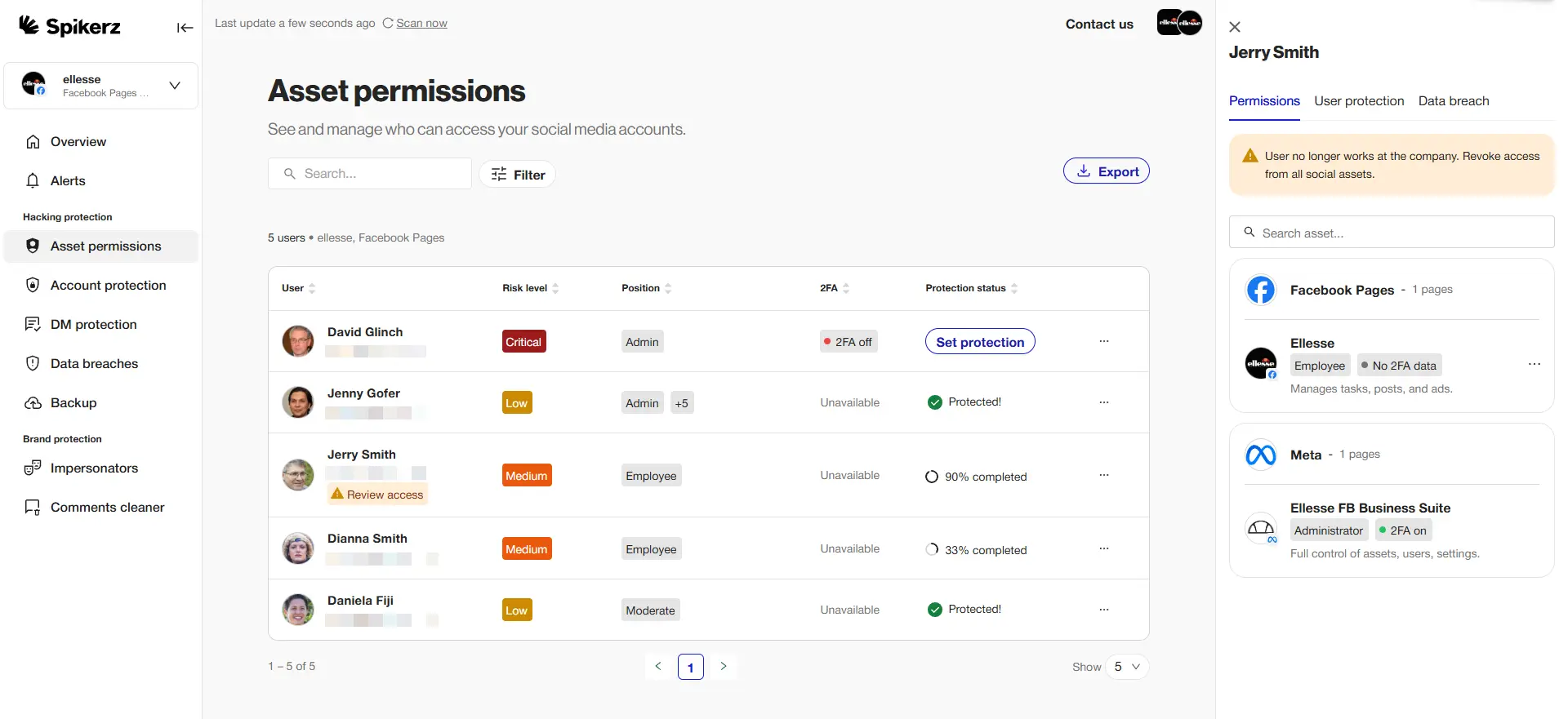
Spikerz eliminates shared credentials altogether, assigning unique, dedicated access to each team member through secure token authentication. It locks down two-factor authentication at the account level, enforces platform-specific rules, and adapts to risky behavior with capabilities like access by location and device control.
The system also enforces password rotation automatically when suspicious behavior is detected, with no manual intervention needed. This makes the login experience secure and designed for the way marketing teams actually work, without the friction that makes people bypass security measures.
Granular Role Delegation
Granular role delegation is when you give people access that matches their exact responsibilities instead of handing out full control to everyone. Think of it like a restaurant where the waiter can take orders but can't access the cash register, while the manager can do both. Instead of treating every user as an admin with unlimited power, it allows permissions to be fine-tuned so one person can upload content, another can moderate comments, and someone else can view analytics without being able to post anything.
%20Tools.webp)
Generic IAM tools don't really solve this for social media platforms. They're built for owned platforms like websites, internal applications, or cloud services that you control directly. But Instagram, TikTok, and X operate independently with their own permission systems that generic IAM can't reach into.
These tools work well at managing who can access your CRM or email system, but they can't distinguish between someone who should only schedule posts versus someone who needs full admin rights on your Facebook page. Teams end up stuck with shared credentials or excessive permissions because the tool simply can't provide the granular control these platforms require.
Spikerz changes that dynamic by assigning roles tailored to each platform's unique structure. A team member can be a "Content Uploader" on Instagram with permission to post and edit captions, a "Community Manager" on X with access to respond to messages and comments, and have no access at all to your TikTok or LinkedIn accounts.
Each permission is tracked, monitored, and instantly adjustable through a central dashboard. When someone's role changes or they move to a different campaign, you can modify their access in seconds. No more wondering who has access to what, because every permission is visible, logged, and controlled. Each person gets exactly what they need, and nothing more.
Seamless Onboarding and Offboarding
Onboarding is the process of giving a new team member access to the tools and accounts they need to do their job. For social media teams, that means connecting them to the right platforms, with the right permissions, at the right time so they can start creating, posting, or managing campaigns immediately. Offboarding is the opposite. It's what happens when someone leaves your team, and their access needs to be revoked everywhere, immediately, and completely.
Most businesses handle this manually, and that's where problems multiply. The marketing manager has to remember every platform the departing employee had access to.
They need to change passwords on Instagram, Facebook, TikTok, LinkedIn, X, YouTube, and any scheduling tools. For example, they must remove the person from Facebook Business Manager, revoke their access in TikTok’s Creator Studio, and update permissions in every third-party tool.
If managers forget one platform, it becomes a security vulnerability. The challenge is that most businesses don't have full visibility into who has access to what, which leaves the door open for mistakes, oversights, or even intentional misuse by former team members who discover they still have access weeks later.
Spikerz makes both processes seamless and secure. New hires can be onboarded in minutes with access that matches their specific role, without the hassle of sharing passwords or juggling admin requests across multiple platforms. The system automatically provisions the exact permissions they need based on their role.
When it's time to offboard, one click immediately cuts off their connection across every platform you use, from Instagram and TikTok to LinkedIn and YouTube. No manual password changes, no forgotten accounts, no security gaps.
Traditional IAM tools weren't designed for these types of requirements. They often make the process complex, expensive due to manual intervention, and even incomplete because access is scattered across multiple accounts with different authentication systems. But Spikerz was built specifically for this challenge.
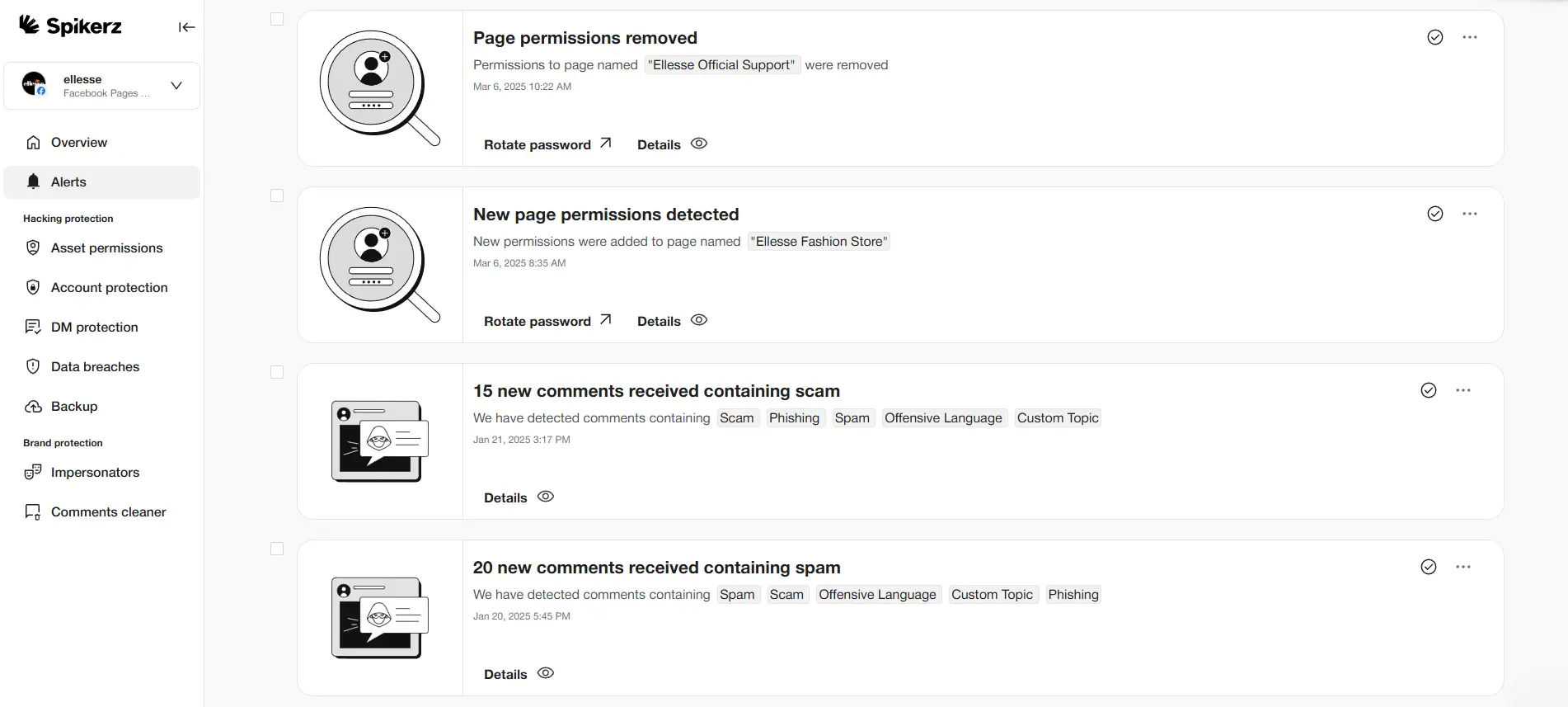
Spikerz doesn't just grant or revoke access; it monitors accounts 24/7 for unusual activity. The system detects suspicious behavior patterns, like login attempts from new locations or devices, and sends instant alerts if someone tries to use permissions they shouldn't have.
Every transition, whether someone is joining or leaving, is quick, secure, and fully under control. You maintain complete visibility and audit trails for compliance, while your team gets frictionless access to do their jobs effectively.
Platform-Specific Insights
Spikerz gives businesses something generic IAM tools can't deliver: a clear audit trail of every action taken on their social media accounts.
Through our alerts dashboard, you can see exactly who made a change, when it happened, from which device, and what specific action was taken. For example, you’ll be able to answer:
- Who published that post at 3 AM?
- Who changed the bio on your Instagram account?
- Who gave admin access to that contractor?
- Were there new unauthorized page permissions on my business account?
Every detail is logged in real time, creating an indisputable record of all account activity.
This level of visibility makes it easy to hold people accountable for their actions and to spot unusual activity before it becomes a crisis. If an unauthorized role change appears in your Facebook Business Manager, if someone tries to log in from an unusual location like a different country, or if someone attempts to elevate their permissions without approval, Spikerz flags it immediately. After that, you receive instant notifications about potential security issues, allowing you to respond before damage happens.
Having a detailed record of every action protects your social media presence in multiple ways.
- It ensures accountability by making it impossible for team members to deny their actions.
- It reduces insider threats by preventing malicious behavior because people are less likely to misuse access when they know every action is tracked.
- It provides evidence for compliance audits and investigations.
- Most importantly, it gives you full control and transparency across all platforms, something that's impossible when relying on generic IAM tools that can't see inside social media platforms.
Why Brand Managers Are Making the Switch
Brand managers across industries are discovering what happens when they regain control of their social media security. No more waking up at 3 AM worried about whether that fired contractor still has access to your Instagram account. No more scrambling to change passwords across a dozen platforms every time someone leaves the team. No more guessing who posted what or wondering if your accounts are truly secure.
With Spikerz, you sleep better at night knowing your social media presence is protected by technology built specifically for these platforms. Your team can focus on what they do best (marketing) instead of wrestling with security procedures that slow them down. Creative work flows smoothly because the right people have the right access at the right time. Security becomes invisible yet ironclad, working in the background while your team builds your brand.
The choice is clear. You can continue struggling with generic IAM tools that leave dangerous gaps in your social media security, or you can implement a solution designed from the ground up to protect your most visible business assets.
Don't wait for a security incident to force your hand. Take control of your social media security today. Create a Spikerz account right now to transform your team's access management and protect your brand's reputation.
Conclusion
Traditional IAM tools were never designed to handle the unique challenges of social media security. They can't eliminate password sharing, can't provide platform-specific permissions, and can't give you visibility into who's doing what on your accounts.
The stakes are too high to rely on tools that only partially protect your social media presence. One security breach, one rogue post, or one compromised account can undo years of brand building and customer trust.
Generic solutions leave you vulnerable because they treat social media like any other IT system, ignoring the specific threats and requirements these platforms present. Specialized solutions like Spikerz exist because social media security demands specialized protection.
When you choose the right tool for the job, you're not just checking a security box; you're investing in your brand's future, your team's productivity, and your peace of mind. The question isn't whether you need better social media security, it’s how much longer you're willing to operate without it.

.webp)

