How To Protect Your Organization On Social Networking Sites
How To Protect Your Organization On Social Networking Sites
Conversations happening on social platforms like LinkedIn aren't just about networking. They're hunting grounds for cybercriminals who exploit the trust we've built in these professional spaces.
A connection request from what appears to be a potential partner. A direct message about an exciting business opportunity. Even a comment on your latest company update. Each of these seemingly innocent interactions could be a trap designed to steal your credentials or infiltrate your systems.
That’s why businesses and users need to take these threats seriously and implement protective measures before attackers strike. In this blog post we’ll cover the security risks present on social networking sites, why they matter to your business, and practical steps you can take to protect your organization from becoming the next victim.
What Are The Biggest Security Issues People Face On Social Networking Sites?
Social networking sites might feel harmless, but attackers use them as intelligence-gathering hubs. The wealth of personally identifiable information (PII) made public there allows criminals to quietly collect details about you and your employees without anyone realizing what's happening.
Job titles, birthdays, pet names, and favorite sports teams become ammunition. Attackers piece these details together to guess passwords, answer security questions, and build enough trust to execute scams.
Once attackers gather sufficient information, they launch targeted attacks that put your security at risk. The most common methods include:
- Social engineering: Attackers manipulate people into sharing sensitive information or transferring money. An attacker might call an employee pretending to be an executive, using details pulled from social media to pressure them into sharing credentials or approving wire transfers.
- Phishing: Criminals create realistic-looking emails or messages to trick people into clicking malicious links, downloading infected files, or surrendering login credentials. These attacks succeed because they're tailored to victims' personal lives or workplaces, making them far more convincing than generic spam.
- Brand impersonation: Attackers create fake accounts or websites that look nearly identical to legitimate businesses. Once someone trusts these imposters, they willingly hand over login details, personal information, or financial data.
- Site compromise and data theft: Attackers use social media intelligence to design malware specifically targeting your company's systems. They might use stolen credentials to slip into private networks undetected. Once inside, they steal massive amounts of sensitive information.
- Spreading malware: Criminals set up fake websites or domains that appear official, tricking people into downloading malicious files or entering passwords. These attacks spread rapidly since people trust the brand or employee name attached to the scam.
- Data breaches: When attackers gain access to account credentials through any of these methods, the consequences multiply. Massive amounts of private data get stolen, causing financial and reputational damage that can take years to recover from.
Here’s what you should know: Every platform offers different benefits to attackers depending on their goals. But the process starts the same way, gathering information that people willingly share online. Once they have enough, they launch a combination of these attacks to maximize damage.
Why Does This Matter To You?
Security issues such as phishing might seem like just another annoying email or message to delete. But the damage from successful attacks can happen overnight. These attacks affect individuals, but they severely damage businesses in ways that can permanently alter your company's trajectory.
Here are some common consequences of a successful attack:
- Financial Loss: Fraudulent wire transfers drain company accounts. Unauthorized access to banking systems moves money overseas before anyone notices. And ransomware demands the impossible choice between paying criminals or losing critical data.
- Data Breaches: Client information disappears into the dark web. Internal documents containing trade secrets get sold to competitors. Intellectual property developed over years vanishes in minutes. Also, each breach triggers legal battles and compliance investigations that drain resources.
- Reputation Damage: A single compromised account can destroy years of carefully built trust. Scammers use your brand to defraud followers and malicious messages sent to clients make them question your professionalism. As a result, the credibility you worked so hard to establish evaporates overnight.
- Account Loss: Losing control of a valuable social media account means losing all its content, connections, and history. These attacks happen daily to accounts of all sizes. Recovery can take weeks or months, if it happens at all.
How To Protect Yourself On Networking Sites
There are many effective methods to ensure you never fall victim to phishing and impersonation attacks. Here are the most effective strategies to implement immediately:
1) Analyze All Your Messages For Phishing Attempts
Protecting your business on social networking sites starts with scrutinizing every message you receive. No exception.
Attackers constantly adapt their tactics, using tools and different techniques to trick employees and access valuable information. Your staff needs to carefully analyze every message to build stronger defenses and reduce the chances of falling victim.
Being ready allows you to:
- Prevent adversaries from using malware to steal credentials and bypass authentication controls
- Monitor for convincing GenAI-crafted emails that accurately imitate your brand's identity or key personnel
- Protect workforce collaboration tools, call centers, and mobile phones against synthetic media like deepfakes
- Detect early signs of social engineering attempts before they escalate into security breaches
2) Limit The Amount Of Information You Publicly Share
One of the simplest yet most effective ways to protect your business is limiting publicly shared information. Every detail you post, including job titles, team structures, and personal interests, are pieces of the puzzle attackers use to make their scams more convincing.
LinkedIn is an excellent example. Businesses highlight their employees and share achievements. Employees post about projects, accomplishments, and tools the company uses. These actions give attackers valuable insights into how your business operates. What’s worse is that information helps them guess passwords, impersonate staff, or target specific employees with tailored attacks.
That’s precisely why you should keep all your profiles professional but not overly detailed. Encourage employees to think before they post. Making it harder for attackers to gather intelligence dramatically reduces their success rate.
3) Monitor The Deep/Dark Web
The hidden corners of the internet are where criminals plan attacks, trade information, and sell stolen data. Paying attention to these spaces gives you a chance to stay ahead of potential risks.
Also, attackers frequently discuss targets and tactics in dark web forums. Once they succeed, they quickly move to sell sensitive data like credentials, identities, or financial information. When this happens, the damage spreads quickly, putting your business and customers at risk.
Deep web monitoring helps identify these activities early. You can see if your business is being mentioned as a target or if stolen data tied to your company is already circulating.
The best thing about monitoring is that if a breach happens, this visibility helps you understand exactly what was compromised. You can act immediately by changing passwords, updating phone numbers, or strengthening authentication methods before criminals exploit the stolen information.
4) Use Social Media Monitoring
Social media monitoring protects your business in many different ways. Attackers aren't just after credentials and data; they're after influence.
They launch operations to sway public sentiment, spreading harmful narratives to damage your reputation and demoralize employees. What’s worse is that these campaigns can destroy customer trust faster than any data breach.
That said, monitoring your own social media accounts for attacks and unauthorized access is just as important. Hackers hijack business profiles to scam followers, spread misinformation, or steal sensitive information. The biggest issue is that recovery from these attacks can be difficult and expensive.
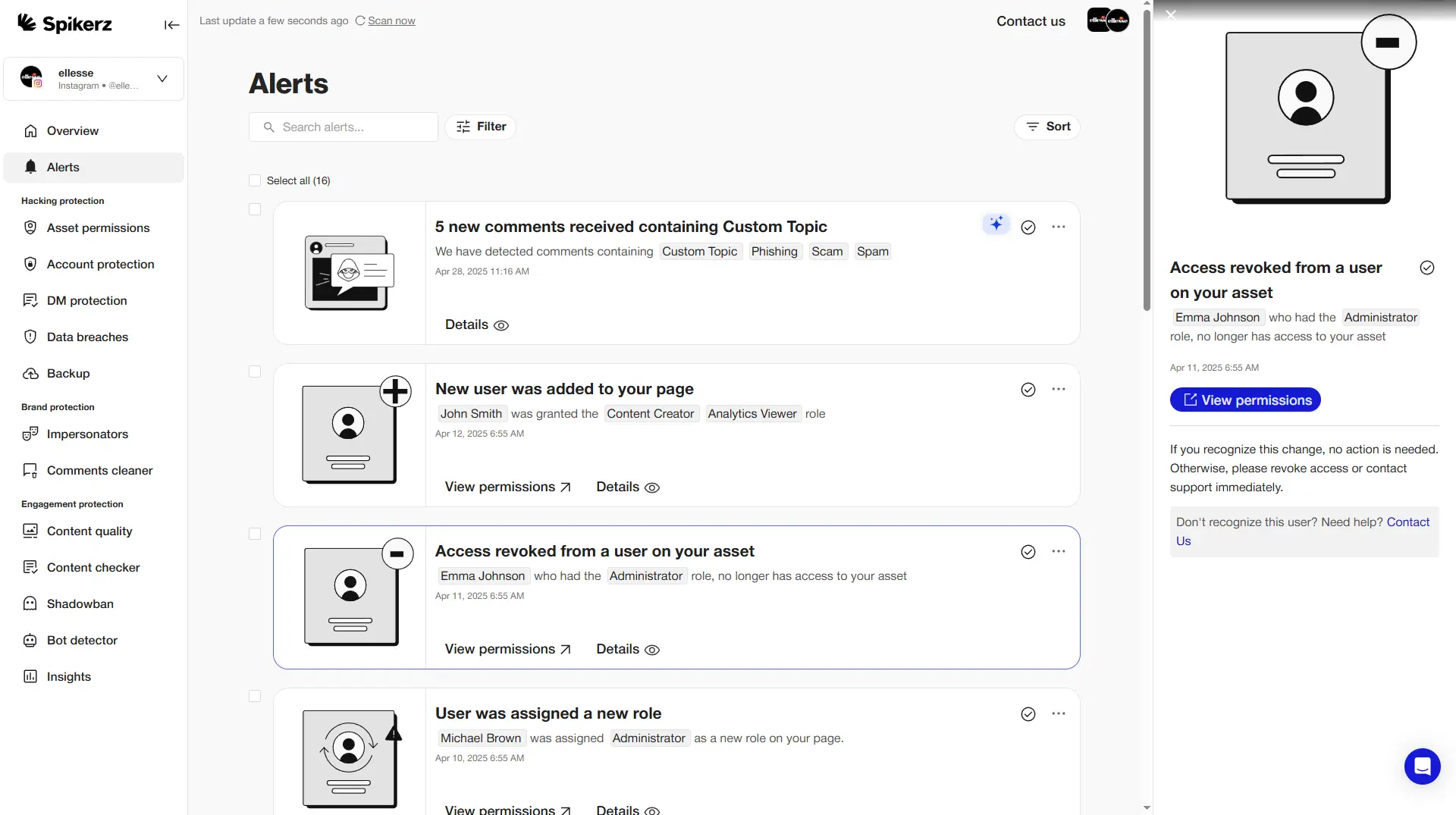
However, there are tools that can help protect you from these threats. The best way to stay ahead is using a security tool like Spikerz. It helps businesses spot suspicious activity and detect account breaches in real-time. When someone tries to break into an account, Spikerz immediately blocks the attempt and changes passwords to stop the attacker.
It protects against brand impersonation by detecting when someone uses your company assets like pictures, logos, or name to trick users. Additionally, it shields accounts from phishing attempts, spam, bots, and malicious links. For instance, when a harmful link appears in direct messages, it flags the threat before anyone clicks it.
5) Identity Verification
Protecting your business means going beyond passwords and traditional security tools. Many platforms now use biometric authentication, like facial recognition or voice verification. However, attackers are finding ways to bypass these systems.
The biggest threats come from synthetic media like deepfakes, like realistic but fake videos or audio clips that trick systems into believing an attacker is legitimate. Combined with presentation attacks (showing fake images or recordings) and injection attacks (feeding false data directly into systems), the risks multiply.
Watch out for these fake authentication attempts and add extra security around your biometric systems. Set up multiple verification steps so that even if attackers create fake videos or audio, they still can’t get into your accounts.
Conclusion
Social networking sites have gone from simple communication platforms into battlegrounds where cybercriminals hunt for their next victims. Every profile update, connection request, and direct message is both an opportunity and a potential threat to your organization's security.
The attacks we discussed above aren't theoretical risks relegated to tech giants and government agencies. They're happening right now to businesses just like yours. Attackers don't discriminate based on company size. They simply look for the easiest targets, and those are usually the ones who believe they're too small or unimportant to need protection.
But here's what makes the difference between being vulnerable and being secure: preparation and having the right tools. If you limit information exposure, monitor for threats, analyze messages carefully, and use specialized security platforms like Spikerz, you’ll transform your social media presence from a vulnerability into a secured business asset.
The choice is yours: wait for an attack that statistics say is coming, or take action now to protect everything you've built online.



