ATO Prevention: 9 Steps to Keep Your Social Accounts Safe
ATO Prevention: 9 Steps to Keep Your Social Accounts Safe
Attackers frequently exploit the weakest link in any security chain: people. They use social engineering tactics and phishing campaigns to trick employees or social media managers into revealing their login credentials. If they succeed, a single compromised account with high-level access can give an attacker control of a company's entire social media presence.
That’s why you must do everything in your power to keep your accounts safe. In this blog post, you'll learn exactly what an Account Takeover (ATO) attack is and discover nine actionable steps to prevent them.
What Is An Account Takeover Attack?
An account takeover (ATO) attack happens when a criminal gains control of your online account. Attackers employ different types of methods to achieve this goal. These methods include using stolen usernames and passwords, phishing scams, malware, or even buying credential lists found on the dark web.
Once they control a legitimate account, their goal is usually fraud. This often comes in the forms of completing unauthorized transactions, stealing personally identifiable information (PII), or using the account as a stepping stone for additional attacks. For example, on social media platforms, an attacker might hijack a user’s profile to spread phishing links, scam followers, or impersonate them to gain even more access.
How To Prevent Account Takeovers
There are many ways to prevent account takeovers. However, the most effective defense includes creating a zero trust framework that creates multiple layers of security. This approach ensures you never rely on a single solution to protect your valuable assets.
1) Set Rate Limiting On Login Attempts
Rate limiting is a measure where businesses place a cap on how many times someone can try to log in within a set timeframe. For example, a business might allow three attempts per hour. Businesses implement this because most account takeover attacks rely on brute force.
Attackers use bots to try thousands of password combinations hoping to find the correct one. If the bot is limited to just a few attempts per hour, then the attack becomes impractical and highly unlikely to succeed. Instead of leaving accounts exposed to endless guessing, rate limits stop the attack before it can cause any damage.
To make this step effective, set limits based on more than one factor, such as usernames, devices, and IP addresses. If you only rely on one factor, it makes it easier for attackers to find a workaround.
For instance, if you only limit by IP address, an attacker using a botnet with many IPs could still brute force accounts. On the other hand, if you only limit by username, someone with a list of usernames could try password variations until they find one that works.
Setting login limits based on typical user behavior helps maintain a balance between security and convenience. Also, adding restrictions on proxies and VPNs strengthens the security even more.
2) Protect Against Credential Stuffing Bot Attacks
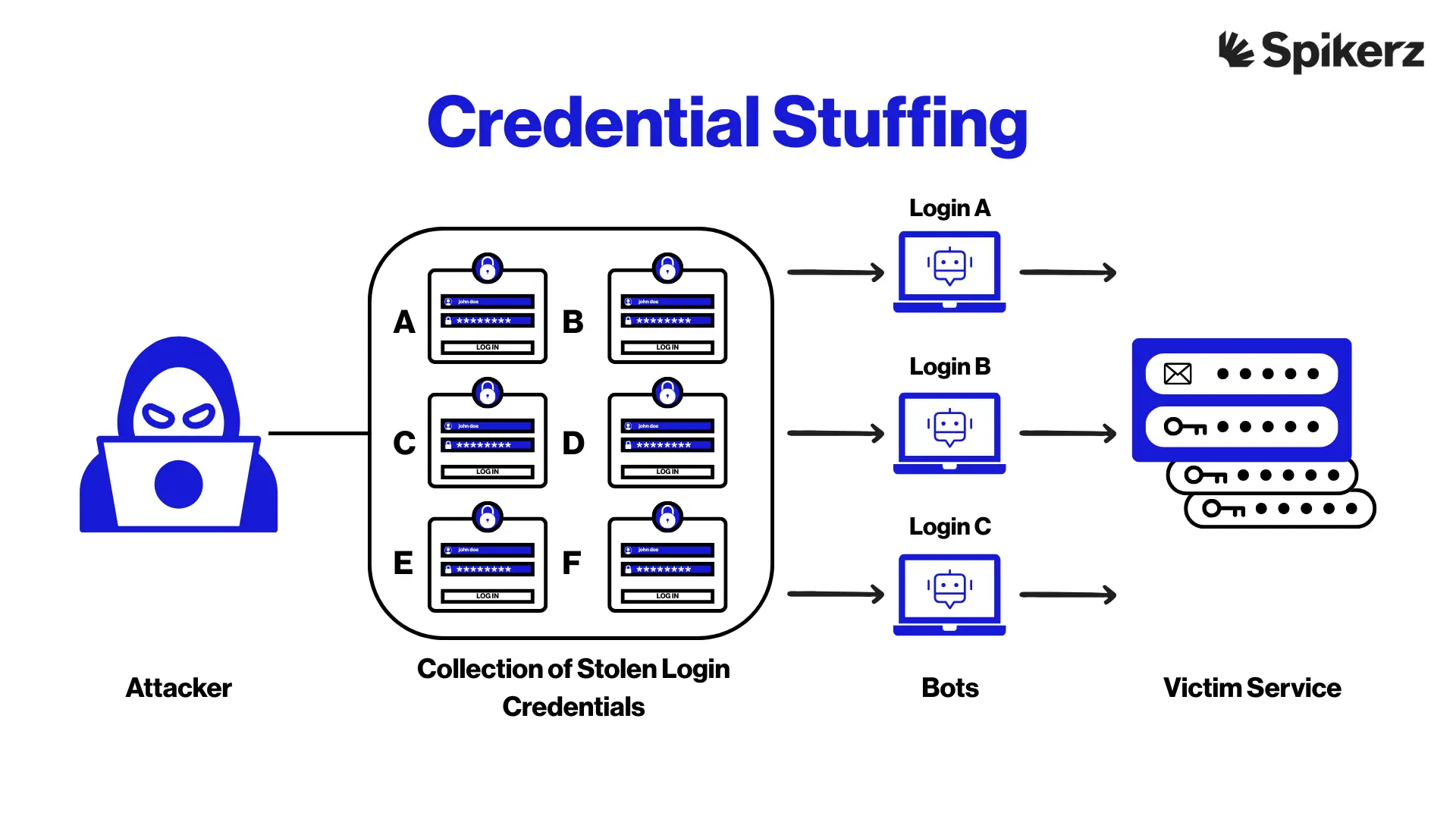
Credential stuffing is a type of cyberattack where stolen usernames and passwords from one data breach are used to try to access accounts on other platforms. For instance, you become vulnerable if you use the same login details for your Instagram account and your Gmail.
If a third-party app connected to Instagram gets breached and your data ends up on the dark web, attackers could use those same credentials to hijack your Gmail, lock you out of your accounts, and even impersonate you online.
This type of attack is widespread because massive lists of stolen credentials are constantly being traded and sold. Attackers use automated tools and bots that can quickly test thousands of the stolen credentials across different sites, easily bypassing traditional login protections. Your best defense starts with awareness and monitoring. If you find that your credentials have been compromised, you need to act fast and protect yourself.
If you want to protect your social media profiles, one of the most reliable ways is to use a tool like Spikerz. Spikerz protects your accounts by blocking malicious bot activity that fuels credential stuffing attacks. It offers continuous protection through 24/7 monitoring for unauthorized logins and detection of exposed credentials.
You'll also receive instant alerts for suspicious activity so you don’t lose control of your accounts, which attackers can then use to steal data.
3) Use A Zero Trust Framework
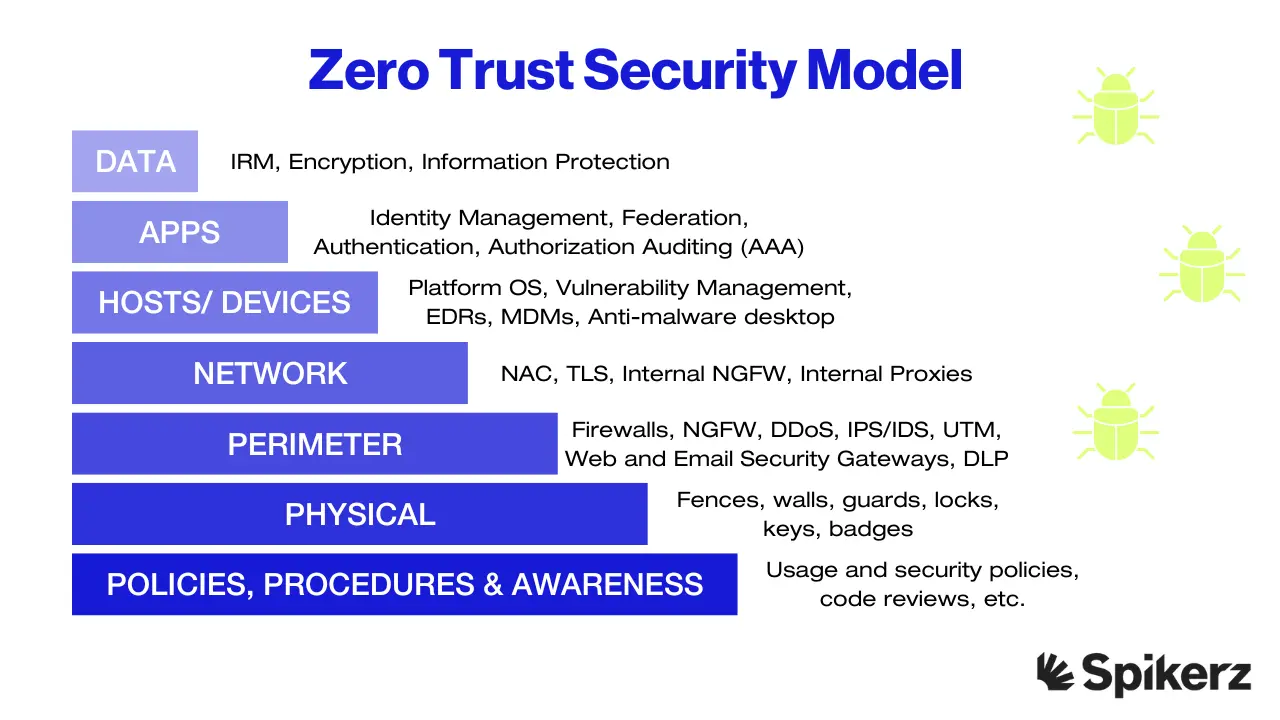
Zero Trust is a security strategy built on a set of principles designed to protect user accounts, devices, applications, and data wherever they live. At its core, Zero Trust operates on the idea of “never trust, always verify”. Instead of assuming that everything behind a corporate firewall is safe, it treats every request as if it could come from an unsafe network.
That means no one gets automatic access, no matter where they are or what they are trying to reach. The framework is built on three main principles:
- Verify explicitly by always authenticating and authorizing based on all available data points.
- Use least privilege access, which means giving users only the access they need, when they need it, and nothing more.
- Assume breach, which minimizes potential damage through segmenting access, encrypting end-to-end, and using analytics to detect threats and strengthen defenses.
These practices are especially important now that mobile workforces and cloud-based systems make traditional defenses less reliable.
The good news is, Spikerz helps put these principles into action with its Asset Permissions capabilities. This gives organizations precise control over who can access what, ensuring that every request is verified and aligned with the idea of least privilege access.
Thanks to its centralized dashboard, you can control which users have access and assign roles, see their risk level, whether they have two-factor authentication enabled, and their overall protection status.
Apply Zero Trust principles through tools like Spikerz to protect your business against account takeovers and keep your digital space secure.
4) Enable Two-Factor Authentication (2FA)
Two-factor authentication (2FA) adds an extra layer of security on top of your password. Instead of relying on just one factor, like something you know (your password), 2FA asks for a second factor before granting access. This second factor could be something you have, like a code sent to your phone or generated by an authenticator app, or something you are, like a fingerprint or Face ID.
The idea behind 2FA is that two distinct pieces of evidence are much stronger than one. A hacker might guess or steal your password, but without access to your phone, biometric data, or hardware key, they can’t break in. That said, hackers are a lot smarter and have ways to bypass regular 2FA, which is why it is not enough anymore. You need Spikerz to make sure you are fully protected and that your accounts are secured.
For teams and businesses, Spikerz makes this process easier. Instead of tying 2FA to personal phone numbers or random devices, Spikerz provides 2FA for teams. It hosts, manages, and secures your 2FA tokens across platforms, so everyone on your team benefits from reliable protection without the hassle of managing codes on their own devices.
If you need to share 2FA codes between team members and struggle trying to reach the person with the code, give Spikerz a try. It simplifies the entire process and removes friction.
5) Enable Suspicious Login Alerts
Enabling login alerts provides real-time detection of unusual activity, which allows you to act before any damage happens. If you know right away that someone is trying to get into your account from a new device or unfamiliar location, you keep control of the situation.
For example, if you receive an alert about a login that does not look right and you know is not from anyone on your team, you can immediately lock the account, reset your password, and deny access. That quick response is the difference between keeping your personal or business data safe.
There are many different monitoring tools available, each with its unique set of features and benefits, but we recommend you check Spikerz. Spikerz takes this type of protection to the next level thanks to the AI-powered engine we use to monitor every login attempt.
If something suspicious happens, Spikerz does not just alert you through its dashboard, it automatically blocks unauthorized access and prevents attackers from getting in. Alerts are not only for suspicious logins, but they also alert you from social engineering tactics like impersonation and phishing.
6) Enable Unauthorized Session Kills
Unauthorized access happens when someone gets into your organization’s systems, networks, data, or social media accounts without permission. It’s one of the most common ways attackers steal information, inject malicious code, or exploit vulnerabilities.
When bad actors get in, they can steal sensitive data like customer records and financial details, intellectual property, and even take over your company’s social media to spread misinformation or scam your followers. They can also disrupt operations, causing downtime and loss in productivity.
The good news is that authorized session kills are one of the most effective defenses against this. The idea is simple: it’s basically cutting off intruders the moment they’re detected. When you do that, it immediately stops them from digging deeper, stealing more data, or hijacking accounts.
Thankfully, this can easily be done with Spikerz. If it detects suspicious activity, it instantly kicks out the intruder, changes your password, and notifies you of what happened. Then you can either keep the strong, auto-generated password Spikerz creates or swap it out for one of your own. Either way, the account is locked down before the attacker has another chance to get in.
7) Use Strong Passwords
Weak or reused passwords are like leaving your front door unlocked so attackers can break in. A strong password, on the other hand, acts as a solid lock that keeps your sensitive information safe.
To make your passwords strong, each one should be unique and randomly generated. You should aim for at least 14 characters, though 20 or more is much better. Mix letters, numbers, and symbols to increase complexity. Then update your passwords every six months, and never share them with anyone to limit your exposure if a breach happens.

That said, managing dozens of unique, complex passwords can become overwhelming, but that’s where password managers come in. There are services like LastPass, Proton Pass, or 1Password that securely store your passwords and generate new ones for you. This means you can create strong credentials for every account without needing to remember them all.
8) Train Your Employees To Recognize Phishing Attacks
Cybersecurity awareness ensures your team understands the importance of never sharing personal information in response to unsolicited requests, no matter how convincing they look.
If your employees know how to identify phishing links or sites, your business will have an advantage over cybercriminals (as your employees act as your first line of defense). Many large-scale cyberattacks begin with a single click on a phishing link, and that one mistake can trigger a chain of serious consequences. That’s why it’s essential for your team to look closely at URLs and spot minor misspellings or suspicious domains.
Once hackers take over an account, they can use it as a launchpad for even more sophisticated attacks. What’s worse is that regaining control can take time, and in the meantime, your credibility and customer relationships are on the line. Preventing that first click is easier than repairing the fallout afterward.
9) Freeze Compromised Accounts
Freezing a compromised account simply means putting it on hold so no one, especially attackers, can make changes or take harmful actions. When an account gets breached, attackers often try to change passwords quickly, update recovery information, or even lock you out completely. When you freeze the account, you cut off their ability to do this and give yourself time to secure things properly.
This is extremely important if you want to prevent full account takeovers. If you allow an attacker to keep access, they can do damage that’s hard to reverse.
Thankfully, there are tools like Spikerz that make this process easier and faster. If your account is successfully breached, Spikerz automatically locks it down, removes intruders, and rotates your password to keep them from sneaking back in.
To enable password rotation, you just need to activate the option in your settings. If Spikerz changes your password, you’ll see the exact date it happened on your dashboard and you’ll also get a real-time alert, giving you both immediate protection and a clear record of what went on for your own reference.
Conclusion
Protecting your social media presence starts with recognizing a critical fact: the human element is often the biggest security vulnerability. Attackers know this, and they actively leverage social engineering and phishing to gain control of high-value accounts.
The most effective defense against account takeovers is a multi-layered security strategy, grounded in the principles of a Zero Trust framework.
This protection plan goes beyond basic passwords and includes strict measures like setting rate limits on login attempts, implementing strong two-factor authentication (2FA) for teams, and training employees to spot phishing scams immediately. Also, tools like Spikerz complement these efforts by providing 24/7 monitoring, automatic suspicious login alerts, and instant session termination when intruders are detected.
Taking these proactive steps ensures that even when targeted, your business's digital assets remain secure, protecting your reputation and your revenue.
You've worked hard to build your brand and audience. Don't let an easily preventable security lapse compromise your entire online presence. Embrace robust cybersecurity practices and leverage specialized solutions to transform your social media accounts from potential liabilities into securely managed business assets.
Ready to implement enterprise-grade security for your social media accounts?
Create a Spikerz account to automatically protect your accounts from hacking, phishing, and bot attacks today.

.webp)

