Social Media Security Tips To Protect Against Online Threats
Social Media Security Tips To Protect Against Online Threats
Social media security isn't just about switching on platform settings and hoping for the best. Your business accounts need active protection against hackers, phishing attacks, and brand impersonation because these threats grow more sophisticated every day.
Platform defaults won't save you when cybercriminals target your accounts. You need a strategic approach that combines in-built platform tools, smart practices, and specialized security tools to keep your digital presence safe.
The good news is that there are strategies you can use that actually work. Here are the best tips to secure your brand's social media accounts and protect your business from online threats.
1) Perform A Social Media Security Settings Audit
Social media platforms store massive amounts of customer data and provide access to an established audience. Regular security audits help you identify and fix vulnerabilities before attackers exploit them.
Security audits are important because they protect your business in multiple ways:
- They reveal weak points that hackers could leverage to breach your accounts.
- They ensure you meet data protection requirements like GDPR and CCPA, avoiding costly fines.
- They test your crisis response readiness before an actual emergency strikes.
- Regular audits strengthen both your security posture and brand integrity.
While monthly audits might not be practical, schedule them quarterly or biannually to maintain strong protection.
Review privacy settings across every social media platform and account tied to your organization. Check who can see your posts, contact you, and access your information. Update these settings as platforms roll out new features and stay up to date with platform-specific security updates.
2) Enable Multi-Factor Authentication (MFA)
.webp)
Multi-factor authentication adds a critical security layer that blocks unauthorized access even when passwords get compromised. According to research from CISA and Microsoft this simple step prevents 99% of automated attacks.
MFA works simply. After entering your password, you verify your identity through a second method, typically a code sent to your phone or generated by an authentication app. This extra step creates a barrier that stops most attackers cold.
In regulated industries, MFA might be legally required, not optional. Banks, healthcare providers, and financial services often mandate MFA to meet compliance standards.
Remember that these statistics apply to brute force attacks. Still, MFA remains highly effective but isn't foolproof. Watch for social engineering attacks where cybercriminals trick employees into revealing passwords or MFA codes through phishing emails, social media messages, or fake support calls.
3) Limit Access To Social Media Accounts
Every additional person with login credentials increases your security risk. More access points mean more opportunities for unauthorized activity, accidental mistakes, or security breaches.
Restrict access to trusted, authorized employees only. Clearly define who needs access and why. Marketing team members might need posting privileges, while executives only need viewing access for reports.
For teams managing social media, use a shared authentication method. This approach lets team members access accounts without sharing passwords. You maintain better oversight through role-based permissions and can instantly revoke access when employees leave your organizations.
Assign specific roles and responsibilities. Document who manages each account and from which devices. This insight helps you spot unusual activity quickly, so if someone logs in from an unexpected location, you'll know immediately.
Uncontrolled access leads to serious problems. One off-brand comment can go viral for all the wrong reasons, damaging years of reputation building. If you limit access, you’ll maintain control over your brand's voice, image, and security.
4) Always Use Strong Passwords
Strong passwords form your first defense line. Create passwords that are at least 14 characters long, mixing uppercase and lowercase letters, numbers, and special characters. Skip common words, predictable phrases, or personal information because these fall quickly to dictionary attacks.
You can create strong passwords manually or automatically. On one hand, manual creation works but requires significant effort to create and remember complex passwords for multiple accounts.
On the other hand, password managers offer the simpler and easier approach. These tools can generate complex, unique passwords for each account and store them securely. They eliminate the burden of remembering dozens of passwords while ensuring each one meets security standards.
Never reuse passwords across accounts. When one account gets compromised, reused passwords give hackers keys to your entire digital presence. Each account needs its own unique, strong password.
5) Monitor For Data Breaches
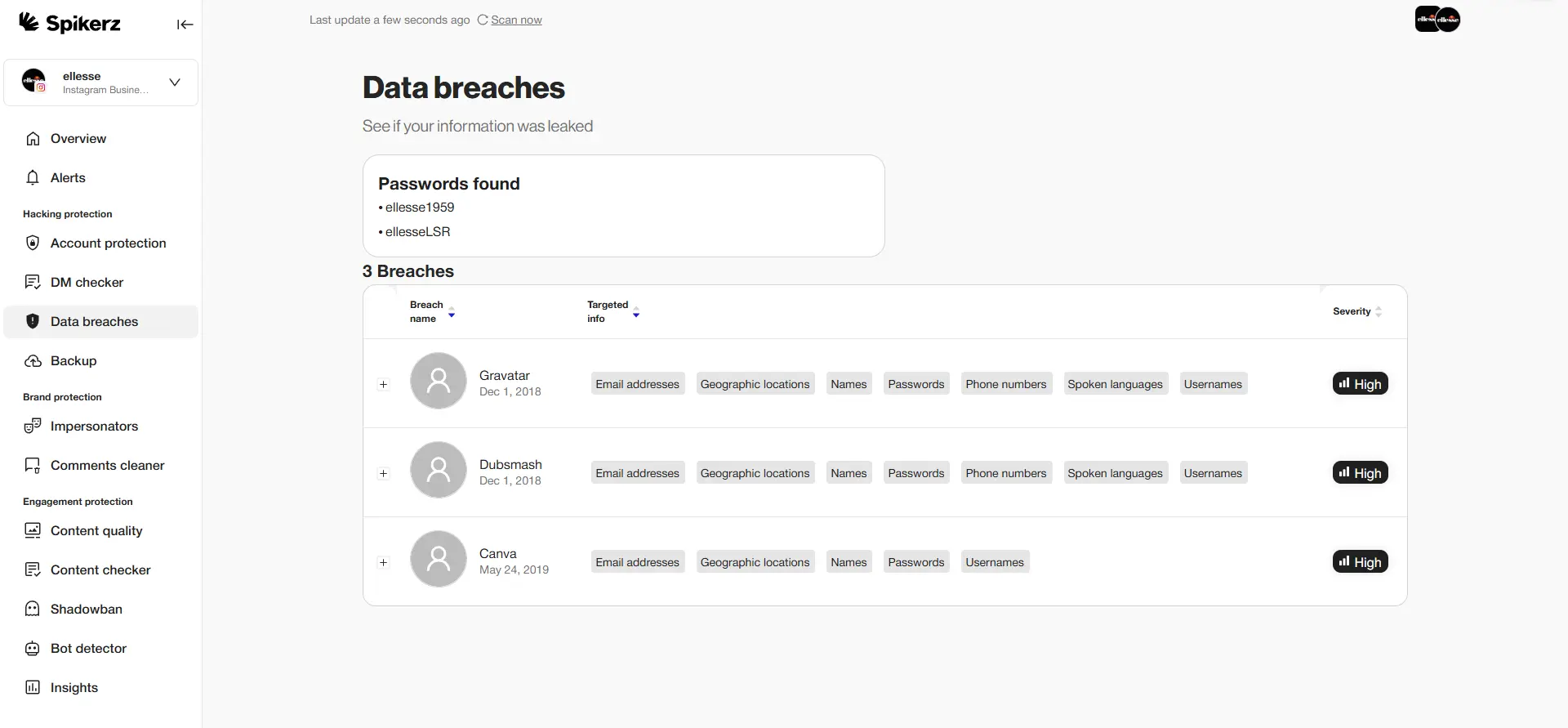
Proactive monitoring helps you identify and stop security breaches before they cause significant damage. When you detect there’s a data breach on one of the services you use, first identify which data was leaked and then immediately change your passwords and other data as needed. Your social media accounts are critical business assets that, when compromised, can devastate multiple areas of your operations.
A simple compromise can quickly escalate into a serious security incident affecting your entire business, so take it seriously and protect your email address, phone number, and passwords.
6) Regularly Review and Revoke Access To Third-Party Applications
Third-party apps expand your attack surface. Each connection is a potential vulnerability that cybercriminals can exploit to breach your accounts.
Unfortunately, these apps often request excessive account permissions that could be exploited. In other rare times these apps access data without proper consent, contain malware, or introduce compliance violations with regulations like GDPR or CCPA. The risk compounds over time.
Also, app developers can change ownership, update permissions, or suffer security incidents without notifying you. That's why regular reviews matter. Periodically audit which apps have access to your accounts and remove any you no longer use or need.
Lastly, verify that remaining apps follow strict privacy and security standards. Fewer connections mean fewer entry points for attackers. When you do that, you maintain better control over your data and reduce exposure to third-party vulnerabilities.
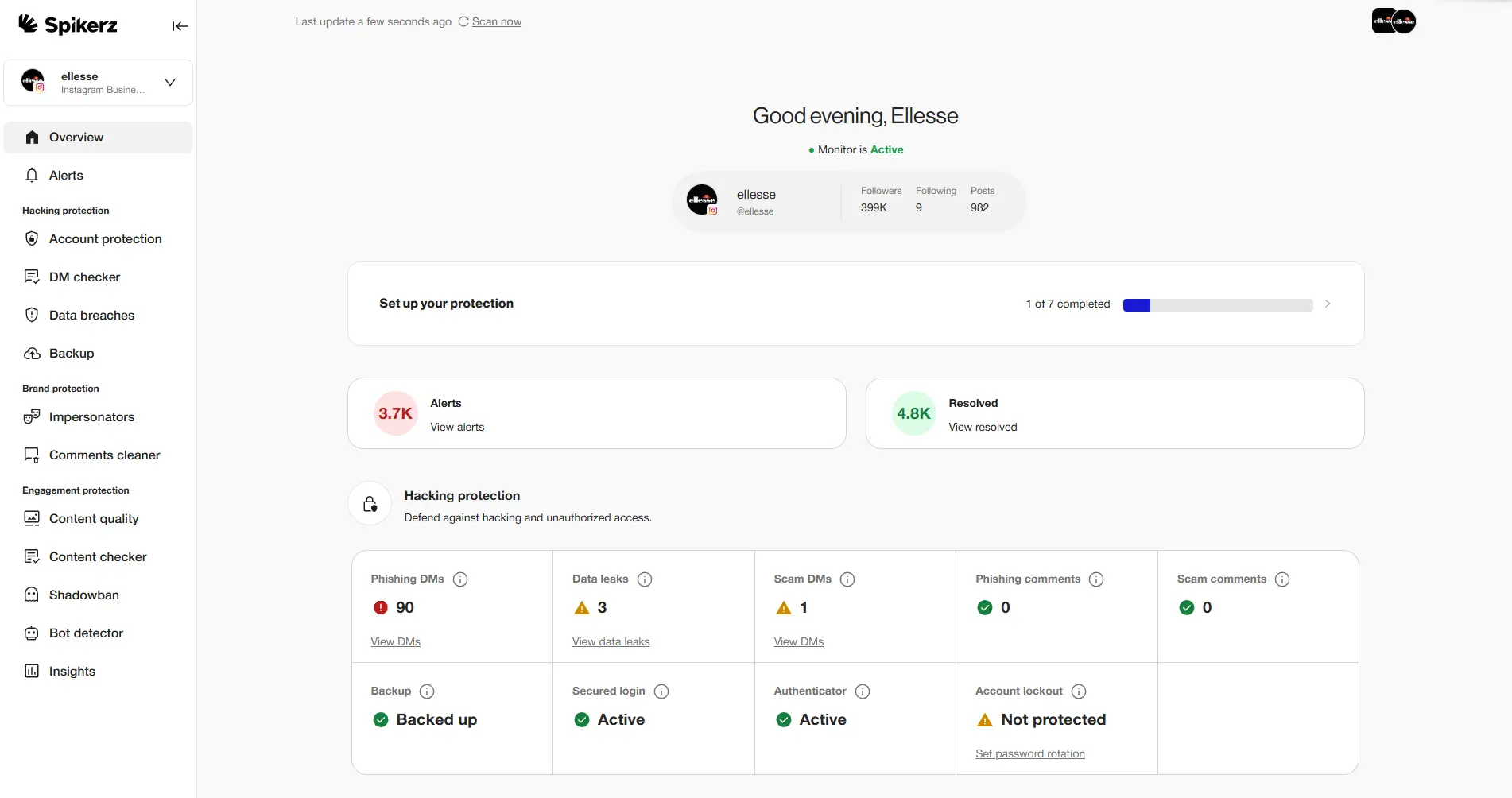
7) Set Up Account Activity Monitoring
Most compromises aren't immediately obvious. Attackers often maintain access for weeks or months, gathering intelligence, building follower lists for scams, or waiting for the perfect moment to strike.
Monitoring tools and platform features help you catch subtle red flags before major damage happens. Focus on these key areas:
- Review login history regularly for unfamiliar locations or devices.
- Track active sessions. Multiple logins from different countries often signal account sharing or compromise.
- Watch for behavioral anomalies like changes in posting frequency, engagement patterns, or sudden follower spikes.
- Use platform-native features like login alerts and unusual activity notifications, and ensure someone actually reviews them.
- For complete protection, tools like Spikerz handle the heavy lifting automatically. Spikerz monitors your accounts 24/7, detects intrusion attempts, blocks attacks immediately, and changes your password instantly to lock out unauthorized users.
Activity monitoring is especially valuable for businesses with multiple team members managing accounts. It ensures appropriate access use according to company policies and identifies when former employees still have access that should be revoked.
Ready to stop worrying about account security?
Give Spikerz a try. We monitor your accounts round the clock, block threats instantly, and handle password changes automatically when attacks succeed.
8) Educate Employees About Social Media Security
Human error is the weakest link in most security incidents. Employees' social media activities directly impact business security, making education key to protection.
Unfortunately, employees often blur lines between personal and professional social media use. They might post work-related content, location information, or company details without realizing the security implications. Personal posts can expose business information or create social engineering opportunities for attackers.
Training helps employees understand how their actions affect security. They learn to recognize threats and respond appropriately by reporting suspicious activity rather than ignoring or mishandling it.
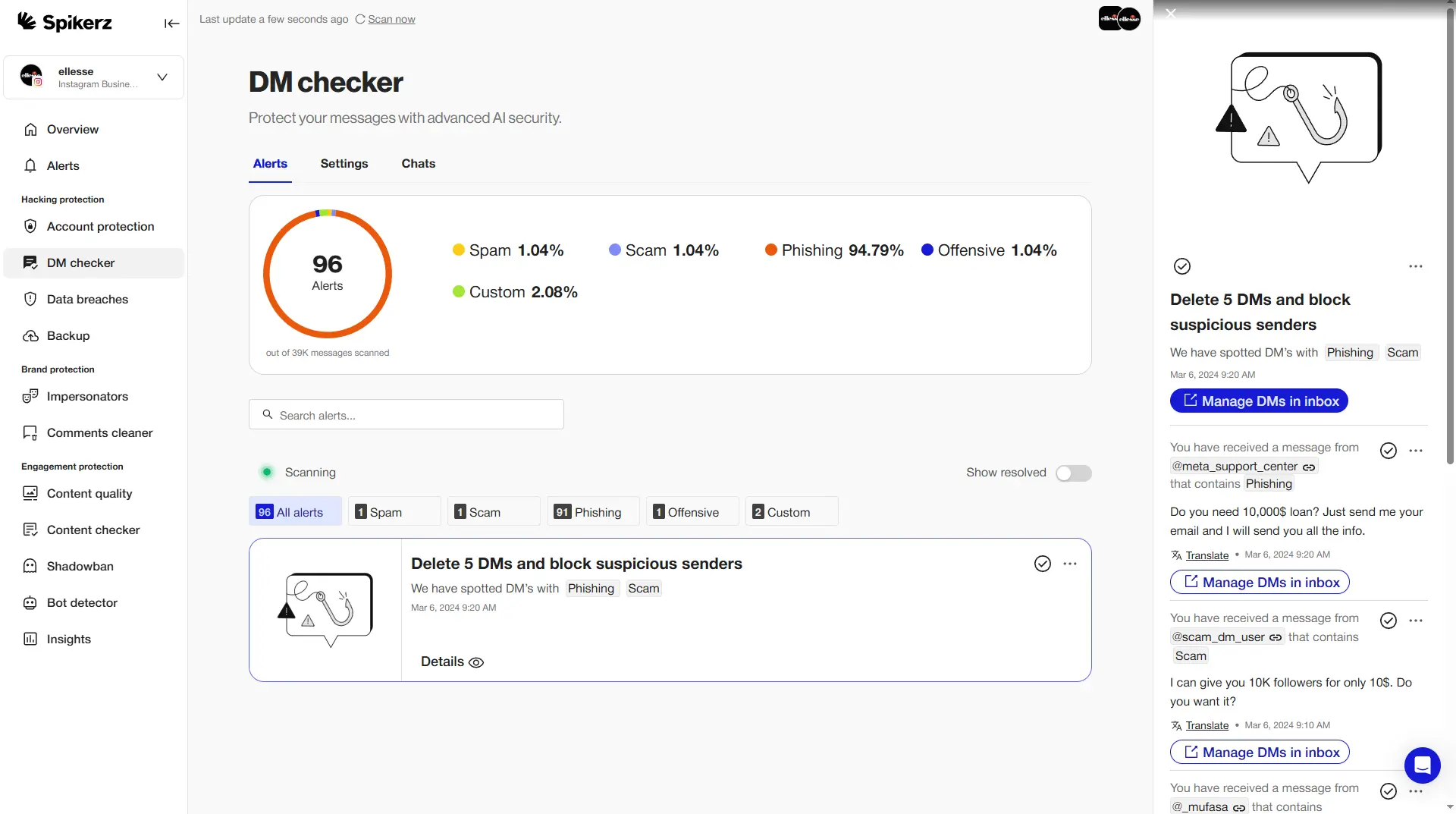
9) Be Careful With Links and Messages
Social media platforms attract phishing attacks, scams, and malware delivered through direct messages and comments. These attacks compromise accounts, steal sensitive data, and damage brand credibility.
Cybercriminals use advanced tactics to achieve this. For example, they create fake login pages to capture credentials, they disguise malware links as business inquiries, and they impersonate profiles to trick employees or customers into revealing sensitive information.
Platform safeguards catch some threats but miss many others. Social media companies can't detect every malicious message or link, leaving your accounts vulnerable.
Security tools designed specifically for social media protection fill this gap. Tools like Spikerz scan messages and accounts in real time, detect phishing attempts, and flag suspicious activity before problems develop. They automatically scan messages and comments for malicious content, keeping your communications safe.
10) Create A Social Media Crisis Management Plan
Social media incidents escalate quickly without proper response protocols. A crisis management plan ensures your business responds with speed, clarity, and control when security breaches happen.
Whether facing a data breach or account takeover, your plan should guide decisive action and effective communication. Quick, coordinated responses minimize damage and a speedy recovery.
Your plan should include clear roles and responsibilities: who makes decisions, communicates externally, and handles real-time monitoring. Document steps for account recovery and containment, including emergency contacts at social media platforms. Establish employee communication protocols to avoid mixed messages during sensitive times. And plan post-crisis recovery efforts, from rebuilding customer trust to conducting internal reviews that prevent repeat incidents.
11) Backup Your Social Media Content Regularly
Platforms can suspend or delete accounts for policy violations, automated detection errors, or mass reporting campaigns. Regular backups ensure years of content creation isn't lost due to platform decisions beyond your control.
If your account gets compromised and content deleted or altered, backups ensure quick recovery with minimal disruption. Rebuilding from scratch based on memory or incomplete files can set your team back months.
Also, platform backup options are often limited. Manual downloads consume a lot of time and storage space (especially for large business accounts), and take forever to be ready. Instead, combine local backups with automated tools that manage backups across all channels. Tools like Spikerz let you backup and restore content quickly and securely, so you never lose your content and have peace of mind.
12) Protect Company Devices and Networks
Businesses should implement robust endpoint security for devices and networks accessing social media accounts. These access points are critical attack vectors that can compromise both social media presence and broader business systems.
Unsecured devices are vulnerable to malware that steals saved passwords, logs keystrokes, or hijacks active sessions. One compromised device can risk your entire social media presence.
Networks are just as important. Public Wi-Fi and unsecured business networks enable eavesdropping attacks. Employees logging into social platforms over unprotected connections may expose credentials and session data to interception. That’s why VPN use on public Wi-Fi is non-negotiable.
Also, mobile devices deserve special attention. Many businesses manage social media from phones or tablets, but these devices often lack desktop-level security controls. They're susceptible to app-based malware, SIM swapping, SMS interception, and theft.
Conclusion
Your social media accounts face constant threats from hackers, scammers, and impersonators. But armed with these security strategies, you can build defenses that actually work.
The difference between businesses that survive cyber attacks and those that don't is preparation. Companies that implement robust security measures before attacks happen recover faster and suffer less damage. Those that wait until after a breach struggle to rebuild trust and reputation.
Don't gamble with your brand's digital presence. The cost of prevention pales compared to the price of recovery. Take action today: audit your settings, strengthen your passwords, enable MFA, and consider using specialized protection like Spikerz.
The question isn't whether your accounts will be targeted, it's whether you'll be ready when they are.



