Binance X Breach: 5 Lessons for Brand Protection
Binance X Breach: 5 Lessons for Brand Protection
Hackers have perfected the art of deception. They don't always break through firewalls or exploit complex vulnerabilities. Sometimes, they simply pretend to be someone you trust like your IT department, a vendor, or even a colleague sitting two desks away. This tactic, known as social engineering, tricks employees into handing over login credentials or clicking malicious links without realizing they've just opened the door to a breach.
Binance’s recent X account hack is a clear example of how quickly attackers can exploit this trust to damage your brand and deceive your customers. In this post, we'll break down what happened to Binance, examine the tactics hackers used, and share five practical lessons your business can use to protect your social media accounts from similar attacks.
What Happened To Binance's X Account?
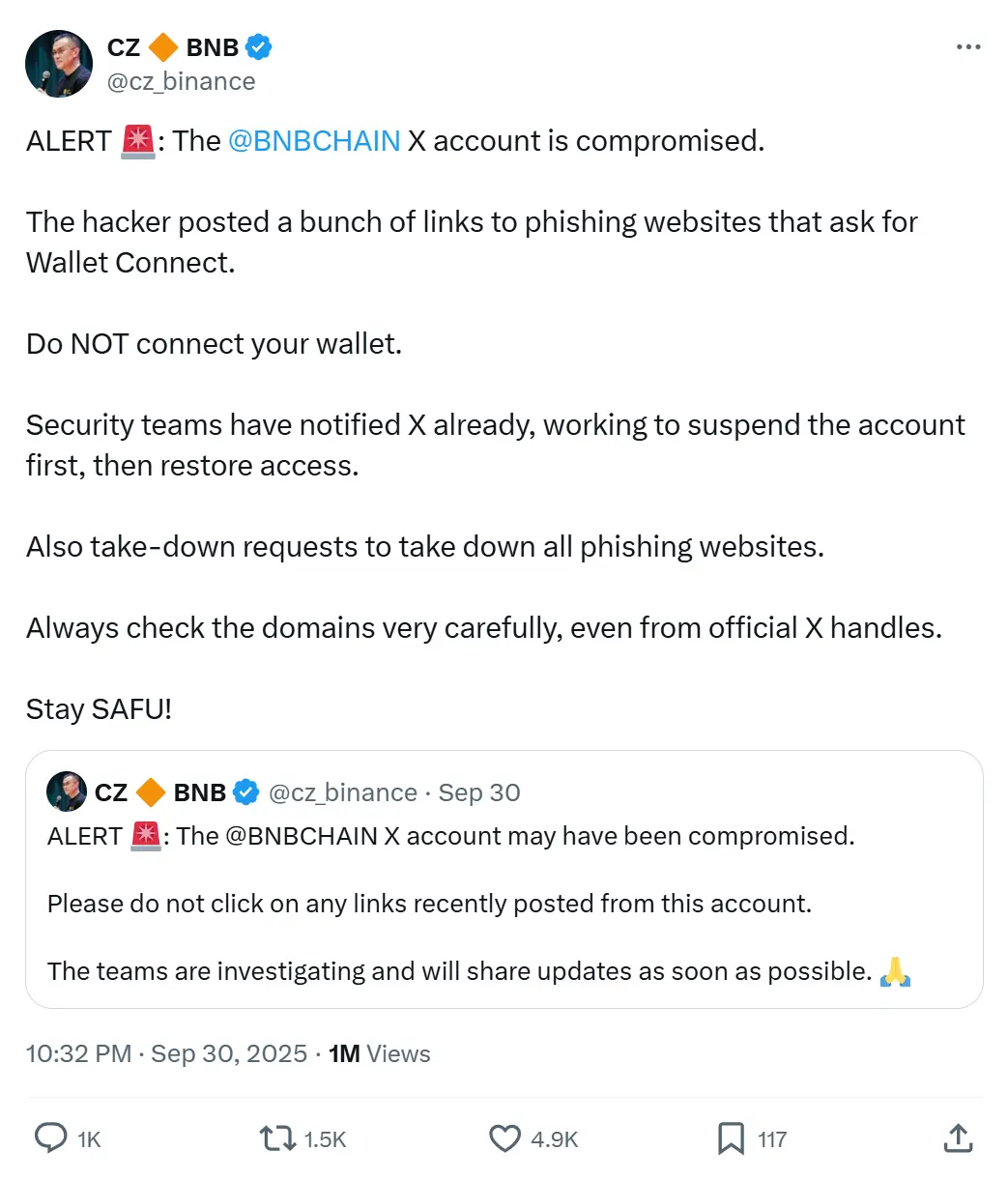
On October 1, Binance's official English X account for BNB Chain was hacked and briefly used to spread fraudulent "airdrop" links. The account promoted phishing scams disguised as WalletConnect prompts, tricking users into connecting their wallets and risking stolen funds.
However, former Binance CEO Changpeng Zhao (CZ) quickly responded from his verified account, warning users not to click on any links from the hacked handle. He confirmed the posts contained phishing material and said Binance had contacted X to suspend the account and filed takedown requests for the phishing domains. CZ also reminded the community to always double-check domains, even when they come from official accounts, and reinforced the importance of staying cautious online.
Thankfully, the damage wasn't big, with losses of about $13,000. CZ assured victims that they would be reimbursed, and noted that Binance's security teams are tracking the attacker, who may be identifiable through KYC.
How Can Businesses Protect Their X Accounts?
Protecting a social media account is quite simple. The goal is to create as many layers of protection as possible to reduce the attack surface hackers can exploit.
The best way to do this is to use a zero trust framework (a security approach built on the principle of "never trust, always verify"). This means treating every access request as potentially hostile, regardless of where it comes from.
That said, here’s what you can do right now to protect your social media presence:
1) Use A Strong Password
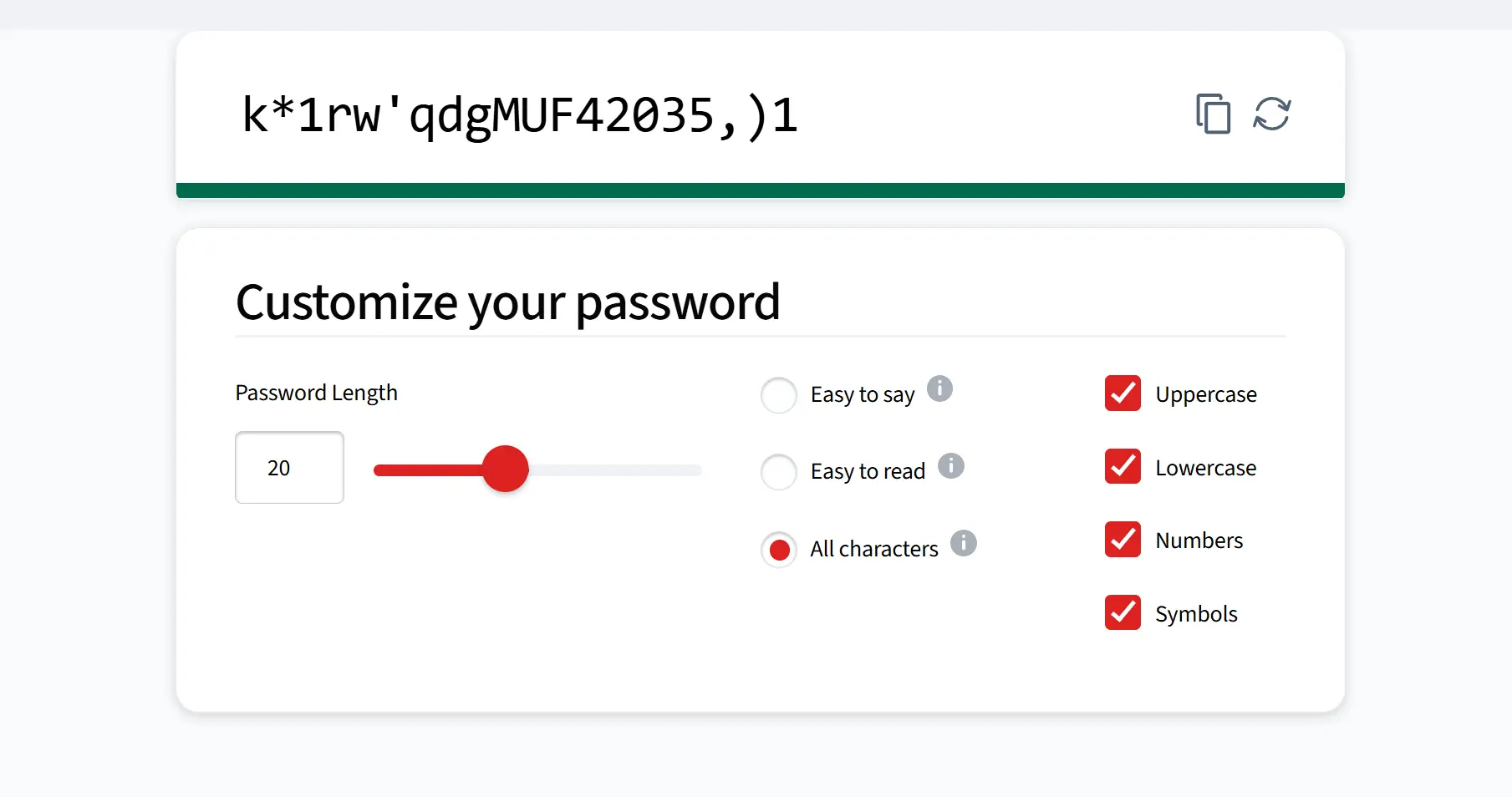
If your business manages multiple social media accounts, it's essential for you to use strong passwords for each account.
If you reuse the same one or rely on weak ones, it creates a single point of failure. If one account is compromised, then every other account that shares that password could also be in danger. And that not only puts your data at risk but also your reputation, your customer's trust, and the overall security of your operations.
Strong, unique passwords help prevent unauthorized access and keep your content and data safe. They are also important for compliance. Many industries require businesses to enforce strict password policies. If you fail to follow these rules, you could face penalties.
Another key reason to use strong passwords is protection against brute force attacks, where hackers use software to quickly guess password combinations until they find the right one. If you have simple passwords, these attacks can be done fairly quickly.
For all of these reasons, it's a must to have a complex, randomly generated password. You should have a password that has at least 14 characters, (though 20 or more is ideal), mix uppercase and lowercase letters, numbers, and symbols.
Important: Avoid dictionary words, personal details, or common patterns (hackers target those first). The best passwords are random, complex, and unique to each account.
2) Enable 2FA For Teams
Two-factor authentication, or 2FA, is one of the simplest and most effective ways to secure accounts. Research by CISA and Microsoft, found that enabling multi-factor authentication prevents 99% of automated attacks.
2FA for teams takes this concept further. Instead of sending codes to one person's phone, access is centrally managed in a dashboard so multiple team members can securely use the same account. As an Admin, you decide who gets access, and if someone leaves your organization or changes roles, their access can instantly be revoked without disrupting the rest of the team.
This is incredibly useful for teams managing social media accounts like X. When team members have to request login codes, it disrupts their workflow. As a result, they end up wasting a lot of time and have to bother other teammates to be able to do their job. 2FA for teams fixes that.
3) Enable Account Monitoring
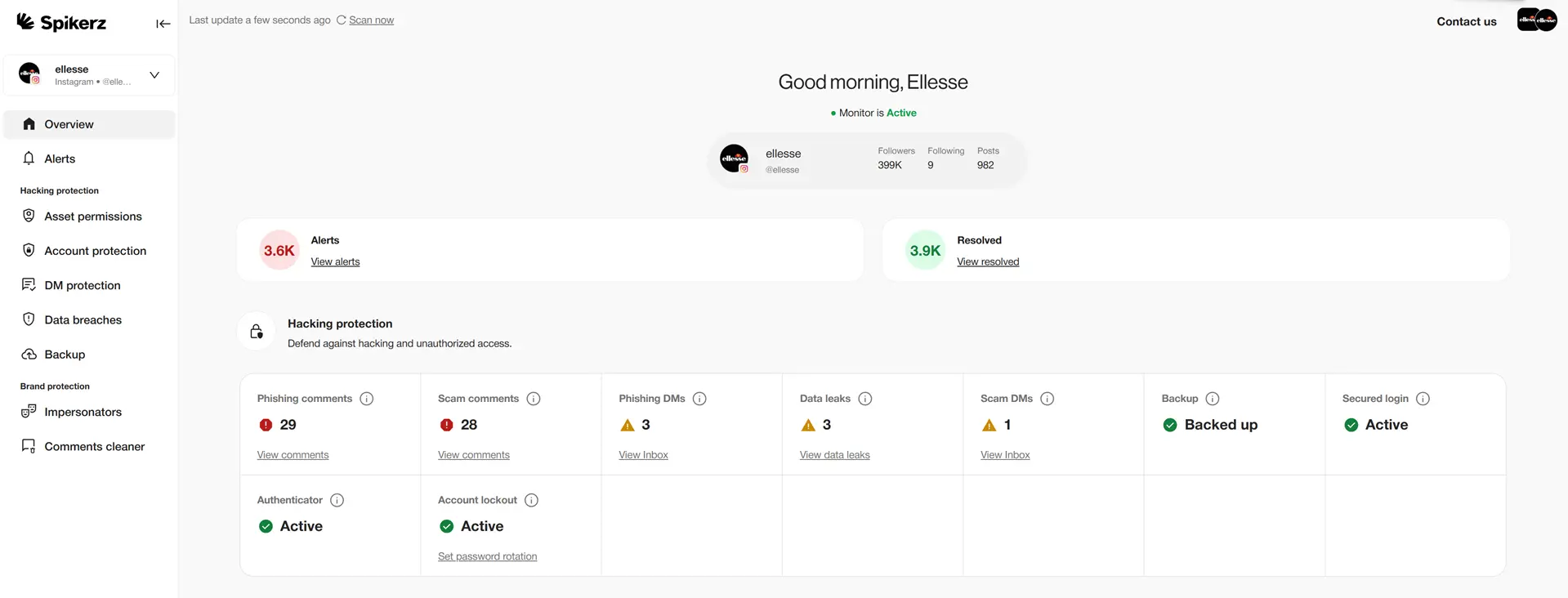
Account monitoring is the process of regularly reviewing an account's activity to detect suspicious actions, prevent fraud, and quickly remove intruders. Social media platforms can handle some monitoring for you, or you can do it manually. This may be fine for personal use, but if you're running a business, especially with multiple accounts, it’s much better to use a third-party tool that centralizes your security and strengthens your defenses.
For example, social media security tools are built for that. They continuously scan accounts for threats, catching unusual login attempts, suspicious messages, or sudden spikes in activity before they turn into real problems.
One of these specialized solutions is Spikerz. It protects your accounts from phishing, bot attacks, and other forms of social engineering attacks by monitoring login patterns, unrecognized access, permission changes, and breaches in real time.
The best thing is, there are clear benefits for businesses. Spikerz automatically removes intruders, resets compromised passwords, and sends instant alerts during a breach. It provides automated backups for quick recovery, filters out spam and offensive content, and ensures posts comply with platform policies so you avoid limitations or shadowbans.
If this sounds like it would be beneficial to your business, create a Spikerz account right now. The cost of recovering from a social media hack is far higher than investing in your security.
4) Use Antivirus Software
Antivirus software provides essential protection for organizational devices against malware, including keyloggers, compromised applications, and other local security risks that increase your attack surface.
When you use antivirus protection, you add layers of defense that reduce the chances of a successful attack. Browser extensions and local file monitoring systems play a big role here, scanning for suspicious activity patterns during web browsing and analyzing downloaded files for hidden malicious code.
The goal is to create as many barriers as possible between your systems and potential threats. Antivirus software is a straightforward, effective way to minimize risks and keep sensitive information safe.
5) Train Your Employees To Recognize Phishing Attacks
Employees are always the weakest link in any security framework. This isn't because they intentionally undermine security but because human factors like fatigue, distraction, or lack of awareness make them vulnerable to mistakes.
Most employees struggle to recognize phishing attempts. That's why proper training is essential. When you give your team the knowledge and tools to spot suspicious messages, you reduce the chances of a successful attack.
But training shouldn't be a one-time event. Regular sessions and ongoing testing keep employees sharp and aware of new tactics attackers use. Live phishing tests can also show you where weak spots are, allowing you to provide targeted support and reinforce security where it's needed most.
Conclusion
Binance’s X breach highlights a harsh reality: no brand is too big or too secure to be hacked. If an organization with Binance's resources and expertise can fall victim to social engineering, it's a wake-up call for every business.
The five lessons we covered aren't just security recommendations. They're essential layers of defense that work together to protect your brand from attackers who grow more sophisticated every day. Each layer closes gaps that hackers exploit, making your accounts exponentially harder to breach.
Don't wait for a crisis to take security seriously. It’s time to strengthen your defenses. Don’t wait until you become the next cautionary tale in the business community.



