5 Esports Giants Hacked: Are You Making the Same Mistake?
5 Esports Giants Hacked: Are You Making the Same Mistake?
One shared social media manager. One phishing link. Five compromised YouTube channels. That's all it took to simultaneously hijack the accounts of some of gaming's biggest brands.
In this post, we'll examine what happened to these esports organizations, how attackers exploited shared access points, and the 11 security measures you need to implement right now to protect your YouTube presence.
What Happened To Dota 2, Esports World Cup, BLAST Premiere, PGL, and ESL Counter-Strike?
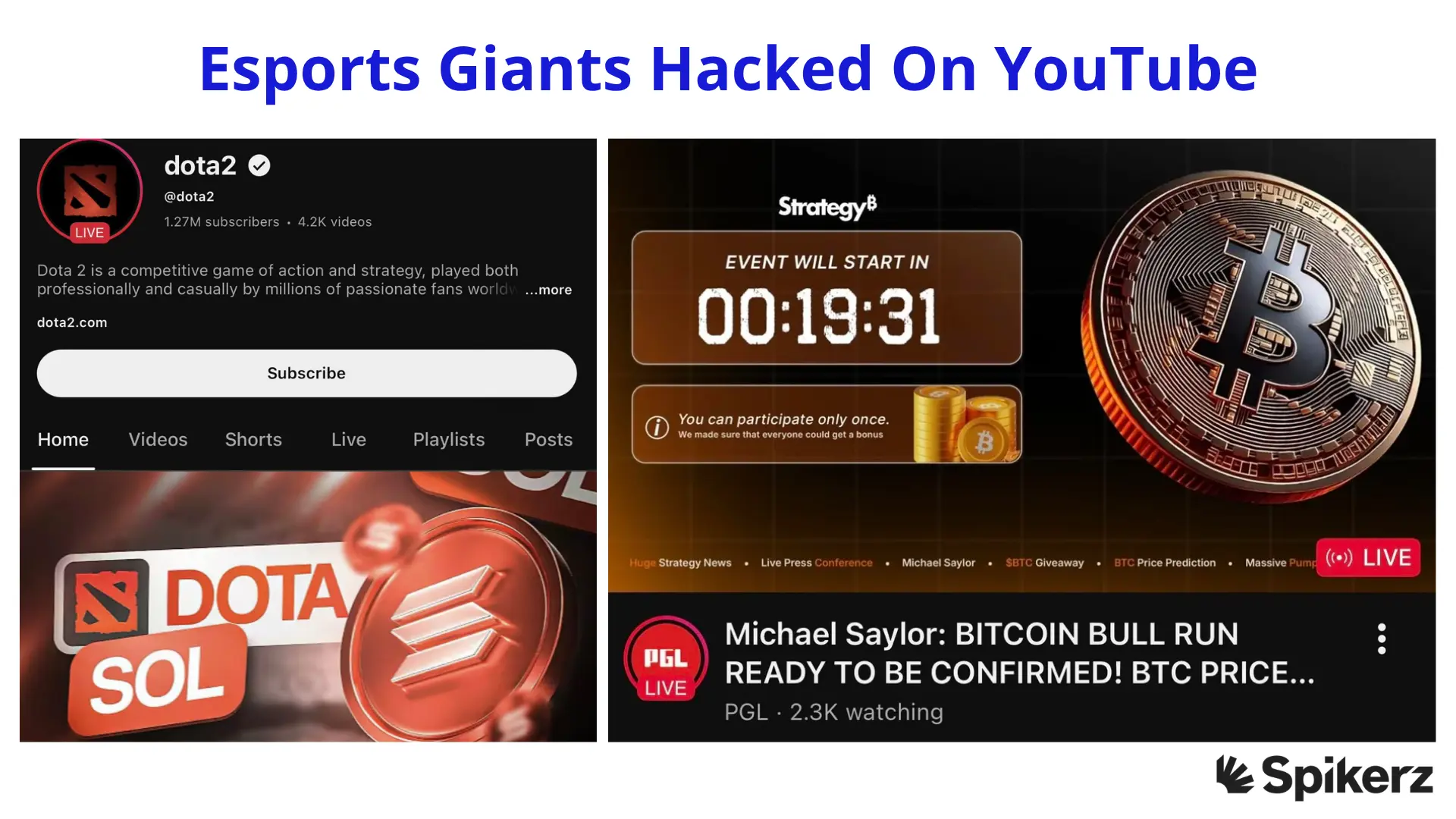
On October 15, major gaming YouTube channels, including Esports World Cup, ESL Counter-Strike, BLAST Premier, dota2, and PGL, were all simultaneously hit by a large-scale hack. The attackers took control of these accounts and began streaming fake live videos promoting a fraudulent Solana-based "ESL CS2 Memecoin."
The streams featured an old recording of Gabe Newell discussing the Steam Deck, with a QR code that led to a phishing site. The same video was broadcasted across multiple channels at the same time, including the ones that are dedicated to Counter-Strike and Rainbow Six Siege.
In just a few minutes, one of the streams reached more than 60,000 views before being taken down. Anyone who scanned the QR code or clicked links in the chat was redirected to a fake crypto page asking them to connect their wallets. Thousands of gaming fans were exposed to this scam before the channels regained control.
But the breach didn't stop there. The official dota2 and PGL YouTube channels were also hijacked and used to promote another Solana-based meme coin. Hackers launched a fake stream titled "Dota 2 Launch Official Meme Coin – Hurry Up," linking to a token on PumpFun with a market cap of only about $5,000. One wallet held more than 98% of the total coin supply, revealing that it was a scam.
PGL's channel was also misused to post a fake livestream featuring a deepfake of Michael Saylor talking about cryptocurrency, which drew over 2,000 viewers before being removed.
All affected channels acted quickly and removed all the fake streams and restored control. YouTube also experienced a major outage on the same day, which may have complicated recovery efforts.
How Were Attackers Able To Gain Control Of All These YouTube Channels?
According to an article by Mnmzzz for Dust2.us, the problem may have started with a shared group of contractors who manage social media for these organizations. It seems that someone with admin access, like a social media manager, was targeted and their account was used to compromise the rest of the YouTube channels.
Something similar happened two years ago to Linus Tech Tips (LTT). In that case, the attackers got around normal security measures, including passwords and two-factor authentication. The hack started early in the morning when the Linus Tech Tips channel was renamed to "Tesla" and began streaming fake cryptocurrency giveaways featuring Elon Musk.
The hackers didn't steal the passwords or 2FA codes. Instead, they stole a session token, which is a small file that keeps you logged into websites without having to enter your password again. Session tokens allow your browser to maintain authentication without repeatedly requesting credentials, but if stolen, they give attackers complete access to your accounts.
One of Linus's team members unknowingly downloaded a "sponsorship offer" that contained malware. Because of that, attackers accessed the account and took control of the channel. They used it to stream scam content and deleted videos before YouTube eventually shut it down.
The same method seems to have been used in the recent esports channel hacks. The attackers went after the people who had access to multiple channels. Once one account was compromised, they could move across the network and reach other connected accounts.
How Can Brands Protect Their Youtube Channels?
The best way to protect your YouTube channel is to create as many layers of protection as possible and reduce your attack surface through employee training and minimizing attack vectors.
The whole point is, each layer you add makes it harder for attackers to succeed. And when one security measure fails, the others are there to catch what slipped through.
1) Create A Unique, Strong Password For Your Accounts
Passwords are the first layer of defense for your online safety. They protect your accounts and sensitive information from unauthorized access, data breaches, and identity theft.
For example, against brute-force attacks, complex, unique passwords make it so attackers' software take significantly longer to succeed (if you create the right password, it'll make it impossible for them to succeed with this method). Or against credential stuffing, a successful breach on one won't let hackers access the rest of your accounts.
The most effective way to create a strong password is to focus on length and randomness. Avoid using personal information, common dictionary words, or sequential patterns.
The best passwords use a minimum of 20+ characters. The longer it is, the stronger it is. It should also be diverse, using a mix of uppercase letters, lowercase letters, numbers, and symbols.
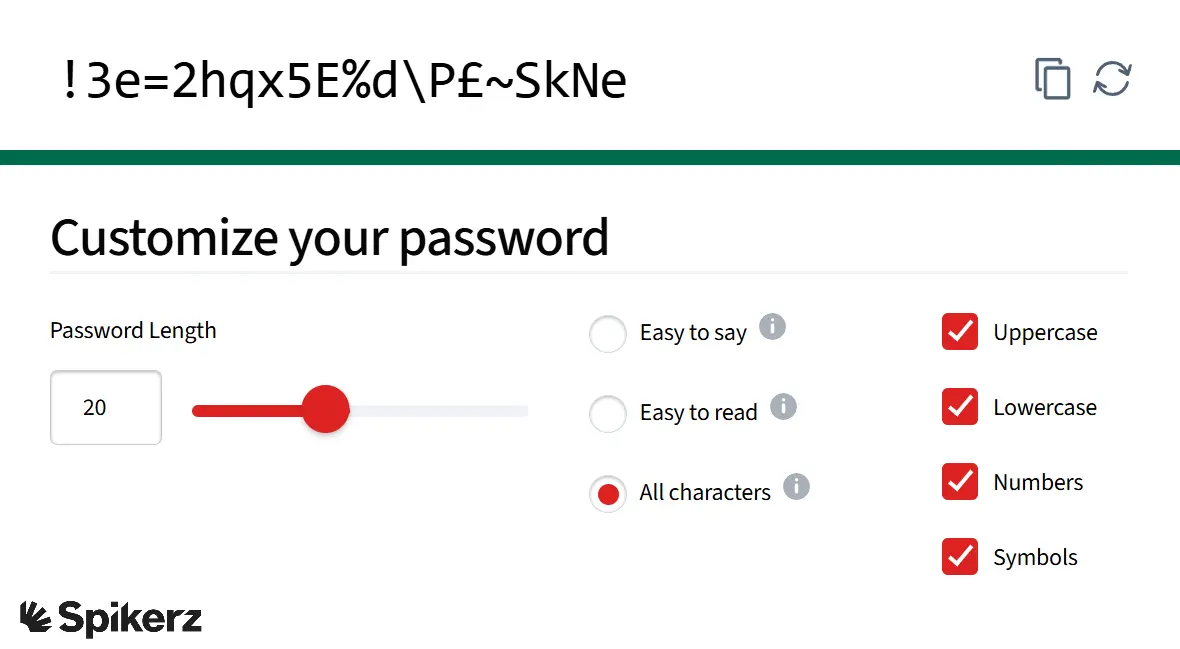
If you're generating it manually, combine many random, unrelated words into a long, memorable phrase with numbers and en dashes like Trace0-Thrill3-Ranting4-Catchy2-Glorifier4.
Or you could use a password manager to create a long, completely random string of characters like H7$JVq&kdRRfb6TwUans. Password managers are awesome because they eliminate the need to remember dozens of complex passwords while keeping your accounts secure.
2) Enable 2-Step Verification On All Accounts
Enabling 2-Step Verification on your account is very simple and one of the most effective ways to protect your personal information. It gives you a second line of defense, keeping your account safe even if your password is stolen. It also saves you the time and stress of recovering a hacked account or dealing with identity theft later.
Once 2-Step Verification is set up, you'll sign in using your password and a second step, or with a passkey. Depending on your situation, Google may ask for different types of verification to make signing in easy and keeping hackers out.
To turn on 2-Step Verification:
- Open your Google Account and go to “Security & sign-in.”
- Under How you sign in to Google, select “Turn on 2-Step Verification.”
- Follow the on-screen instructions to complete the setup.
The entire process takes less than five minutes but provides lasting protection.
3) Use Antivirus Software To Scan Local Environments
Antivirus software is a program that's designed to detect, block, and remove malicious software from your computer. It scans files and your system's memory for patterns that match known threats, like viruses and other forms of malware.
Modern antivirus solutions also use behavioral analysis to identify suspicious activity (even from previously unknown threats). For that reason, you should strongly consider using antivirus software on all your local devices to protect them from malware, especially infostealers.
Infostealers are a type of malicious software that secretly collects sensitive information from your system. They can steal login credentials, credit card numbers, Social Security numbers, personal information, browser history, emails, and even crypto wallet information. Some can also take screenshots or copy files without your knowledge.
These types of attacks often come from phishing emails, infected websites, or unsafe software downloads. Once installed, infostealers can compromise your privacy and lead to identity theft, account takeovers, or financial loss.
In fact, a 2024 report from Constella Intelligence revealed that more than 500 million devices in 2023 were infected, resulting in nearly 2 billion stolen records containing sensitive data. That's why you should keep antivirus software active and updated to ensure your devices are continuously scanned and protected. Regular scans catch threats before they can do damage.
4) Regularly Train Employees On Cybersecurity Best Practices
Regularly training employees on cybersecurity best practices is one of the best ways to protect your business from data breaches. The reason is, people often are the biggest risk to a company's security. This is supported by the Verizon 2021 Data Breach Investigations Report.
It found that 85% of breaches involved a human element, with phishing being responsible for 38% of them. This means that even the best security tools can't stop an attack if employees don't recognize the signs of a threat. Technology alone can’t compensate for human vulnerabilities.
And what's worse is that human error is inevitable. Employees handle large amounts of data, use multiple applications, and communicate across different platforms, which creates more opportunities for mistakes or oversights. Even well-intentioned staff can accidentally click malicious links or fall for social engineering tactics.
That's why consistent cybersecurity training must be a high priority. If employees know how to identify phishing attempts and understand social engineering tactics, they're far less likely to fall for them.
Also, an engaging and ongoing security awareness program helps transform employees from potential weak spots into a strong defense for you. It gives them what it takes to recognize suspicious activity, protect their credentials, and respond effectively in real-world scenarios.
5) Monitor For Suspicious Activity And Unusual Login Patterns
Monitoring your social media accounts for suspicious activity is the best way to protect your brand. Hackers often target social media to spread scams, steal information, or damage reputations. We've seen this many times across the web, in fact, this month alone, we've reported on nine high profile social media account hacks.
The good news is that we can use behavioral analytics to protect accounts from breaches like these ones. They identify abnormal patterns that may signal fraud, hacking attempts, or data breaches. If you know what normal activity looks like, you can detect changes quickly and take action before anything happens.
There are many benefits to doing this. For example, behavioral analytics allows proactive monitoring to detect risks early, continuous adaptation to threats, and insider threat detection to catch suspicious activity (even from trusted users). This way, you can catch threats that traditional security measures might miss.
That said, a complete social media security strategy should include strong passwords, malware protection, regular account reviews, user training, and clear response plans. The reason for this is, prevention is always better than recovery, and consistency is the key to keeping your accounts secure. Security is not a one-time project but an ongoing commitment.
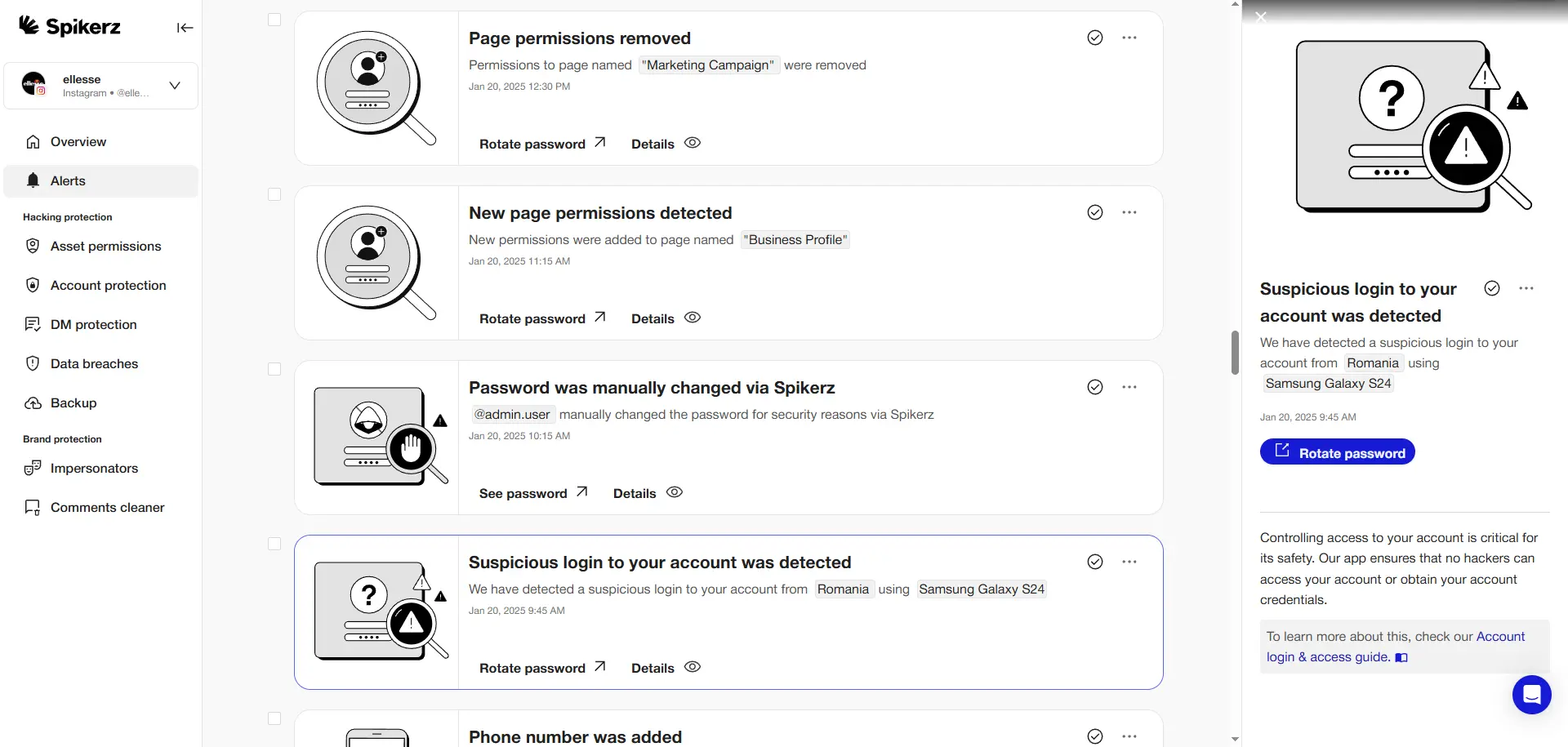
The good news is, Spikerz makes this process simple. It gives you the tools to monitor your social media accounts for suspicious activity, track unusual login patterns, and detect compromised accounts. Also, by taking advantage of behavioral analytics, Spikerz continuously learns your account's typical behavior, helping you spot irregularities in real time.
With its alerts and insights, you can take immediate action to keep your online presence safe, secure, and one step ahead. Ultimately, Spikerz gives you peace of mind in knowing your accounts are protected while you focus on creating content and growing your business.
6) Avoid Unzipping Email Attachments
You must avoid unzipping email attachments at all cost, especially if they're unexpected or look suspicious. They can hide malware, spyware, or ransomware that compromises your computer and steals your data. Cybercriminals often use zip files to bypass security filters and trick users into opening them.
Email attachments are a common way for hackers to launch attacks. For example:
- Malware can infect your device when downloaded, giving attackers access to your local files and accounts.
- Phishing emails often use fake addresses to trick you into opening infected attachments that steal personal or financial data.
- Ransomware can encrypt your files and demand payment to restore them.
- Zero-day attacks exploit unknown software vulnerabilities through attachments, causing serious breaches.
Each of these attack vectors has caused millions of dollars in damages to businesses worldwide.
A clear example of why you should never unzip email files is what happened to Linus Tech Tips (LTT). As we mentioned above, the team received what looked like a legitimate sponsorship email from a potential partner. It appeared harmless, so one of their team members unzipped the file and opened what seemed to be a PDF with the deal's details.
Within 30 seconds, malware installed itself and accessed all user data from the person's browsers, including saved passwords, cookies, and session tokens, allowing attackers to hijack accounts without needing credentials or two-factor authentication. This single mistake compromised multiple channels and took days to fully resolve.
7) Always Double Check File Extensions Before Executing Them
This isn't optional. You must always double check file extensions before opening a file. Extensions tell your system what kind of file it is and which app should open it. Most have three letters, like .exe, .txt, or .dll, though newer ones like .docx or .xlsx can be longer.
Knowing common extensions helps you spot suspicious files quickly. File extensions are the first indicator of whether a file is safe or potentially dangerous.
Attackers often exploit malware by manipulating extensions. They might use double extensions like example.jpg.exe to make a dangerous file look harmless. Since Windows often hides known extensions, you may only see example.jpg and think it's an image.
This is a common trick in email attachments, where a file like Evil.txt.exe appears as Evil.txt. The first extension (.txt or .jpg) looks safe, but the second (.exe, .Ink, .hta, .scr) reveals its true nature. Attackers count on users not checking beyond the visible extension.
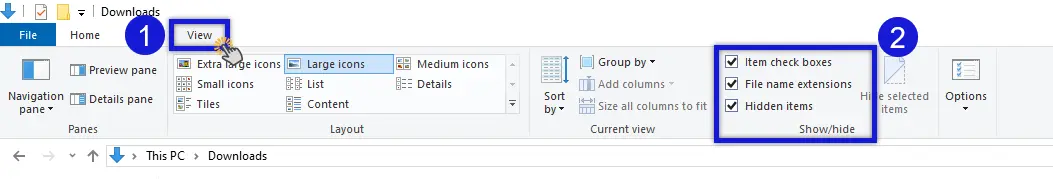
To stay safe, make sure your system shows full file extensions so you can verify what you're opening. Avoid executing any file that ends with a potentially dangerous extension unless you're certain it's safe. When in doubt, verify the file's authenticity with the sender through a separate communication channel.
This is something that antivirus software can also help with. It adds more protection by detecting and blocking hidden threats. Modern tools can identify malicious behavior, stop suspicious downloads, and prevent attacks that exploit vulnerabilities or steal data.
For example, technologies like Network Threat Prevention can spot double-extension attacks and block them before they cause any damage. Having multiple layers of protection significantly reduces your risk of falling victim to these attacks.
8) Implement An Incident Response Plan To Quickly Address Any Potential Breaches
A Cyber Security Incident Response Plan is a written document that outlines how an organization will detect, respond to, and recover from potential security breaches or cyber threats. It defines clear roles, responsibilities, and procedures to protect the confidentiality, integrity, and availability of important information assets. Without this plan, teams waste critical time deciding what to do during active breaches.
Having this plan in place helps protect sensitive data, maintain customer trust, and keep business operations running smoothly. It also enables companies to act quickly during an incident, minimize damage, prevent data loss, and reduce financial impact.
To sum up:
A well-developed incident response plan supports compliance and helps avoid potential legal issues. And when they're combined with secure development practices and a zero trust framework, it improves cybersecurity resilience and ensures business continuity.
9) Perform Regular Security Audits And Penetration Testing
A cybersecurity audit is a structured review of your organization's security measures, policies, and procedures. It helps you identify weak spots in your systems and prevent data breaches.
Regular security audits and penetration testing help you understand your organization's specific cyber risk environment so you can build a clear roadmap to prioritize and reduce those risks. When you examine your networks, systems, and applications, you reveal vulnerabilities that hackers might exploit, whether they're targeting your social media accounts, internal systems, or the data behind them.
Consistent audits also strengthen your overall security posture. They allow you to assess the effectiveness of your current security controls, ensure regulatory compliance, and adapt to emerging threats. Most importantly, they give you the confidence that your organization's data, systems, and online presence are well-protected against cyber threats.
10) Limit Access To Your YouTube Accounts Based On The Principle Of Least Privilege
The principle of least privilege is about giving people or systems only the access they truly need to do their work. It helps reduce the risk of unauthorized access, data misuse, or accidental changes. This fundamental security concept prevents the cascade failures we saw in the esports hacks.
When this principle is applied to your social media, for example YouTube accounts, it protects your business from unnecessary exposure. Too many people with access increases the chances of mistakes, leaks, or even security breaches. In essence, each additional person with admin access multiplies your attack surface.
That said, access management isn't something you set up once and forget. As your team grows and roles shift, you need to regularly review who has control over your accounts. Employees leave, contractors finish projects, and responsibilities change, but access permissions often remain unchanged.

Spikerz makes the whole process simple. It lets you see exactly who and what has permission to your YouTube accounts, helping you spot unnecessary or outdated access. And when someone leaves your organization or no longer needs access, you can revoke their permissions right away.
11) Backup Your Content Regularly
Backing up your content is essential as data loss can happen to anyone (small businesses are especially vulnerable). Without a strong backup system, one mistake, cyberattack, or hardware failure can erase months or years of hard work.
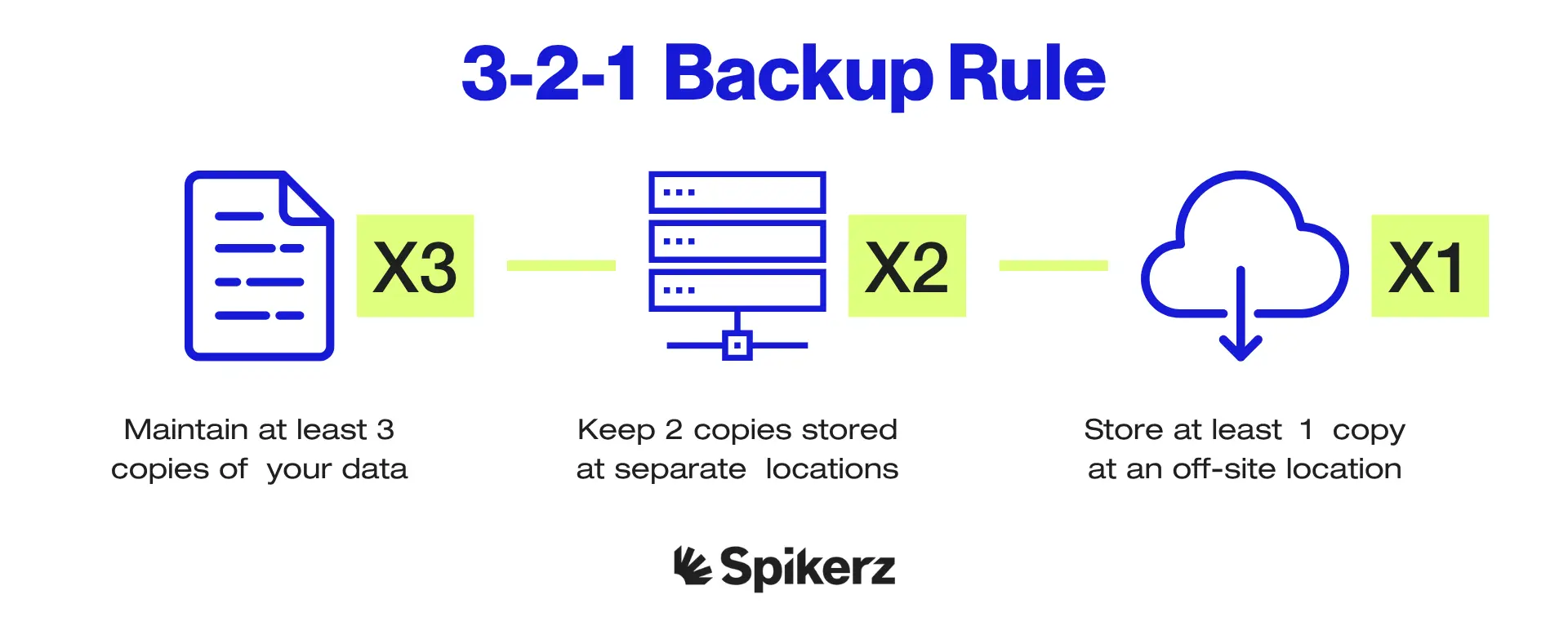
But the good news is that the 3-2-1 backup strategy is one of the easiest and most effective ways to protect your content. It involves keeping three copies of your data, storing them on two different types of media, and keeping one copy off-site. All of this ensures that if one backup fails or becomes corrupted, you still have other copies available.
Businesses of all sizes use this method because it's simple, reliable, and scalable. And if you need help with your digital copies, Spikerz automatically backs up your content. It continuously monitors your YouTube account and automatically archives everything you upload or share publicly.
Each piece of content is stored securely in the cloud, using advanced encryption to keep your files private and protected, and ensuring your videos stay safe from accidental deletion, hacks, or platform errors.
Conclusion
The esports YouTube hacks weren't just sophisticated technical exploits. They were the result of excessive permissions and shared access that created a single point of failure across multiple organizations. When attackers compromised one person with admin rights, they gained control of five major channels simultaneously.
This demonstrates a crucial truth: your security is only as strong as your weakest access point.
Don't wait for a breach to take security seriously. All these organizations learned this lesson the hard way, but you don't have to. Start implementing these protections now, beginning with the most critical: limiting access based on the principle of least privilege and enabling comprehensive monitoring.



