Why Celebrity Hacks Are Your Company's Wake-Up Call
Why Celebrity Hacks Are Your Company's Wake-Up Call
Social media hacks have become a daily occurrence, affecting everyone from Fortune 500 companies to A-list celebrities. These breaches aren't rare events that happen to "other people," they're systematic attacks targeting anyone with a valuable online presence.
Jesse Williams is just the latest victim in an endless stream of high-profile social media compromises. However, what makes his case particularly disturbing is that his account wasn't hijacked to sell cryptocurrency, spread political propaganda, or launch phishing campaigns. Instead, the hackers took control "for fun," posting crude content that damaged his reputation purely for their own entertainment.
This shift toward recreational hacking is troubling to say the least. When attackers no longer need financial motivation to target your accounts, every business becomes a potential playground for malicious actors.
In this blog post, we’ll examine what happened to Jesse Williams' X account, explore why companies and influencers continue falling victim to these attacks, and provide six actionable strategies you can implement today to protect your business from similar breaches.
What Happened To Jesse Williams' X Account?
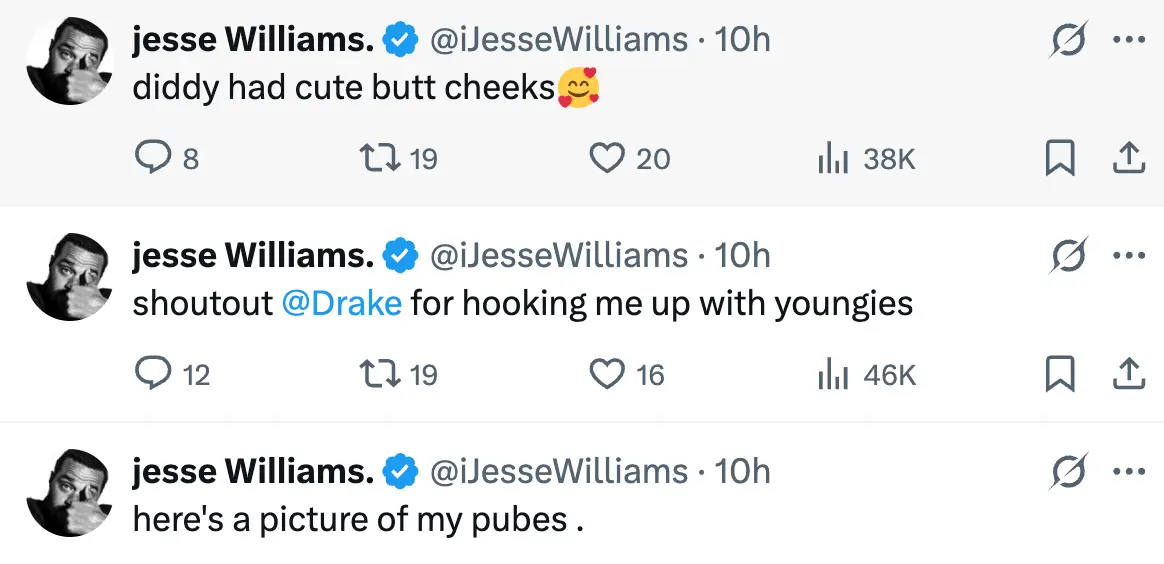
On June 8, 2025, Jesse Williams was hacked on X. The former Grey's Anatomy actor lost control of his account to hackers who used his platform to share inappropriate content and offensive jokes.
What made this hack especially concerning wasn't the scale or sophistication of the attack. The hackers didn't use Williams' account to promote cryptocurrency scams, share political misinformation, or distribute ransomware like most attackers do.
Instead, the account was hijacked to share crude messages involving nudity and inappropriate jokes about race and pedophilia. The hackers transformed his professional platform into a vehicle for offensive content that could damage his career and reputation.
Hacks like this one aren't new, they happen all the time across all platforms. Last month alone, we documented at least 12 high-profile account breaches and we know of thousands of lower-profile attacks targeting businesses and individuals worldwide.
This attack was seemingly executed for pure entertainment value, which is a more worrying trend than traditional profit-driven cybercrime. When hackers no longer require financial incentives to target your accounts, the threat landscape becomes unpredictable and far more dangerous.
The question that haunts every business owner watching these attacks unfold is simple: if celebrities with resources and technical teams can't stay protected, how vulnerable is my company?
Why Do Companies And Influencers Keep Getting Hacked?
High-profile social media accounts get compromised for many reasons, but in our experience, there are trends that always show up. Understanding these common security gaps helps explain why even well-funded organizations continue falling victim to relatively simple attacks.
This pattern is consistent across industries and account sizes. Most breaches result from common security vulnerabilities, not sophisticated hacking techniques.
Using Low Quality Passwords
Passwords are your first line of defense against unauthorized access, and they play a critical role in protecting accounts from brute force attacks. Weak passwords essentially hand hackers the keys to your social media without requiring them to break down the door.
Creating a strong password isn't difficult, but many users still rely on easily guessable combinations that provide minimal protection. Hackers use automated tools that can test millions of password combinations per minute, making simple passwords vulnerable.
That's why you should take password security seriously and create complex combinations that can withstand automated attacks.
Reusing Passwords
The biggest problem with password reuse is that it creates a domino effect. If hackers breach one of your accounts, they can potentially access all your other online profiles in a cascading attack. This is why security professionals consistently rank password reuse among the most dangerous cybersecurity practices.
Password reuse transforms individual account breaches into company-wide security disasters. A single compromised social media login can give attackers access to email accounts, financial platforms, and business applications if you're using identical credentials across services.
You should always use different passwords for each account your business operates. This simple practice contains breaches to individual platforms rather than allowing them to spread throughout your entire digital presence.
Not Having Multiple Layers Of Protection
Think of bank security as a perfect example of layered protection. Banks typically have doors protecting the ATM area, another door securing the main banking floor, additional barriers protecting employee work areas, and massive vault doors protecting the actual money.
All of these represent security layers protecting the bank's most valuable assets. Your social media accounts should implement a similar system with multiple security barriers protecting your online presence from various attack vectors.
Most people skip these security layers, which creates poor overall protection and makes account takeovers inevitable. Single-layer security might stop casual attackers, but it won't withstand determined hackers who specialize in social media breaches.
Falling Victim To Phishing Attacks
Phishing is the most common attack method hackers use to steal login credentials from unsuspecting victims. This method tricks users into entering their usernames and passwords on fake websites that look identical to legitimate platforms.
Phishing attacks work because they exploit human psychology. Hackers create convincing replicas of login pages and use urgent messaging to pressure victims into acting without careful consideration.
As such, phishing awareness is one of the most important considerations when thinking about how to reduce your company's attack surface and protect valuable social media assets.
Not Protecting Local Devices
One common attack vector hackers use involves deploying malware to compromise devices like laptops, computers, and mobile phones. Once attackers gain device access, they can monitor your typing, steal stored passwords, and hijack social media sessions.
Keyloggers are a particularly dangerous threat because they record every keystroke on infected devices. When you type your social media passwords on compromised equipment, hackers receive copies of your credentials.
That's why protecting local devices from malware, keyloggers, and other compromising software is essential for maintaining social media security across your organization.
Not Having Active Protection For Their Social Media Accounts
Even when you implement every security best practice, sometimes you still get hacked due to unforeseen vulnerabilities or zero-day exploits. Platform-level breaches, social engineering attacks, or phishing campaigns can bypass traditional security measures.
When breaches happen despite your efforts, you need security systems monitoring your accounts to automatically remove unauthorized users and alert you to the compromise. Quick response times often determine whether a hack becomes a minor inconvenience or a major business crisis.
Most people lack this automated monitoring capability, which explains why they often struggle to regain account control after security incidents. Manual detection and response simply can't match the speed of automated systems.
What Can You Do To Protect Yourself?
Now that we understand why companies tend to get hacked, we also know exactly how to protect your business from these attack vectors. Here are six security measures that will dramatically reduce your vulnerability to social media breaches and help you maintain control over your online presence. Each recommendation addresses specific weaknesses that hackers routinely exploit to compromise business accounts.
1) Use A Strong, Complex Password
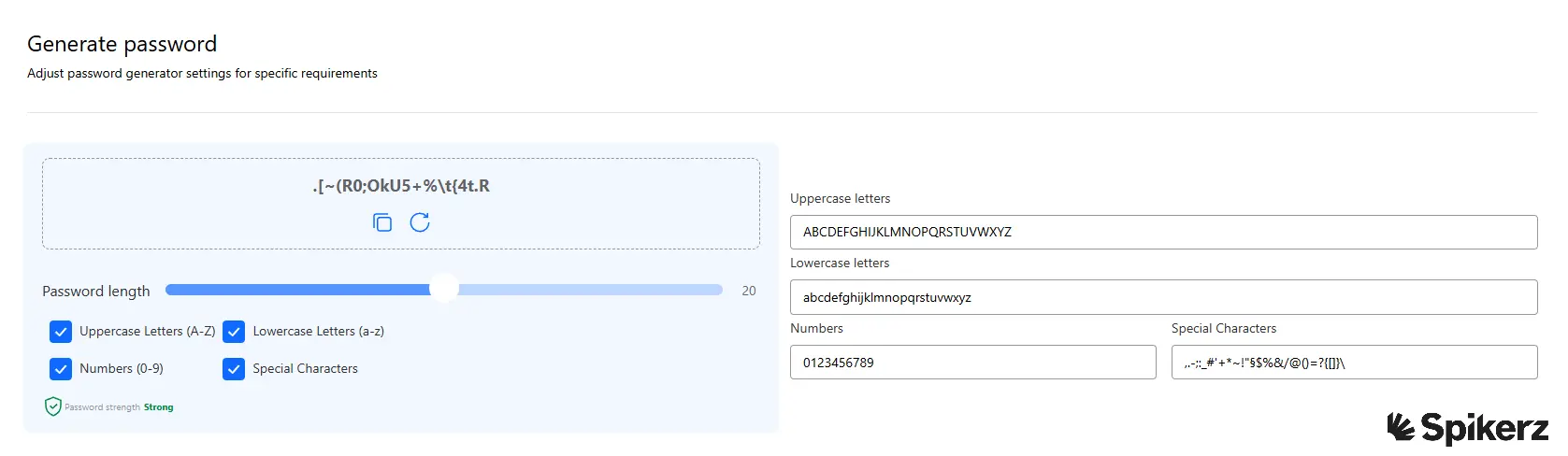
As we mentioned before, passwords serve as your first layer of defense against unauthorized access. They provide essential protection against brute force attacks that attempt to guess your credentials through automated testing.
To create strong passwords, make them at least 14 characters long and as random as possible. Use combinations of upper and lowercase letters, numbers, and special characters like symbols to maximize complexity. For example: HEx10eZaL$b#$j
Strong passwords force attackers to spend significantly more time and resources attempting to crack your credentials. This increased difficulty often causes hackers to abandon their attempts and target easier victims instead.
2) Always Use Different Passwords
Password reuse remains extremely common despite widespread awareness of its risks. A significant portion of internet users rely on identical passwords across multiple accounts, creating cascading vulnerabilities throughout their digital presence.
What worries us the most is that most users understand the dangers of password reuse, yet convenience often wins out over security. According to a Google survey, 65% of people reuse passwords across sites because they find it difficult to remember different combinations.
This creates a problem we encounter frequently in our security consultations. Businesses know they need better password practices but struggle with implementation. We recommend using password managers to solve this challenge. Password managers eliminate the memory burden and ensure every account receives unique, strong protection, making it practical for businesses of any size.
3) Use Two Factor Authentication
Two Factor Authentication is one of the most effective methods for preventing brute force attacks from succeeding. The good news is that most companies use 2FA on all business accounts. In a 2024 JumpCloud survey of over 1,000 SME IT professionals, 83% of respondents reported requiring employees to use MFA for accessing organizational resources.
That said, traditional 2FA works well for individual users, but companies need more sophisticated solutions for team environments. For example, 2FA for Teams like Spikerz provides better functionality for social media managers.
The main difference between individual and team-based 2FA is access management capabilities. Traditional 2FA only allows one person to receive security codes for account access, while team-based solutions grant multiple authorized team members secure access to verification codes from a centralized dashboard. You maintain complete visibility into who has access to each platform and can instantly revoke permissions when employees leave your organization.
4) Train Your Employees To Recognize Phishing Attacks
We've emphasized this point repeatedly across our content, but people are the weakest security link in any organization. This vulnerability doesn't stem from employees actively trying to undermine security efforts, it’s just that there are many human factors that make people inherently unreliable in security contexts.
For example, tired employees who've been working long hours may not carefully examine suspicious messages. This fatigue can lead them to click dangerous links or provide sensitive information to attackers, resulting in account breaches that proper training could have prevented.
That's why employee training on recognizing phishing attacks is essential for maintaining organizational security. Your team needs the knowledge and the tools to identify and respond appropriately to these threats.
Regular training and testing help ensure your employees stay up to date on evolving attack patterns. Scheduled live testing also helps you identify which team members need additional support and training to strengthen your overall security posture. Ongoing education helps you pinpoint security weak spots and provide targeted assistance where needed most.
5) Use Antivirus Software To Protect Local Devices
Antivirus software provides essential protection for organizational devices against malware like keyloggers, compromised applications, and other local security risks that expand your attack surface.
This protection is critical because cybercriminals frequently direct victims to spoofed domains or convince them to install compromised applications specifically designed to steal personal information. These attacks often appear legitimate, making them difficult for users to identify without technical assistance.
Antivirus protection also works through browser extensions and local file monitoring systems. These tools analyze suspicious activity patterns in your web browsing and scan downloaded files for malicious code that could compromise your social media security.
6) Enable Social Media Account Monitoring
There are many types of social media monitoring that exist, but social media security tools offer the specific protection your business needs. These specialized platforms differ significantly from basic social listening or engagement tracking tools.
Social media security tools provide software and applications designed to protect accounts, data, and your overall online presence from cyber threats. They operate continuously, scanning accounts for compromise indicators like unusual login attempts, suspicious messages, or abnormal activity spikes.
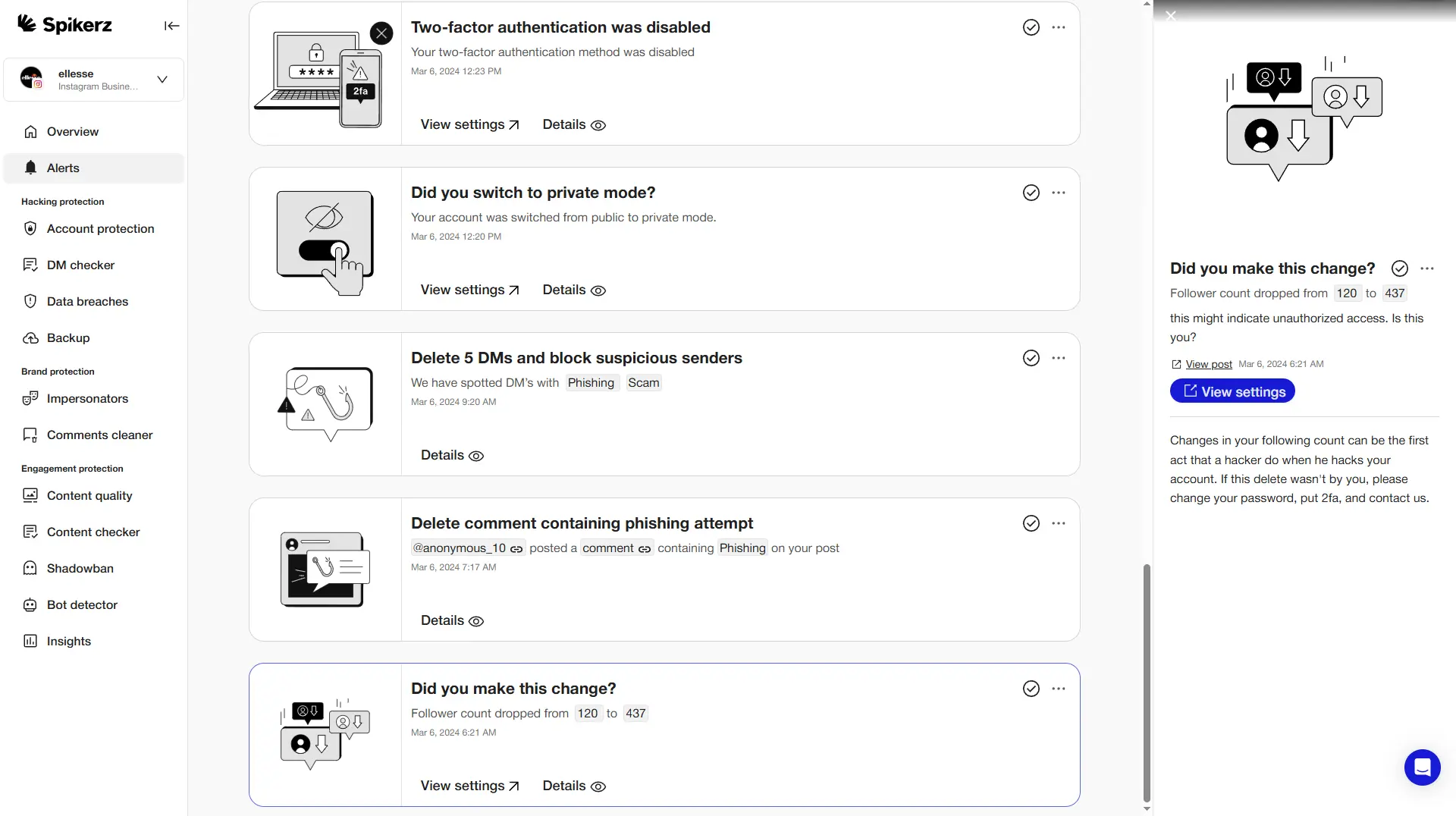
For example, Spikerz monitors your social media accounts for threats like login attempts from unrecognized locations, unusual login patterns, successful account breaches, and unauthorized permission changes.
Spikerz also improves your account health and security posture through key features like:
- Automatic intruder removal, password changes, and instant security alerts when breaches happen
- Automated backup systems to enable quick account recovery if problems arise
- Intelligent content filtering to detect and block spam, offensive language, and irrelevant content before it reaches your audience
- Content compliance analysis to ensure your posts meet platform policies and avoid account limitations or shadowbans
If you aren't already using social media security tools like Spikerz to protect your business accounts, you should start immediately. Preventing hacks costs significantly less and creates far less stress than dealing with account compromises after they happen.
Conclusion
Celebrity social media hacks like Jesse Williams' X account breach are a reminder that no organization is immune to hacking. What’s worse is that these attacks have evolved beyond simple financial crimes. Hackers now even target accounts for entertainment, making every business a potential victim regardless of size or industry.
Unfortunately, the security vulnerabilities that enable these breaches are common and preventable. Weak passwords, password reuse, insufficient authentication layers, phishing susceptibility, unprotected devices, and lack of active monitoring create the perfect conditions for account takeovers.
Your business can't afford to learn these lessons the hard way. Implement the six protection strategies we've outlined to create multiple layers of security that significantly reduce your vulnerability to these attacks. The investment in prevention will always be smaller than the cost of recovery from a successful breach.