Password Sharing for Teams: Secure Ways to Manage Social Media Access
Password Sharing for Teams: Secure Ways to Manage Social Media Access
Password management stands front and center of your social media security strategy. When you handle passwords correctly, you protect your accounts from hackers, prevent unauthorized access, and maintain control over your digital presence. Without proper password protocols, even the most sophisticated security measures become useless.
In this blog post, we'll go over how to educate your team about password security, create unbreakable passwords, implement two-factor authentication for teams, use password managers effectively, and establish role-based access controls to protect your social media accounts.
1) Educate Team Members On Password Security
Educating your team members helps you reduce the risk of data breaches, phishing attempts, and other malicious activities tied to infostealers. Proper training also lets employees take responsibility for their role in protecting company systems and sensitive data.
Additionally, security awareness helps employees understand the importance of established security measures and procedures. A lot of the time people don’t do everything they should because they don’t understand how their actions compromise them. When teammates are aware of potential threats and know how to respond appropriately, it creates a stronger and more resilient security culture within your organization.
A successful training program should include four core elements:
- Training
- Testing
- Communication
- Human security
It should be tailored to the specific needs of your business and you should test it regularly to assess if employees understood your security policies.
The training content should include topics like basic security principles, password management best practices, email security, social media safety, mobile device security, identity theft protection, and data privacy.
For example, they should be instructed to never share passwords or login credentials via text messages, instant messages, direct messages on social media, email, or internal messaging platforms like Slack.
The reason for that is because even trusted platforms can be compromised. In fact, a recent leak revealed that around 16 billion login credentials from major services like Apple, Facebook, and Google were exposed.
Training should help your team recognize and respond to social engineering attacks and other common cyber threats. The more familiar employees are with the tactics attackers use, the better they can protect themselves and your business.
2) Create Secure Passwords For Every Account
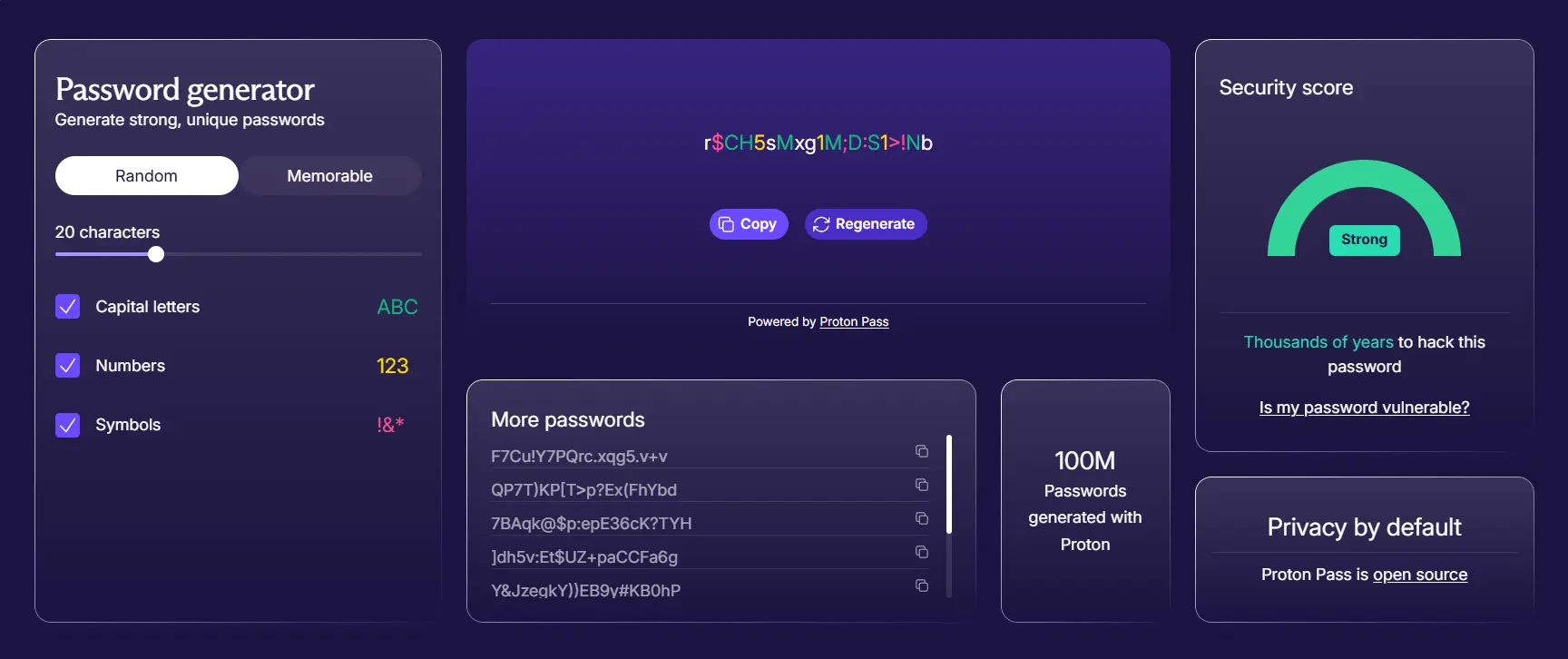
If your company manages multiple accounts, it's key for you to create strong, unique passwords for each one. Using the same password across different accounts or using weak ones can put your entire system at risk. If one account is compromised, all others that share the same password could be too.
Strong passwords help protect your systems and play a key role in preventing account takeovers. They ensure that only authorized people can access sensitive information, which is essential for maintaining operational security and customer trust.
Compliance is another crucial reason to enforce strong password practices. Many industries are subject to regulations that mandate strong password policies. If you don't adhere to these requirements you could face penalties.
Past compliance, you must also defend against common cyber threats, particularly brute force attacks. In these attacks, hackers use software to rapidly guess password combinations until they find the correct one. Simple passwords can be cracked in minutes.
That's why you must create passwords that are both complex and unpredictable. A strong password should be at least 14 characters long (20+ is much better) and include a mix of uppercase and lowercase letters, numbers, and symbols. It should also be random, not something basic. Avoid using dictionary words, personal information like birthdays, and don't rely on common patterns.
3) Enable Two-Factor Authentication (2FA) For Teams
Two-factor authentication (2FA) is a form of account security that complements traditional authentication methods.
Normally, you log in with just a password. But with 2FA, you need two different types of authentication to get in. That could be:
- Something you're like a fingerprint or face ID
- Something you know like your password or a security question
- Something you have like your smartphone or a security key
2FA uses two out of these three to grant access. For example, you might enter your password and then approve a prompt on your phone or enter a code sent to your email or generated on an authentication app. Using two of the same category, like a password and a security question, doesn't qualify as 2FA because it doesn't provide sufficient security.
2FA for teams is built on the same concept but is structured to work across multiple users instead of being tied to one individual's device. It's designed for businesses where people like social media managers, digital marketers, or community managers need access to shared accounts.
Instead of sending verification codes to a single phone, access is centrally managed. You decide who gets access, and when someone leaves the company or changes roles, you can revoke access immediately without disrupting the rest of the team.
For example, tools like Spikerz help manage 2FA for teams by managing account access and preventing takeovers. They also provide a centralized dashboard with alerts for threats like phishing attempts, scams, brand impersonation, or potential platform violations.
%20For%20Teams.webp)
These tools are more effective for marketing teams than platform-specific solutions like Meta Business Suite or TikTok Business Center because they protect multiple social media platforms at once.
Companies should also implement 2FA because people's passwords tend to be unreliable (they are too short, generic, and simple). Hackers use brute-force methods to try millions of combinations in seconds, which is a serious risk when employees use weak or reused passwords.
2FA prevents unauthorized access even if a password is compromised. Research from Google showed that device-based 2FA stopped 100% of automated bot attacks.
4) Use A Secure Password Manager
A password manager is a software program that generates, stores, and autofills passwords in a secure digital vault protected by a single master password. It allows you to access your credentials easily without having to remember multiple logins.
Password managers are an effective way to get rid of insecure habits like writing down passwords or sharing them over mail. And they reduce the chances of data breaches caused by weak or stolen credentials.
That's supported by the Verizon Data Breach Investigations Report, which shows that 81% of hacking-related breaches succeeded through stolen passwords or weak passwords.
A big part of the problem comes from everyday behavior at work. It's common for employees to reuse passwords across multiple accounts or share credentials with coworkers to save time or to avoid the hassle of remembering them all, which after a while creates serious security gaps.
That's where password managers make a difference. They generate strong, unique passwords for each account and store them securely with end-to-end encryption. Then, access to your passwords is only given through your master password, which is the only one you need to remember.
That said, password managers do more than just store passwords. They eliminate unsafe sharing practices like sending passwords over text messages, emails, spreadsheets, or chat apps like Microsoft Teams. When you use these methods you leave your credentials exposed. Using a password manager can help you share your passwords through encrypted channels and revoke access when you need it.
Lastly, for IT and security teams, password managers offer visibility into password health across the organization. They monitor password strength across your company and flag reused or weak credentials.
5) Use Role-Based Access Control
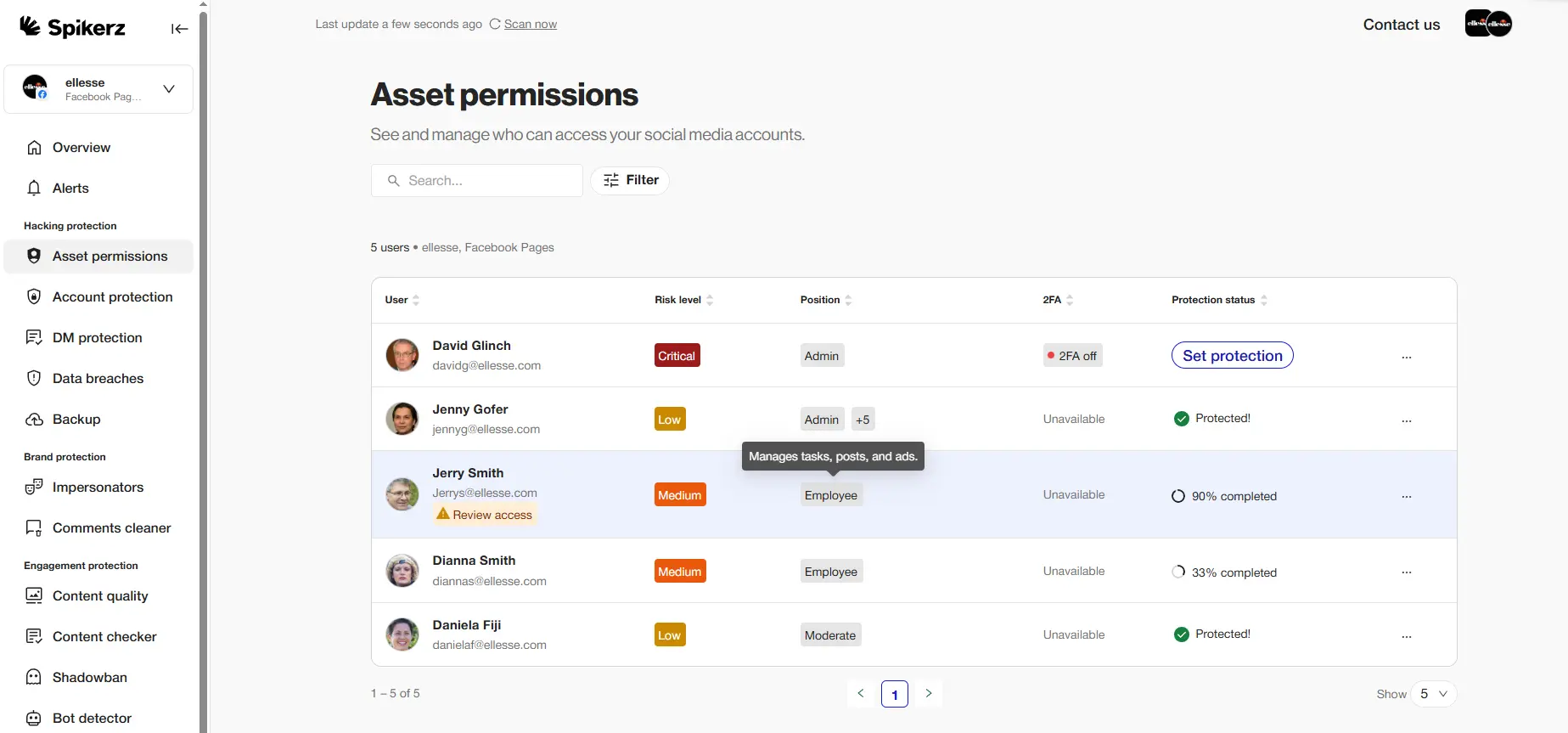
Role-Based Access Control (RBAC) is a security framework that assigns you permissions based on your role within your organization. Instead of assigning permissions to individual users, RBAC groups users into predefined roles, each of them associated with specific permissions tailored to that job function.
For example, a manager may have access to team reports and performance dashboards but a regular employee can only have access to their personal data and assigned tasks. Ensuring users interact only with the systems and resources relevant to their responsibilities to minimize the risk of unauthorized access.
RBAC is used in industries like IT, finance, healthcare, and anywhere sensitive data needs strict control. It's especially effective in environments where roles are consistent and predictable.
Here are some of the main advantages of using RBAC:
- New employees can be onboarded faster since roles already have the necessary permissions.
- User access changes are easier to implement by switching roles instead of editing individual permissions.
- Managing access is more efficient and less susceptible to error.
- It reduces delays in daily operations that are caused by manual permission setups.
- Access activity is well-documented, which helps with audits and meeting regulatory requirements like HIPAA, GDPR, and SOC 2.
- As the company grows, it's simpler to add users and roles without the need to sacrifice security.
- RBAC offers a structured, scalable, and secure way to manage access that improves security and operational efficiency.
Conclusion
Protecting your social media accounts takes more than just good intentions. It demands a systematic approach that combines education, technology, and ongoing vigilance.
Your team members are your first line of defense. When they understand security protocols and recognize threats, they turn from potential weak points into active defenders. Strong passwords and two-factor authentication create barriers that stop most attacks before they start. Password managers eliminate risky sharing practices and make security convenient. And role-based access control ensures people have exactly the permissions they need, nothing more, nothing less.
So take the time to implement what you learned here today. If you feel overwhelmed, start with one improvement. Your future self will thank you for it.