Social Media Security: How To Protect Your Social Media Accounts
Social Media Security: How To Protect Your Social Media Accounts
Social media account hijacking has exploded over the past two years, going from an occasional nuisance into one of the most critical threats businesses face online. Hackers now view social media accounts as high-value targets, launching attacks that can destroy years of brand building within hours.
That’s why this guide will show you exactly how to protect your accounts through practical security measures, team management strategies, and specialized tools that defend against modern threats.
What Is Social Media Security?
Social media security covers the practices and measures organizations take to protect their social media accounts, information, and privacy from unauthorized access and malicious activities.
These protective measures shield businesses from threats like hacking, phishing, malware, data breaches, identity theft, and the spread of misinformation. The goal is creating multiple barriers between your valuable accounts and the cybercriminals who want to exploit them.
How To Protect Your Social Media Accounts From Hackers
Businesses face three main types of unauthorized access threats: 1) external hackers seeking to steal data or damage reputations, 2) disgruntled former employees with insider knowledge, and 3) current employees who might accidentally compromise security through poor practices.
Each threat type requires specific defensive measures to prevent breaches. Here are some strategies that create overlapping layers of protection that significantly reduce your vulnerability to all three categories.
Tip #1: Create A Detailed Social Media Policy

A social media policy is a set of guidelines that outline how your business and employees should use social media responsibly. This document serves as your organization's roadmap for maintaining security and engaging online.
The security section of your social media policy should include rules covering multiple risk areas. It should establish standards for social media use across all devices - both business equipment and personal devices like smartphones and tablets that employees use to access work-related accounts or information. These standards should prevent activities that could expose corporate accounts, whether through direct access mixing or through personal account compromises that create pathways to business systems.
The policy should clearly specify which departments or team members are responsible for each social media account, and define account ownership to prevent both day-to-day confusion about access permissions and disputes when employees leave the organization. This protects both business interests and departing team members.
Technical requirements are just as important. Include requirements for strong passwords and regular updates, along with expectations for keeping software and devices up to date. Outdated systems create exploitable vulnerabilities.
Additionally, your policy should inform your employees how to respond appropriately to threats. Provide guidance on identifying scams and security risks, along with specific instructions on who to contact and how to respond when concerns arise.
Tip #2: Set Up An Approval Process
Setting up a content approval process ensures content quality, consistency, and alignment with organizational goals before publication. It essentially creates a quality gate that catches potential problems before they reach your audience.
A key step involves limiting the number of people who can access and post on your social accounts. This restriction maintains control over your content pipeline and reduces the number of potential access points for attackers.
Strong approval workflows combined with smart access controls help you build a more secure, consistent, and effective digital presence. They also establish clear roles and responsibilities for content creation and publication.
Tip #3: Create A Rapid Response Team (RRT)
.webp)
A Rapid Response Team (RRT) is a dedicated group within an organization tasked with managing and effectively responding to various types of incidents that require immediate action. These teams serve as your first line of defense when crises emerge.
RRTs can focus on different areas depending on organizational needs. Cybersecurity teams (often called CSIRTs - Security Incident Response Teams) handle security threats and data breaches, while others manage social media crises, public relations emergencies, and business disruptions.
In social media contexts specifically, an RRT predicts, plans for, and responds to events that could threaten an organization's online reputation or operational stability. They develop protocols for different crisis scenarios and train team members on rapid response procedures.
Organizations need social media RRTs because online crises can spread very fast and damage reputation permanently if not addressed immediately. A single negative post can reach thousands of people before traditional response teams even become aware of the problem.
A clear example of a missed opportunity is McDonald’s #McDStories X campaign. It started as a way for people to share positive customer stories. However, it was quickly hijacked by people who were sharing horror stories and customer support complaints. McDonald’s then failed to control the narrative and as a result, it turned into a PR nightmare that is still alive today.
Tip #4: Regularly Train Your Team On Cybersecurity
Threats targeting social media platforms change all the time, requiring organizations to continuously update their security measures to stay ahead of malicious actors. What worked six months ago might be ineffective against current attack methods.
That’s why it’s essential for businesses to train employees on cybersecurity. Many employees lack understanding of the security risks associated with using social media for business, creating vulnerabilities in organizational defenses. They might share too much information, click suspicious links, or use weak authentication practices that expose business accounts.
Regular, targeted training empowers employees to make smarter security decisions in their daily online interactions and recognize social engineering attempts. This education transforms your team from potential security weaknesses into active defenders of your digital assets.
Robust training programs strengthen the "human firewall". When everyone understands their role in maintaining security, the entire organization becomes more resilient against attacks.
Tip #5: Create Strong Passwords
Passwords are the first and most important layer of account defense. In many cases, a strong password is enough to protect them from breaches and takeovers.
The more intricate and unpredictable a password is, the harder it is for attackers to crack it, especially against brute-force attacks where automated systems attempt countless character combinations to break in.
To improve password security, use different passwords for different accounts, including your email account linked to social media. That way, if one account is compromised, others won't be at risk of cascade breaches.
Reusing passwords across multiple platforms dramatically increases the chances of widespread damage if just one of them is exposed in a breach. Cybercriminals often use stolen credentials from one breach to access other accounts in credential stuffing attacks.
The longer your password is, the better your protection becomes. Aim for at least 14 to 16 characters, as longer passwords take exponentially more time to crack using current technology.
Focus on length over complexity when possible. One useful trick involves using full sentences or memorable phrases like "breadandbutteryum." Some systems even allow spaces: "bread and butter yum."
To further increase strength, include a mix of uppercase and lowercase letters, numbers, and special characters. A more secure version might be: "Br3@d & butt3r YUM!"
That said, unpredictability is key to password strength. Avoid using single words or personal details like birthdays, pet names, or anything that could be easily guessed through social media research.
Tip #6: Manage Your Passwords Effectively
As a best practice, change the passwords to your social media accounts quarterly or immediately if there's any suspicious activity like a security alert or when a social media manager leaves their role or the organization. Regular password rotation limits the window of vulnerability.
Also, password security starts with keeping them confidential. Never reveal your passwords to anyone outside the social media team, including the IT department. If someone asks for your password, assume it's a scam attempt.
Additionally, team members should store passwords securely and never write them down or leave them exposed. A smart approach involves using a password manager to generate and securely store strong, unique passwords for each account.
Password managers streamline the login process, making it easier and safer to manage multiple social media profiles without compromising security. They eliminate the human tendency to create weak, memorable passwords or reuse credentials across platforms.
Tip #7: Use Two-Factor Authentication For Teams
Organizations should mandate the use of two-factor authentication (2FA) for their teams. This requirement creates an additional barrier that significantly reduces successful attack rates.
Microsoft reports that enabling multi-factor authentication can prevent 99.9% of account-based attacks. However, while traditional 2FA methods like receiving a code via SMS or using an authenticator app work well for individual users, they fall short when multiple people need to access the same account.
That's where team-based 2FA comes in. 2FA for teams is designed for shared environments, letting multiple trusted users securely log in to the same account without compromising security or disrupting workflows.
While there are many solutions available, we recommend you check Spikerz 2FA for Teams. Spikerz was built for collaborative environments like social media management, making shared access safe and seamless.
Here's how Spikerz sets itself apart from traditional authentication methods.
- Centralized access management: It integrates with your social media accounts so only authorized team members can access.
- AI-powered threat detection: It blocks phishing attempts in real time—before they ever reach your team.
- Device-free authentication: It uses browser-based 2FA, removing the need for a dedicated device.
- Simultaneous multi-device access: It allows multiple team members to work from different devices at once—perfect for managing posts, comments, or analytics in real time.
Stop leaving your social media accounts vulnerable to hackers. If you aren't using professional-grade security like Spikerz 2FA for Teams, you're gambling with your business reputation every single day. Protect what you've built—secure your accounts now before it's too late.
Tip #8: Set Up A Prevention System With Social Media Security Tools
Social media security tools cover a wide range of software, applications, and strategies designed to protect accounts, data, and your overall online presence from threats. These specialized solutions address vulnerabilities that standard platform security can’t cover.
They operate by continuously scanning accounts for signs of compromise, like unusual login attempts, suspicious messages, or abnormal spikes in activity. This constant monitoring provides early warning systems that can prevent small security incidents from becoming major breaches.
They often use AI to detect phishing attempts, malicious links, and bot-generated content. Some tools integrate directly with social platforms to monitor for threats in real time, while others offer layered protection through features like encrypted login management, malware detection, and automated response workflows.
One example of a social media security tool is Spikerz, an all-in-one security platform for businesses and individuals.
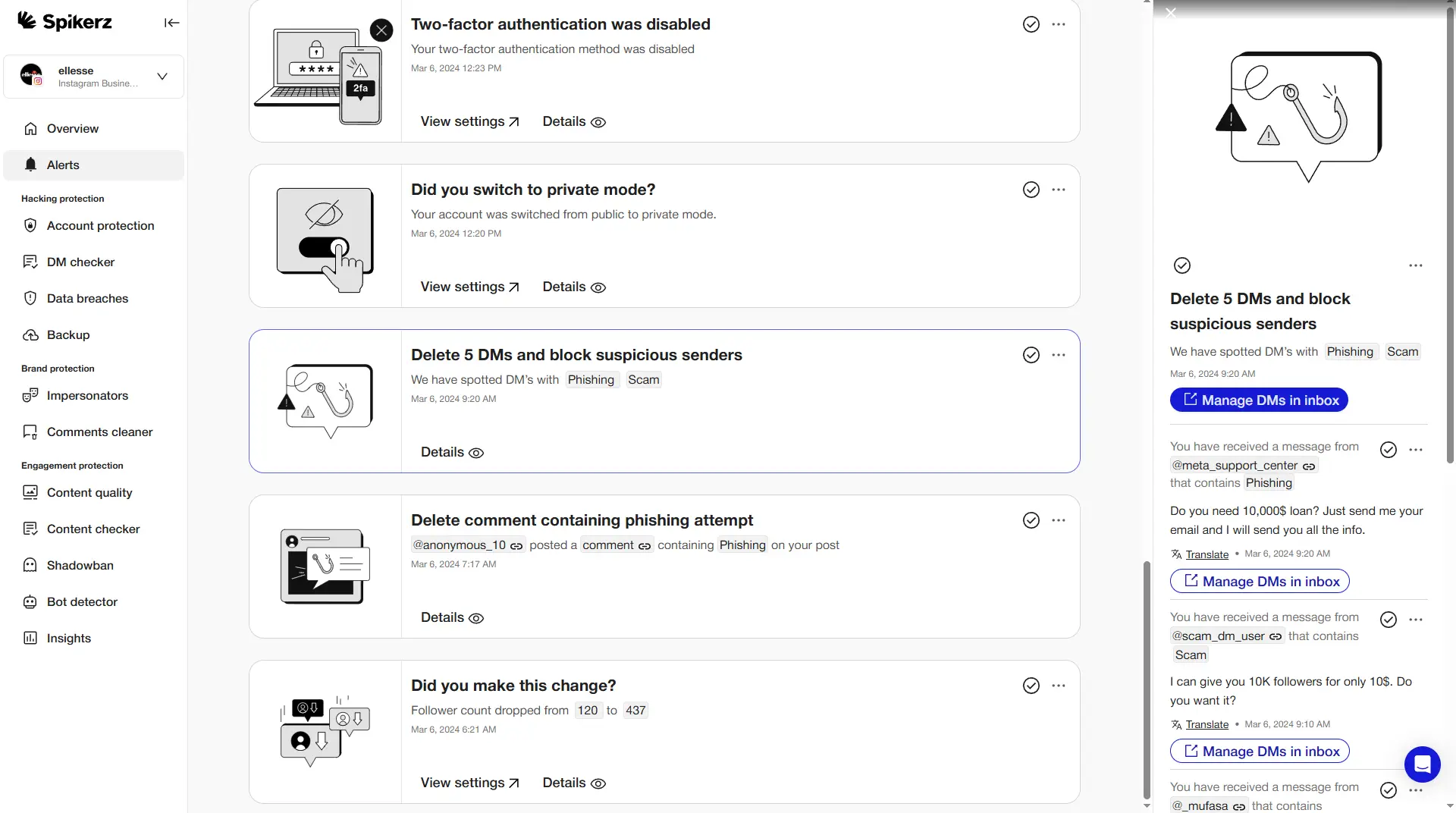
Spikerz offers specialized protection that goes far beyond what social media platforms provide natively. For example:
- Spikerz offers 24/7 monitoring to detect hacking attempts, bot attacks, spam, impersonators, and even risks like shadowbanning.
- It provides automatic backups to help you quickly recover your accounts if something goes wrong.
- It offers intelligent filters to detect and block spam, offensive language, and irrelevant content before it ever reaches your feed.
- It includes a free chatbot for account recovery, giving businesses a no-cost, no-hassle way to regain access.
- It provides peace of mind to anyone managing their social media presence by ensuring that accounts are protected by a robust, reliable system.
- It handles security monitoring automatically, allowing business owners to focus on growth rather than threats.
If you're not using social media protection like Spikerz, you're playing Russian roulette with your digital presence. Take control today before cybercriminals make that decision for you.
Tip #9: Go Over Your Social Network Privacy And Security Settings
Organizations should regularly review and adjust their social media privacy and security settings to protect sensitive data, maintain brand reputation, and comply with regulations.
It's essential to ensure that you and your team fully understand each platform you use. Social media companies routinely update their privacy and security settings. For example, X disabled two-factor authentication via text message for non-premium users in March 2023. In April 2024, the platform rolled out Passkeys as a login option for all iOS users worldwide.
Tip #10: Regularly Review Your Current Social Media Security Standing
Organizations that use social media should regularly assess their social media security standing to identify vulnerabilities, stay ahead of emerging threats, and ensure a strong defense against account takeovers, impersonation, and data breaches.
Regular reviews including vulnerability assessments, platform audits, and permission checks can uncover weak spots in how social accounts are managed. If weaknesses are left unaddressed, they can be exploited by attackers to steal data and content, or impersonate your brand.
Conclusion
Social media security isn't optional anymore—it's essential. The explosion of account hijacking over the past few years has transformed social media from a marketing opportunity into a critical security challenge that demands immediate attention.
However, if you implement the ten strategies we shared above, you’ll have a strong security posture that will protect you for years to come. Each strategy creates overlapping layers of protection that significantly reduce your vulnerability to hackers, disgruntled employees, and accidental security breaches.
So, what are you waiting for? Start implementing them right now to fully safeguard your online presence.



