What Is A Social Media Scam? How Do They Work?
Scammers excel at social engineering, manipulating employees into revealing confidential information or taking actions that compromise security. They study human psychology and exploit our natural tendencies to trust, help others, and respond to authority.
That's why we should be mindful of social media scams and how they work. Understanding these threats protects not just your personal accounts, but your entire organization from potential breaches.
In this post, we'll explore what social media scams are, how they operate, who falls victim to them, and most importantly, how you can identify and prevent these attacks from targeting your business.
What Are Social Media Scams?
Social media scams are fraudulent activities that happen when someone uses social media to try and manipulate you into giving them money or handing over personal information that you wouldn't normally share with others. These attacks specifically target the trust and connectivity that make social platforms valuable for businesses and people.
Scammers create fake profiles, impersonate trusted contacts, or hijack legitimate accounts to appear credible. They exploit the casual, friendly nature of social media interactions to lower your guard and make malicious requests seem routine.
These attacks can range from simple money requests to advanced phishing campaigns designed to steal corporate credentials. The big problem is that the interconnected nature of social networks means that a single successful scam can quickly spread to impact your entire business network.
How Do Social Media Scams Work?
Social media scams work because scammers exploit people's trust and they use psychology against them. Here's how they do it:
Make Small Requests
Scammers start with small requests to create psychological investment so victims are more likely to comply with larger demands later. A clear example of this is when someone asks you to do simple tasks like reacting to social media posts to get small commissions and then later they invite you to engage in more "rewarding" tasks to get larger commissions.
Pretend To Be Experts
Another tactic they use is they present themselves as experts to build credibility and trust with their victims. Also, they act helpful to make them feel indebted to "repay" those favors. This approach works particularly well in professional networks where expertise and helpful connections are valued.
Showing Concern
Scammers act as if they're concerned about their victim, they compliment them, and say they have the same interests to create a bond. This emotional manipulation makes victims feel understood and appreciated, lowering their defenses against fraudulent requests.
Showing Social Proof
Scammers pretend that others are already participating in the exciting activities they are talking about to make them seem normal and legitimate so victims want to join in. For example, if someone adds you to a group chat about investment opportunities with some strangers, and they're all gushing positive feedback about earning big returns quickly.
Use Pressure Tactics
An important characteristic is that scammers pressure victims to act quickly, not giving them time to think or reconsider. If you see this, run. It's most likely a scam.
Who Can Fall Victim To Social Media Scams?
Anyone can fall prey to scams, even when you think you're too smart to become a victim. If you're not worried about scams, you should be, especially now that technology has advanced so much, it's harder than ever to detect them.
The reason why so many people underestimate their vulnerability is a false sense of security. There's this mindset that because we're all so connected and have been using the internet for years, we can spot scams in the blink of an eye, which couldn't be further from the truth. Digital natives often feel particularly confident in their ability to navigate online threats, yet they frequently fall victim to social engineering tactics.
The comfort we feel navigating online spaces actually makes us more vulnerable to scams. When we're relaxed and engaged in social interactions, we're less likely to scrutinize every message or link for potential threats.
Another factor is stereotyping. Some people believe they don't fit the typical victim profile because of the misconception that only elderly people fall for scams. This assumption creates dangerous blind spots that scammers actively exploit.
The reality is that scammers target human psychology, not demographics. They exploit our emotions and desires, which means anyone, regardless of age, education, or tech-savviness can become a victim.
How To Identify Social Media Scams
It's extremely important to know how to spot a scammer so you can protect yourself. Here are some red flags to keep an eye out:
Poor Grammar
Poor grammar and spelling are common in scam messages, so they're often a reliable warning sign. However, don't rely only on this indicator, as scammers are becoming more sophisticated in their communication.
New Profiles
Brand-new social media profiles with very few friends or little content should raise immediate suspicion. Legitimate users typically have established online histories and genuine connections.
Impersonating Profiles
If the profile belongs to someone you thought you were already friends with, then it could be a scammer using a duplicate account. Always verify through your existing contacts before engaging with potential duplicate accounts.
Getting Unsolicited Messages
Unsolicited messages with links (especially if you don't know who they came from) present significant security risks. Legitimate businesses rarely send unsolicited promotional messages through personal social media accounts.
Taking Conversations Off Social Media
If someone asks you to contact them via messaging app or other private channels don't do it, they're most likely trying to avoid platform oversight. This tactic removes the protective measures that social platforms have in place to detect and prevent fraudulent activity.
Receiving Messages From People You've Only Met Online
Especially if they urgently ask for money to deal with a personal emergency, should trigger immediate skepticism. Genuine emergencies rarely require immediate financial assistance from online acquaintances.
Getting Blackmailed
Receiving threats to share a private image of you unless you send them money, that's a scam and a form of extortion. Report these immediately to both the platform and law enforcement, as this constitutes criminal activity.
Receiving Investment DMs
Receiving DMs promising you attractive investment opportunities, partnerships, or a way to earn quick, easy money with little effort or risk represent classic scam tactics. Legitimate business opportunities require proper vetting, documentation, and realistic expectations about risk and returns.
How To Prevent Social Media Scams
There are a few effective ways to prevent social media scams. Here are the ones we’ve identified as the best for protecting your business and employees:
1) Verify The Identity Of People You Interact With Online
Always research the profiles of people you don't know that contact you to see if there are signs that could tell you if that person is trying to scam you. Check how long the account has been active, how many friends or followers they have and how much activity they have had online.
When there's no sign of history, details in their profiles, and they have few or no followers, then that could mean you're dealing with a fake profile. Legitimate users typically have consistent posting patterns, genuine interactions, and established connections within their networks.
Also, be wary if someone offers you a job via direct messages (DMs) and not via a professional networking site like LinkedIn. But even in sites like LinkedIn, there's a process for that. Don't give out your personal information to anyone. When real recruiters contact you to offer you a position, they would want to interview you on-site or remotely, ask you for references, etc.
Think about it, if an offer appears too good to be true, it probably is. Always do your research and make sure you're talking with good intentioned people.
2) Limit What Information You Share Publicly
Bad actors are all over social media looking for information they can use to commit fraud and scams. That's why you should be extremely careful about what you share on your profiles.
Scammers use multiple methods to gather personal information. They thoroughly examine your profile to learn about you from your bio, photos, videos, and any linked websites.
They also look for clues in your content about places you've visited, people you know, your travel plans, and if you've unknowingly shown personal information like your address, phone number, bank details, etc. Even seemingly innocent posts about your daily routine can provide valuable intelligence to potential attackers.
All of this information can be used to steal your identity, commit fraud in your name, or even target your friends, family, and co-workers. The interconnected nature of social networks unfortunately means that compromising one person can provide access to their entire professional and personal network.
3) Create Strong, Unique Passwords
Strong passwords protect your social media accounts from unauthorized access and they keep your personal information safe. Password security is the foundation of your overall account protection strategy.
The more complex the password, the safer your information will be from hackers. Simple passwords can be cracked in minutes using automated tools, while complex passwords can take years or decades to break.
Your passwords should include a combination of letters, numbers, and symbols to increase its complexity. Avoid using dictionary words, personal information, or predictable patterns that attackers can easily guess.
Sometimes, hackers use brute force methods to access your accounts and devices, so the longer and more complex your password is, the better. Long passwords take a long time to hack, ideally they should be at least 14 characters long.
If you are worried you'll forget your password, use a password manager. They help you create safe passwords and store them securely so you can access them whenever you need them.
4) Enable Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) improves your account security because it combines multiple forms of identification to access your account, so it's harder for bad actors to access it even if they know your password. This additional security layer significantly reduces your vulnerability to account takeover attacks.
MFA uses three common authentication methods to verify your identity: something you have (text message codes, authenticator apps), something you know (passwords, PINs), something you are (biometrics). The combination of these factors creates multiple barriers that attackers must overcome before they can do anything to your account.
Here are three wonderful reasons to enable MFA right now:
- MFA blocks approximately 99.9% of brute force attacks.
- It ensures regulatory compliance. In some industries like finance, healthcare, and government there are hefty fines and legal issues if you don't implement MFA.
- It protects against credential stuffing attacks because it requires each user to authenticate their identity with something they know and something they have. Even if your password appears in a data breach, MFA will prevent unauthorized access.
5) Monitor Your Direct Messages And Comments For Phishing Attempts
Social media accounts are common targets for scammers because of their reach. If they get access to them, they can steal your personal or business information, impersonate you or your brand, and scam your followers.
The main way attackers compromise accounts is through phishing. Phishing in DMs and comments are often personalized to seem to come from sources you can trust like friends, family, or legitimate businesses, making them more convincing than let's say a generic phishing email.
The way to protect yourself from these attacks is to monitor your DMs and comment sections regularly so you catch suspicious behavior early. It reduces the chances of accidentally engaging with harmful links or giving away sensitive information.
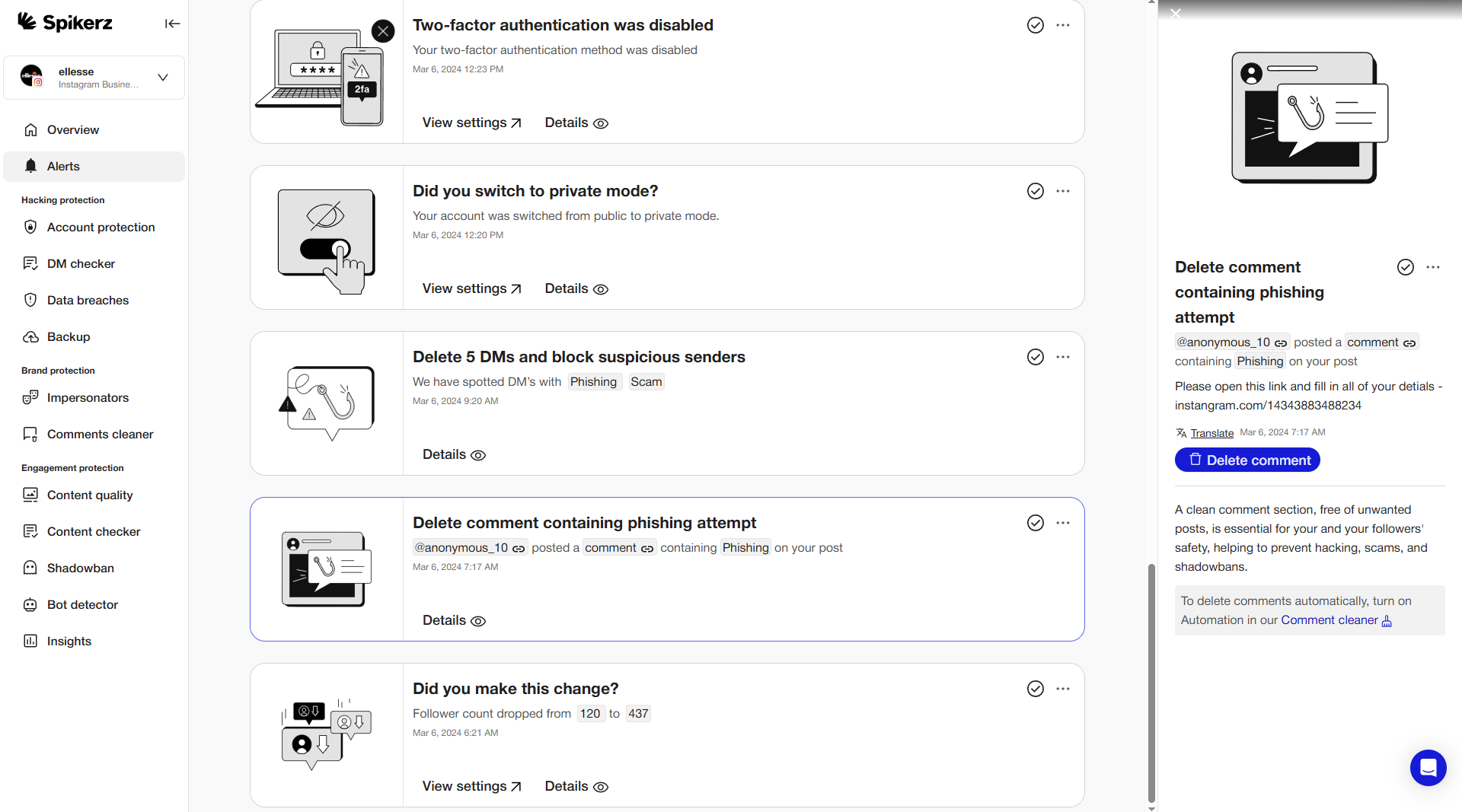
That's where a tool like Spikerz can help. Spikerz automatically scans your DMs and comments for phishing attempts, suspicious links and other online threats. It analyzes the content and context of messages and flags anything that looks suspicious. It also alerts you immediately when a risky message or comment is detected, so you can take action before something goes wrong.
In addition to threat detection, Spikerz gives you a clear overview of your security status and offers recommendations to keep your accounts safe. It supports multiple platforms, including TikTok, Instagram, Facebook, and YouTube, so you can manage everything in one place.
If this sounds like something that would benefit you, give Spikerz a try. We are sure you'll find it useful.
Conclusion
Social media scams are a growing threat to businesses and individuals alike, exploiting our natural tendency to trust and connect with others online. These attacks have evolved far beyond simple requests for money, they now involve psychological manipulation designed to extract sensitive information and compromise entire organizations.
However, understanding how scammers operate gives us the power to protect ourselves and our business. They rely on urgency, false expertise, emotional manipulation, and social proof to bypass your natural skepticism.
The most effective way to defend against these threats combines active monitoring with practical security measures. For example, verifying identities before sharing information, limiting what you post publicly, using strong passwords with multi-factor authentication, and monitoring your communications for suspicious activity with a tool like Spikerz to have an additional layer of protection that automatically detects and blocks threats before they can cause damage.

