5 Ways Hackers Target Facebook Comments (And How to Stop Them)
5 Ways Hackers Target Facebook Comments (And How to Stop Them)
Your Facebook business page serves as your digital storefront. It's where you connect with customers, share company news, and build your brand. But lurking within those seemingly innocent comment sections are cybercriminals waiting to strike.
Facebook comments present a perfect opportunity for hackers. They use these spaces to distribute malware, gather personal information, and create targeted attacks against your business and followers. Many organizations focus on securing their main accounts while overlooking the vulnerabilities in their comment sections.
In this post, we'll cover five common tactics hackers use in Facebook comments and provide an actionable strategy to protect your business from these threats.
1) Phishing Through Comments

Phishing attacks have evolved far beyond basic email scams. Now, cybercriminals use Facebook comments as launching pads for sophisticated attacks that target your business and customers.
Hackers create fake profiles mimicking trusted entities like "Facebook Support" to respond to legitimate customer questions on your posts. They establish credibility by offering seemingly helpful advice before directing users to fake login pages that steal credentials. These fake pages look nearly identical to genuine Facebook login screens, making them difficult to spot.
Another common tactic involves tagging multiple users in malicious comments to increase visibility and create a false sense of legitimacy. These comments often contain enticing offers like fake job listings for work-from-home positions. While initially appealing with promises of flexible hours and good pay, these scams ultimately request sensitive data like Social Security numbers under the pretext of "onboarding."
Hackers also hijack legitimate accounts to post malicious links in your comment section, leveraging the trust associated with those profiles. They'll craft references to other platforms with messages like "Check what I found on Instagram" to make users more likely to click external links. These scammers analyze public profile information to create personalized messages that appear trustworthy while concealing dangerous payloads.
2) Dangerous Links in Messages

Facebook Messenger provides hackers with a direct channel to target your business and employees through personalized communication that bypasses public scrutiny.
When customers or employees click links sent via Messenger, they may unknowingly trigger drive-by downloads that install malware without requiring any further action. These links often lead to fake websites or login pages designed to steal credentials and sensitive business data. The attackers frequently disguise malicious files as photos, videos, or documents to appear legitimate.
Social engineering tactics make these attacks particularly effective. Messages with urgent subject lines like "Look at this photo of you!" create immediate curiosity and prompt hasty actions. Initial links might lead to seemingly legitimate sites that later redirect to malicious pages or trigger secondary downloads.
The most dangerous aspect of these attacks is their chain-reaction nature. Once clicked, the malware accesses the victim's Messenger account to spread further through their contact list. This creates an expanding network of infections that can quickly spread throughout your organization. These attacks specifically target mobile devices, exploiting vulnerabilities in mobile browsers and apps that many security systems overlook.
3) Fake Images and AI-Generated Content
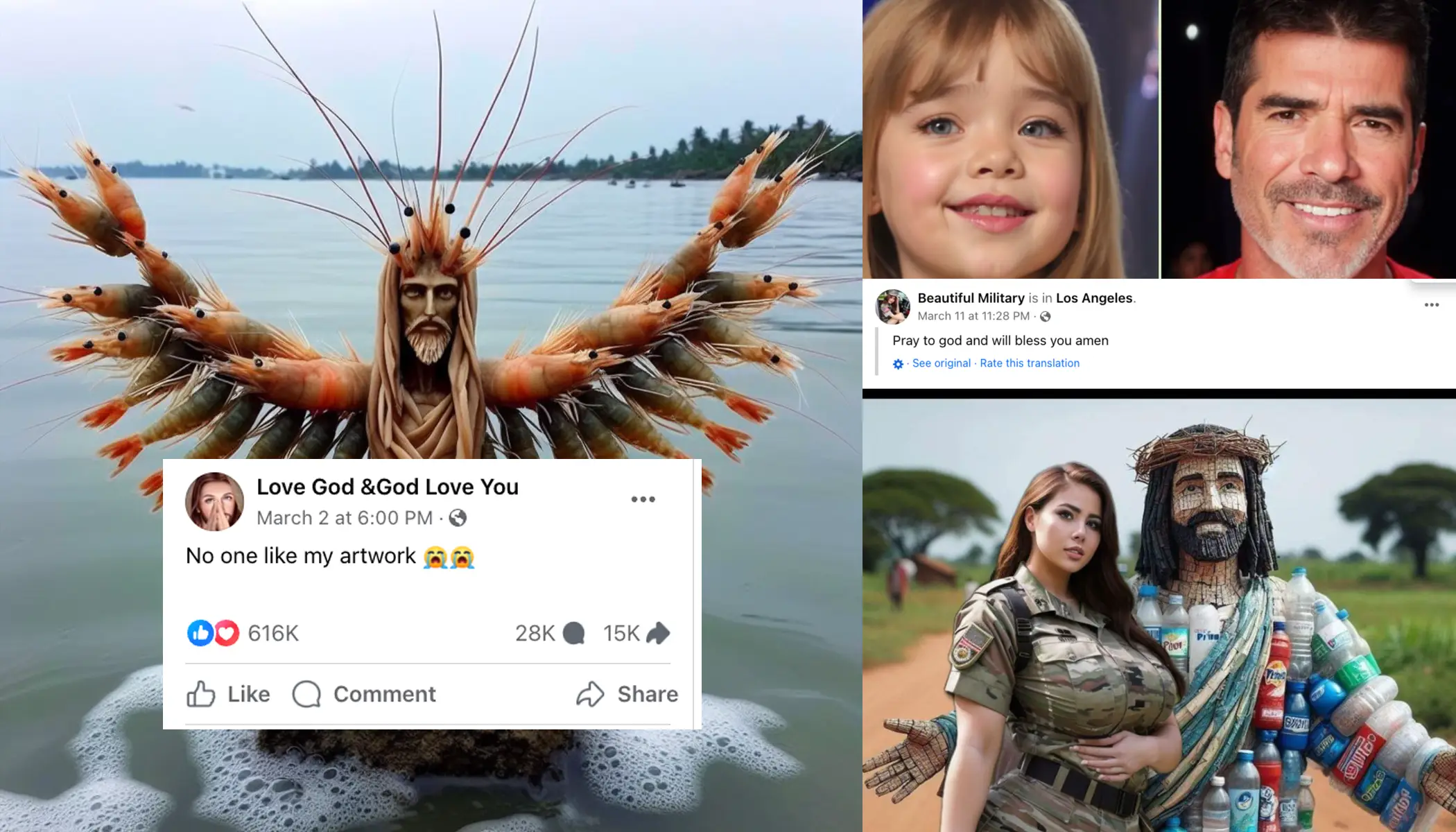
The rise of artificial intelligence has given hackers powerful new tools to create convincing fake images that distribute malware and trick people into revealing sensitive business information.
Cybercriminals employ several image-based attack strategies. They hide malicious code within legitimate-looking images that, when downloaded or opened, execute concealed malware in the background without any visible signs. These attackers also create convincing screenshots of sensitive information, such as banking details, to normalize the appearance of phishing sites targeting business accounts.
Another common tactic involves images labeled with innocent prompts like "click to view" or "download to see full image" that actually contain executable files with malware payloads. More sophisticated attacks combine fake images, AI impersonation, and traditional phishing tactics to create multi-layered threats that bypass standard security measures.
The severity of this threat is recognized by experts. The U.S. Department of Defense reports that cybersecurity professionals anticipate a long-term battle of "AI vs. AI" as both attackers and defenders leverage artificial intelligence. A 2024 survey reinforces this concern, revealing that approximately 36% of respondents believe online scams and phishing have become much more sophisticated due to AI integration.
As AI-driven threats grow more sophisticated, businesses must stay vigilant and adopt proactive security measures to stay ahead.
4) Creating Fake Profiles
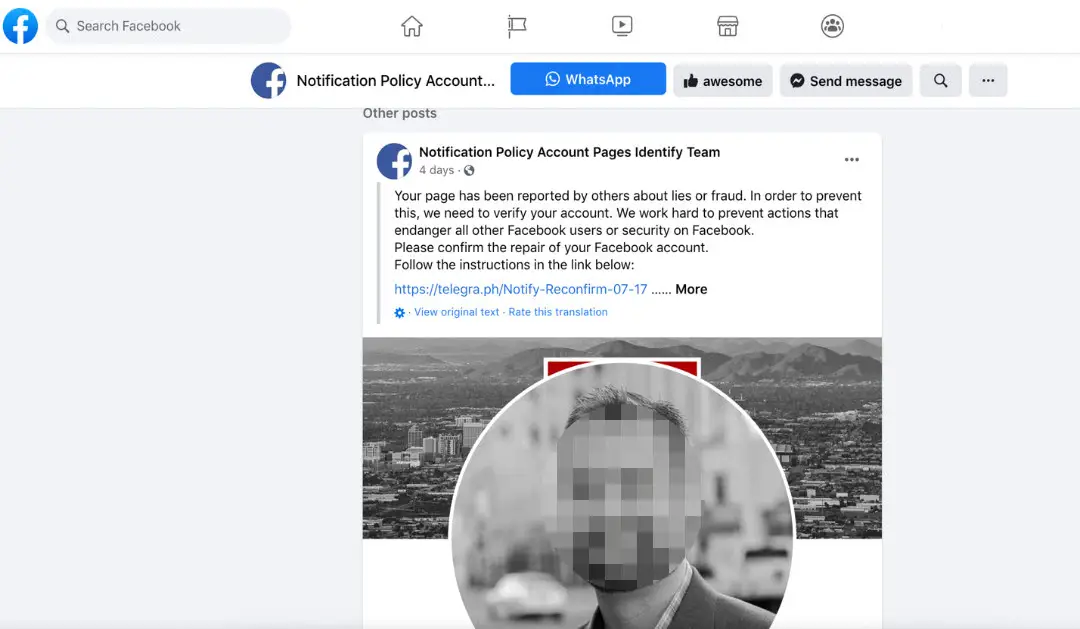
Fake profiles serve as powerful weapons in a hacker's arsenal, allowing them to infiltrate your business network and exploit trusted relationships with your employees and customers.
Cybercriminals create convincing fake profiles by stealing photos and basic information from real people's public accounts. They research potential victims to craft personalized approaches based on interests, work history, or connections. Hackers first build a network of connections and establish an activity history, this is to develop credibility before launching attacks.
Once established, these fake profiles distribute malware through various methods: sharing links to "photos" or "interesting articles," sending file attachments with embedded malicious code, or directing victims to fake websites. They often exploit known vulnerabilities in software or operating systems to install malware without user consent.
These technical attacks often work alongside social engineering tactics. Romance scams represent one of the most dangerous examples in personal contexts, where hackers develop emotional connections to manipulate victims. Once trust is established, these relationships can become gateways to business data when victims work for target organizations.
Attackers create urgent scenarios like “My bank account’s frozen” to persuade victims to share sensitive business information they have access to. Alternatively, they manipulate emotional connections to convince victims to provide personal financial data or make donations to fraudulent accounts. This dual approach allows cybercriminals to compromise both personal and business resources through a single compromised relationship.
The financial impact of these scams is substantial. The FTC reported that in 2022, nearly 70,000 people reported romance scams with losses hitting $1.3 billion. The median reported loss was $4,400, with gift cards being the most common payment method. These statistics highlight just the personal financial losses and don’t account for the potential business damages when corporate information is compromised. But it helps paint a picture of the significant damage they cause.
5) Targeting Friends and Connections

Hackers often use sophisticated methods to exploit the network of relationships surrounding your business accounts, turning trusted connections into unwitting attack vectors.
After compromising an account, hackers immediately target that person's friends list, sending malicious links that exploit established trust relationships. They analyze public friends lists to identify the most vulnerable connections first, working through networks systematically to maximize their reach.
These attacks use information visible on public profiles to craft personalized messages that appear legitimate. For example:
'Hey, I saw you were at the industry conference last week with Sarah - check out this photo of us at the booth!'
Such messages reference mutual connections and shared experiences to establish credibility, significantly increasing success rates. The inherent trust between business partners, employees, and customers makes these attacks particularly effective.
Once hackers gain access to your network, they gather personal data for identity theft or sell it on the dark web. They may also impersonate victims to ask friends or family for sensitive information or money. And damage not only your business reputation but also the trust between you and your customers.
How Can You Protect Yourself From Hackers?
Protecting your business from online threats requires a multi-layered approach that addresses both human and technical vulnerabilities. Start by being cautious with personal information. Review and limit the details you share publicly, regularly check privacy settings, and be selective about connection requests.
Implement vigilant practices like verifying unexpected links, confirming requests for personal information, keeping apps and devices updated, and removing sensitive content from posts.
Also, strong security practices should form your foundation: enable two-factor authentication (2FA), set up login notifications for new login attempts, review connected apps regularly to revoke access for unused services, and use a password manager to create complex, unique passwords for each account.
With that said, while these basic measures help, they're often insufficient against today's sophisticated threats. That’s why you should use social media security tools. Think of them like antivirus software but for your social media profile.
Dedicated social media security tools provide essential protection through:
- Real-time monitoring of login attempts and account access
- Detection of malicious links and phishing attempts in comments, messages and ads
- Tracking of unauthorized account setting changes and password reset attempts
- Identification of social engineering attempts and excessive permissions
- Implementation of multi-factor authentication and automatic account lockdown in case of a breach
- Detection of impersonation through fake accounts and mentions tracking
How Spikerz Helps Businesses And Content Creators Protect Their Profiles

Spikerz is a specialized social media security platform that provides complete protection beyond what native platform tools can offer.
While Facebook and other platforms provide basic keyword filters and moderation, Spikerz instantly removes spam and malicious content across multiple social platforms simultaneously.
The system analyzes user behavior patterns to identify repeat offenders, bot activity, and suspicious accounts, proactively detecting and removing harmful material before it reaches your audience.
Spikerz delivers comprehensive account protection by automatically backing up your content and safeguarding against unauthorized access through multi-layered security features including two-factor authentication for teams, dedicated contact methods, and automated password rotation.
The platform monitors your accounts in real-time, detecting leaked credentials and suspicious activities, while ensuring compliance with platform policies and managing team member permissions.
It also identifies and eliminates fake accounts attempting to impersonate your brand and alerts you to banned or risky hashtags that might trigger shadowbans.
For support, Spikerz offers guides, resources, blog articles, and chatbot assistance to help with account recovery.
Are You Ready To Improve Your Social Media Security?
Every day without proper protection is another opportunity for hackers to damage everything you've built. Why risk your brand's future when specialized protection is just a click away? Create a Spikerz account and take control of your social media security today.
Conclusion
Facebook comments present a significant but often overlooked security risk to your business. Hackers use these spaces to launch phishing attempts, distribute malware through dangerous links, deploy fake images with hidden code, create convincing fake profiles, and exploit trusted relationships within your network.
A single successful attack can damage your brand reputation, compromise sensitive data, and cost thousands in recovery efforts. Standard platform security measures simply aren't enough against today's online threats. Specialized protection like Spikerz provides the complete security your business deserves.



