What Is The Threat Intelligence Lifecycle?
What Is The Threat Intelligence Lifecycle?
Businesses face an unprecedented wave of cybersecurity threats. From phishing campaigns to advanced threats, attackers are becoming more creative and persistent in their methods. Traditional reactive security methods that respond to threats after they happen are no longer sufficient to protect your digital assets.
A proactive stance is essential for survival. Organizations must anticipate threats before they materialize, understand emerging attack patterns, and develop intelligence-driven defenses. This shift from reactive to proactive security requires a structured approach to managing threat information.
The threat intelligence lifecycle provides this framework. This systematic process transforms raw data into actionable insights that strengthen your security posture. In this blog post, we’ll explore what the threat intelligence lifecycle is, why it's critical for your organization, and how you can implement this framework to stay ahead of evolving threats.
What Is The Threat Intelligence Lifecycle?
The threat intelligence lifecycle is a structured process used in cybersecurity to manage and respond to cyber threats systematically. This framework guides the end-to-end flow of intelligence analysis—from gathering raw data to distributing actionable insights to key stakeholders across your organization.
The lifecycle helps organizations protect their information assets by continuously collecting, analyzing, and applying information about both current and emerging threats. Instead of operating in reactive mode, this process enables security teams to anticipate attacks and strengthen defenses before threats materialize.
Its goal is to improve the quality and relevance of threat intelligence over time, adapting to the constantly evolving cyber landscape. The framework creates a feedback loop that refines intelligence gathering and analysis based on real-world outcomes and stakeholder needs.
Why Is The Threat Intelligence Lifecycle Important?
The threat intelligence lifecycle provides a structured approach to gather, analyze, and use threat intelligence effectively. Without this framework, organizations often collect vast amounts of security data but struggle to transform it into actionable intelligence that supports decision-making.
This framework enables organizations to proactively defend against attacks, make informed security decisions, and respond more effectively to incidents. Rather than scrambling to understand threats during an active attack, teams have the intelligence needed to predict, prevent, and mitigate security incidents.
When following this lifecycle, organizations reduce their risk exposure, minimize the impact of successful attacks, and maintain a robust, adaptable cybersecurity posture that safeguards their information assets. This structured approach ensures intelligence efforts align with business priorities and deliver measurable security improvements.
The 6 Stages Of The Threat Intelligence Lifecycle
The threat intelligence process involves six connected stages that work together to transform raw data into actionable insights. Each stage builds upon the previous one, creating a continuous flow of intelligence that strengthens your organization's security posture. Understanding these stages helps you implement an effective program that delivers real value to your security operations.
That said, here are the six stages of the threat intelligence lifecycle:
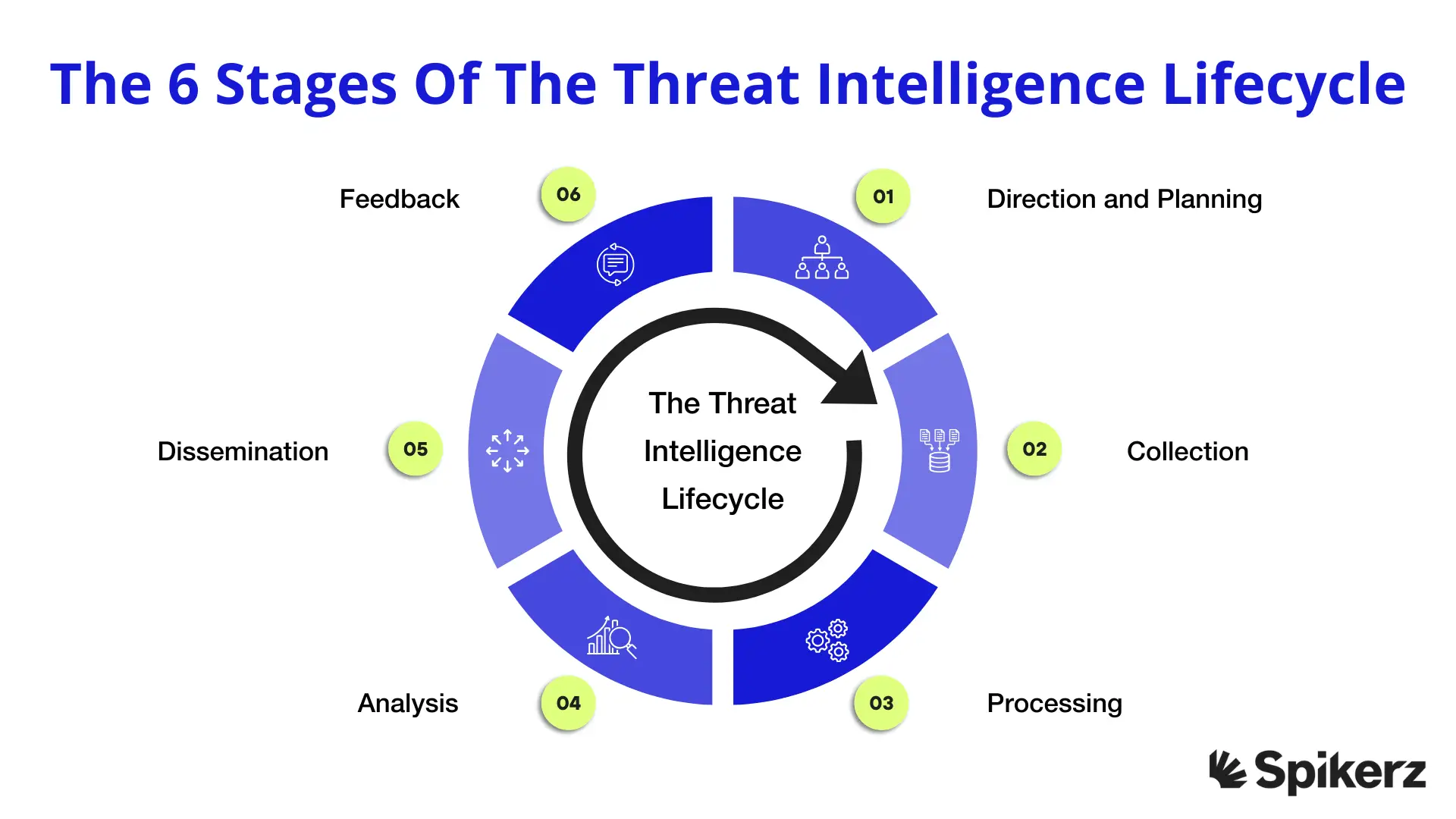
1) Direction And Planning
Planning starts the lifecycle by establishing the foundation for your entire threat intelligence program. Security teams collaborate with business stakeholders to define the program's objectives, goals, and scope based on organizational priorities and risk tolerance.
This stage often starts with determining what assets and data need protection, allocating resources and budget, and establishing key performance indicators (KPIs) to measure success. Teams identify critical business operations, sensitive information, and high-value targets that require protection from cyber threats.
Key objectives include identifying stakeholders who will receive intelligence, establishing communication channels, and defining intelligence requirements at both operational and strategic levels. Operational requirements focus on current threats and immediate defensive needs, while strategic requirements address long-term threat trends and future security planning.
Teams must also prioritize critical assets and identify gaps in current intelligence capabilities. This assessment reveals where additional resources, tools, or expertise are needed to support effective threat intelligence operations.
2) Collection
During the collection phase, organizations gather data and information from multiple sources identified during the planning phase. This stage involves systematic data gathering from multiple channels to create a complete view of the threat landscape affecting your organization.
These sources include internal logs, external threat feeds, open-source intelligence (OSINT), information sharing and analysis centers (ISACs), social media intelligence (SOCMINT), government agencies, industry groups, commercial vendors, and deep and dark web intelligence. Each source provides unique insights into different aspects of the threat environment.
That said, organizations will never be able to collect all available data due to resource constraints and access limitations. Geographic location significantly influences the operational environment through cultural, technical, and geopolitical factors, which determines available data sources and visible threat patterns.
For example, security firms collecting data from US customers will encounter different threats and intelligence than firms operating in other regions. Organizations collect a subset of available data, use a portion of that data to create information during processing, and transform a fraction of that information into actionable intelligence during analysis.
3) Processing
During the processing phase, raw collected data is transformed into structured information ready for analysis. This critical stage serves as the bridge between data collection and intelligence analysis, ensuring information quality and usability.
This stage involves organizing data through several key activities: cleaning to remove irrelevant or corrupted elements, normalizing formats for compatibility with storage systems, and verifying legitimacy and trustworthiness based on source credibility and corroborating evidence. These steps ensure data integrity before analysis begins.
Effective data processing is essential for quality intelligence outcomes. Poor data quality leads to flawed analysis and unreliable intelligence, ultimately producing insights that can't support sound security decisions.
4) Analysis
The analysis phase turns processed information into actionable intelligence that organizations can use to defend themselves and inform strategic decisions. This stage transforms raw information into meaningful insights that guide security operations and business decisions.
Human analysts apply their knowledge and experience to identify patterns and trends within the collected information, then interpret these findings to produce meaningful insights through cross-referencing multiple data sources and applying analytical techniques to understand context and implications.
Effective communication of intelligence is crucial for organizational impact. Intelligence must be presented in formats that decision-makers can readily understand and act upon, tailored to each audience's needs and technical background.
For example, reports for non-technical leadership should be concise (a one-page memo or a handful of slides), avoid confusing and overly technical terms and jargon, articulate issues in business terms like direct and indirect costs and impact on reputation, and include recommended courses of action.
5) Dissemination And Action
The dissemination phase involves sharing actionable intelligence with relevant stakeholders including internal decision-makers, operational teams, and external partners. This stage ensures intelligence reaches the right people at the right time in the right format.
For each recipient, you need to determine…
- What threat intelligence do they need, and how can external information support their activities?
- How should the intelligence be presented to make it easily understandable and actionable for that audience?
- How often should we provide updates and other information?
- Through what media should the intelligence be disseminated?
- How should we follow up if they have questions?
Effective dissemination ensures intelligence is actionable, relevant, and timely for each recipient. Security operations teams need specific indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) for threat hunting, while executive leadership requires strategic summaries focused on business impact and risk mitigation.
6) Feedback
The feedback phase involves gathering stakeholder input on the effectiveness and relevance of delivered threat intelligence to continuously improve the overall process. This stage closes the loop by evaluating intelligence quality and usefulness from the recipient's perspective.
This feedback is analyzed to identify process gaps, improvement opportunities, and ensure intelligence remains up to date and applicable to stakeholder needs. Regular assessment helps refine collection priorities, analysis methods, and dissemination approaches.
Insights from feedback enable refinement of the threat intelligence process, resulting in more targeted and valuable intelligence delivery. Also, you need regular feedback to understand the requirements of each stakeholder group and make adjustments as their requirements and priorities change.
Benefits Of The Threat Intelligence Lifecycle
The threat intelligence lifecycle enables organizations to defend against cyber threats through a strategic, efficient, and comprehensive approach to cybersecurity risk management.
Key benefits include:
- Early threat detection and response to minimize cyber attack impact,
- Strategic risk management through better understanding of the threat environment,
- Cost savings from proactive prevention instead of reactive damage control,
- Strengthens security resilience,
- Provides valuable incident response context,
- Enables development of tailored security solutions addressing specific vulnerabilities,
- Gain competitive advantages through effective threat management,
- Improve customer and partner confidence,
- And gain broader threat perspectives from diverse global intelligence sources.
Implementing The Lifecycle In Your Organization
The threat intelligence lifecycle is used by many organizations to structure their threat intelligence processes and improve security outcomes. However, the specifics of how to implement and use this framework depend on several organizational factors that determine the most effective approach for your unique environment.
You need to understand these implementation factors to help you adapt the framework to your specific needs and maximize its effectiveness. Successful implementation requires careful consideration of your organization's context, resources, and objectives.
Defining Intelligence Requirements
Defining intelligence requirements is important because it ensures your threat intelligence efforts are focused, relevant, and actionable. Without clear requirements, your team could waste time collecting and analyzing data that doesn't support decision-making or align with business goals.
To set intelligence requirements, you should:
- Align efforts with business priorities like protecting specific assets or complying with regulations,
- Guide data collection to focus on the most relevant threats,
- Enable efficient analysis by narrowing scope,
- And support timely and informed decisions for incident response, management, or strategic planning.
In short, defining intelligence requirements is the foundation for producing valuable, targeted threat intelligence.
Assessing Available Resources
Assessing available resources is important because it helps ensure your organization can realistically implement and sustain the threat intelligence lifecycle. Without understanding what tools, personnel, and budget are available, your intelligence efforts may fall short or become unsustainable.
To assess resources, you can:
- Identify gaps in skills, technology, or processes that need to be addressed,
- Set realistic goals based on what your team can actually support,
- Prioritize actions to maximize the impact of limited resources,
- Avoid overcommitting which can lead to burnout or ineffective operations,
- And make informed decisions about whether to build internal capabilities or outsource.
Resource assessment helps you build a practical and effective threat intelligence program that fits your organization's capacity, ensuring long-term success and sustainable operations.
Tailoring The Framework To Your Context
Tailoring the threat intelligence framework to your organization's context is important because every organization has unique risks, goals, and operational environments. A one-size-fits-all approach won't effectively address your specific threat landscape or business requirements.
To customize the framework, you can:
- Align intelligence efforts with your industry, size, and threat profile,
- Focus on protecting the most critical assets and operations,
- Ensure compatibility with existing tools, workflows, and team structures,
- Improve the relevance and usefulness of the intelligence produced,
- And adapt to regulatory, compliance, or business-specific requirements.
Tailoring the framework makes your threat intelligence lifecycle more efficient, actionable, and aligned with what actually matters to your organization, delivering better results with the same resources.
How Spikerz Can Help Protect Your Business From Threats
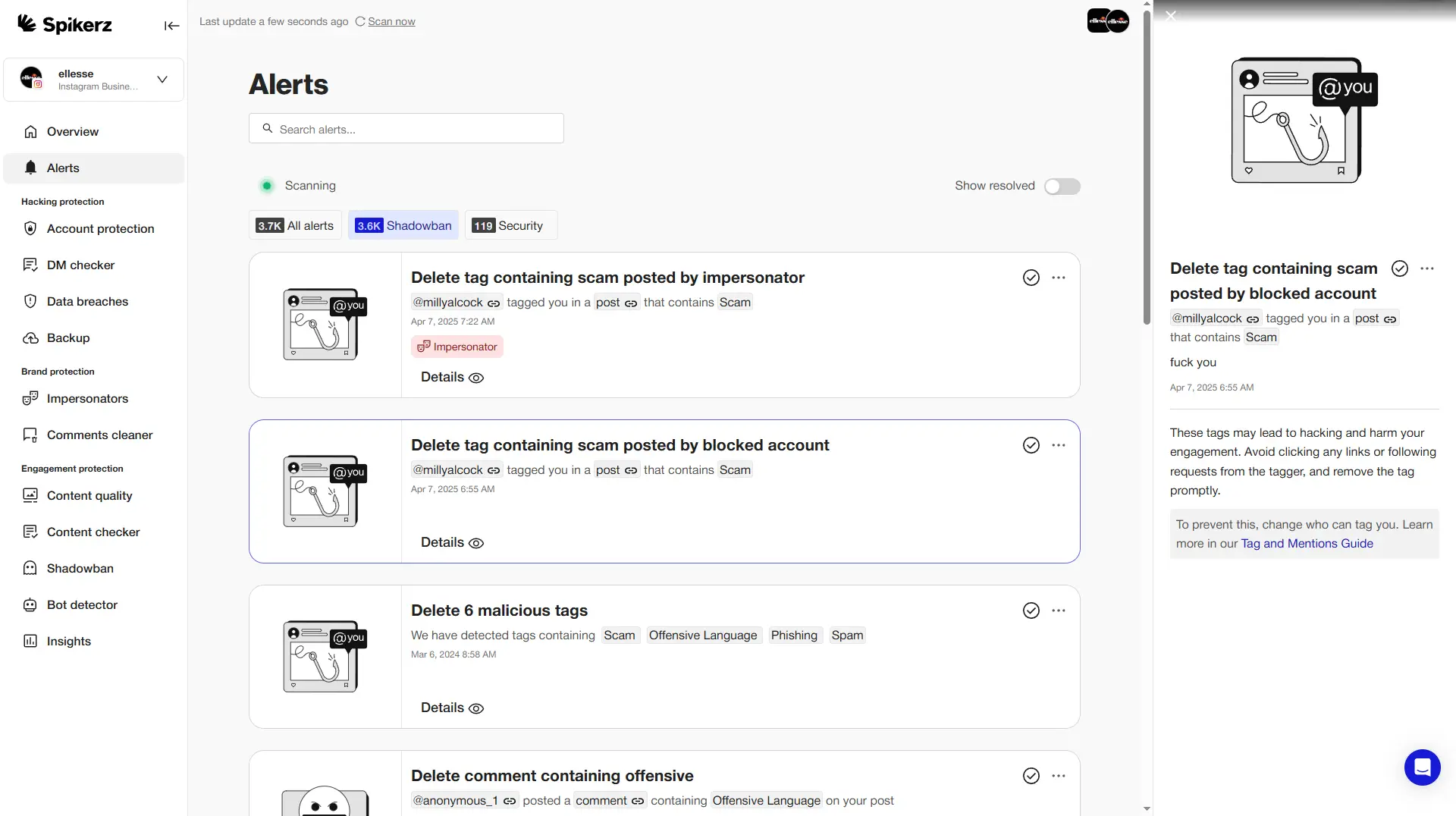
Spikerz is a cybersecurity platform designed to help businesses protect their digital assets from cyber threats targeting social media accounts. The platform focuses on detecting and mitigating malicious activity across social media channels where many organizations maintain significant digital presence.
Here’s how Spikerz helps protect your business:
- Spikerz continuously scans social media channels for suspicious activity including account takeovers, impersonation attempts, phishing links, and harmful content, enabling proactive threat response before escalation.
- Identifies fake accounts, copycat profiles, and unauthorized brand usage while flagging impersonators early to protect brand reputation and prevent social engineering attacks.
- When threats are detected, Spikerz provides immediate notifications and rapid response capabilities to minimize damage and restore account integrity.
- Tracks key health indicators like access controls, suspicious login behavior, and content policy violations, allowing organizations to address potential security liabilities proactively.
- It strengthens internal governance through multi-user access and role-based controls, ensuring only authorized personnel can respond to threats or make changes.
- It provides security measures like shared two-factor authentication (2FA), automated password rotation to reduce hijacking risks, and regular backups of social media data (including posts and comments) to ensure recovery following breaches or platform issues.
Are You Leaving Your Digital Assets Vulnerable While Competitors Strengthen Their Defenses?
Every day without specialized social media security is another opportunity for attackers to damage your brand, steal your content, or hijack your accounts. Take control of your social media security today with Spikerz—Your reputation is too valuable to leave unprotected.
Conclusion
The threat intelligence lifecycle provides a structured framework for transforming security data into actionable intelligence that strengthens your organization's defense capabilities.
Through the six stages of direction, collection, processing, analysis, dissemination, and feedback, organizations can proactively identify and respond to cyber threats before they cause significant damage.
Implementing this lifecycle requires careful consideration of your organization's unique requirements, available resources, and operational context. Success depends on tailoring the framework to your specific threat landscape while ensuring intelligence efforts align with business priorities and deliver measurable security improvements.
With that said, your organization's security posture directly impacts your ability to operate, grow, and maintain customer trust in an increasingly hostile cyber environment.
The threat intelligence lifecycle, combined with specialized tools like Spikerz for social media protection, creates a robust defense system that adapts to emerging threats and supports informed security decision-making across your organization.